- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Call For Papers
Your Expertise, Our Stage
The Great Exposure Reset
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Hybrid Mesh
- :
- SASE and Remote Access
- :
- Re: VPN Routing: Route all except for Internet tra...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
VPN Routing: Route all except for Internet traffic?
Hi,
we currently have a local Cluster of R77.30 Gateways with many VPN tunnels. We now want to install a bunch of centrally managed 1430 appliances in remote offices.
We normally use VPN Routing "To center, or through the center to other satellites, to internet and other VPN targets". The problem is that we want a local internet breakout on each remote office but need the "other VPN targets" from our local Cluster.
Is there a possibility to achieve this?
I appreciate your help
Marcel
28 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
--sk86582--
$FWDIR/lib/crypt.def
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I know about the crypt.def but I don't understand how I could solve my problem with it. Can I negate the destination IP so that only private IPs are sent through the tunnel? Would something like this work?:
vpn_exclude_dst!={<10.0.0.0,10.255.255.255>}Maybe you can help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you know how to get this working instead? I can't imagine that this is not possible.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It depends on a use case. The easiest way to set up VPN is to use simplified domain based option. I can only guess why you have decided to go for VPN routing instead.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To make things clear I made a quick picture:
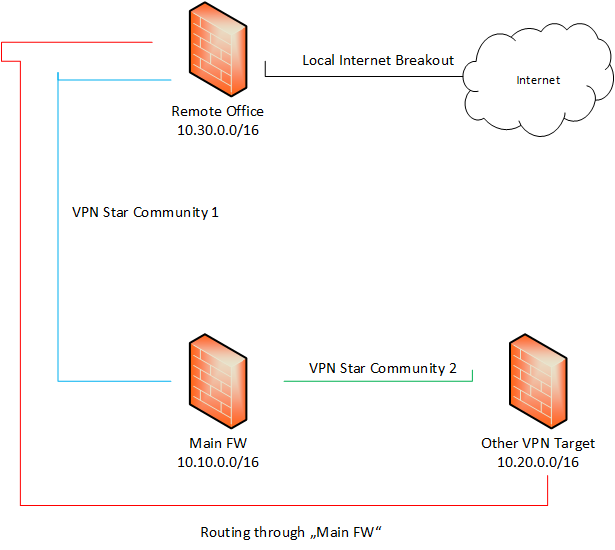
Short:
- Our main firewall has many VPN tunnels with other companys etc.
- Our remote offices have one VPN tunnel with our main firewall
- The remote offices have to access the other VPN tunnels through the main firewall
- The remote offices should use the local internet connections
Any idea?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
> - The remote offices should use the local internet connections
It is a standard S2S VPN setup. Use domain based VPN, it will work out of the box. If you need to route Site 1 to Site 2 through the main FW, there is an option under VPN Community / VPN Routing to do that.
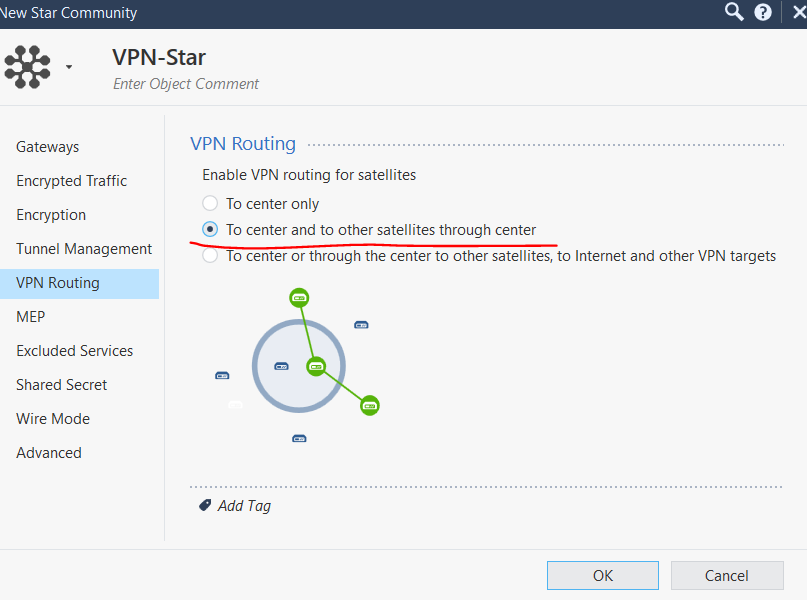
This is also written in the documentation, look into the admin guides
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Valeri,
does you proposal also cover this requirement ?
- The remote offices have to access the other VPN tunnels through the main firewall
If this explanation is correct confused-about-vpn-routing-options (which I believe), then your proposal will only work, if all satellites are in the same VPN community, which is not the case in Macrels setup. Or am I wrong ?
Matthias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's exactly my questions here. We normally have one community for a company - thats over 20 in total now. I tested again but it's not working. And I can't just put the remote office in the other community.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Marcel,
I believe it will work only with a combination of Route Based VPN (for your 1430 appliances) and the Domain Based VPNs which I guess you have for your already established VPN Communites.
A mix of both modes on a gateway is possible as per sk109340
But: on a R77.30 Gateway, a Route based VPN would disable CoreXL: CoreXL Known Limitations, an update to R80.x might be an option.
Routed based VPN is supported on a 1430 appliance: Route Based VPN on R77.20.xx Gaia Embedded appliances but it will also disable Core XL.
You would have to test it carefully of course.
Matthias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Matthias,
thanks for your help. That sounds like an option but a pretty complex one...if there is no easy way to achieve this we will route all traffic through our main firewall. It works even if it's not the ideal solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why do you want to route traffic between remote sites through the center? Why don't you just use a simple Mesh community and allow the sites to talk to each other directly?
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't want to connect the remote offices but everyone has to access other VPN connections that we don't manage. It's not possible to change the whole VPN contruct here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You over-complicate the issue. What you need is a single Star VPN community with your main cluster as center and remote offices are satellites. The second option, "to center and other satellites through enter" gives you what you need.
There is one caveat, not related to VPN. Make sure each of satellites has a different internal network IP range OR does unique NAT for internal addresses.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It would be nice if I over-complicate the issue but I don't think so. The main point is:
- The remote offices have to access the other VPN tunnels through the main firewall
Every remote office has to access e.g. the Google Cloud via VPN but the connection has to go through the main firewall. And I cannot build a complete new setup where I only have one community for all VPNs.
Your solution doesn't work because the remote offices wouldn't route traffic for the Google Cloud to the main firewall. I double tested this scenario.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Got it.
How is Google Cloud VPN configured on your main GW? If it is a community, you could enable directional VPN rules in your policy and do something like this:

You need to configure routing on the main GW that would make sure one tunnel cleart ext would go to another.
Did you consider such setup?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Valeri,
thank you for this option I never looked at. It quite nice in some other rules ![]()
But the problem still exists on the given setup. The problem is that the remote offices try to send traffic to e.g. the Google Cloud through the internet when the VPN routing isn't set to the third option. And if I do that everything is send through the tunnel.
Maybe I misunderstood you but the problem is still the same. And route based VPN is no option because of CoreXL etc.
Do you have any idea left? Maybe it's something that isn't possible no matter how long we think about it...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, how is Google Cloud VPN configured on your main cluster? Is it a community?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry, it's configured as a star community with our main cluster as center. VPN routing is set to the second option.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay.
Traffic between two communities can be routed with standard means. Since both communities: Google Cloud <-> Main Cluster & Main Cluster <-> Branch Offices are working, the only missing link is routing on the main cluster. Look into that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I too have just hit this exact scenario.
0. Started with a third party vpn with a center site with encryption domain with ALL networks. VPN traffic always routed thru center site over MPLS.
1. VPN community1 designed for MPLS backup. MPLSbackupcommunity works and all site are accessible via remote client thru center site. VPN option is set to second option.
2. Internet access goes out local firewall.
3. Second VPN community to third party. Third party community works and is accessible via remote remote client thru center site.
So I see two options:
1. Add all remote sites with firewalls to third party VPN. Not an easy to implement as third party was already defined with all remote sites. We do not have the ability to change the remote side of the third party vpn.
2. Set VPN option to third choice and route all internet AND VPN traffic thru center site. Bad choice due to the increased load on the internet connection on the center site.
The question remains how to do third option on VPN, but still allow internet access out the remote local firewall.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
when you have 2 Star topologies, 1 with all Check Point managed own gateways and one with a 3rd party VPN you will find that traffic from a CP satellite will be routed through the VPN to the center. The next VPN however does not accept your remotes' IP range when this has not been added to your 3rd party side as living behind your gateway.
In other words, your 3rd party needs to know about your satellites' networks or it will never accept traffic from them.
In other words, your 3rd party needs to know about your satellites' networks or it will never accept traffic from them.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is exactly why I specified 0 above. The third party already knows about all the remote sites and routes them back to the center site over the VPN. The encryption domain changed from center site networks + all remote site networks, to just center site networks.
Problem is how to get the remote sites to route their traffic to the center site over the vpn without routing internet traffic over the vpn.
We really need a 4th VPN option:
Allow traffic to center, other remote sites, and other VPN sites thru center gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Using option 2 you should see traffic for the 3rd party routed through the VPN.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
nope option 2 is for other remote sites thru center, NOT different vpn community. I had to re-read it closely myself.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you tried and checked the logs?
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes, which is why I am posting here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Marcel,
Did you get the resolution for the posted issue? I'm also facing the same issue with the local internet breakout requirement.
vpn_exclude_src1={<192.168.200.1,192.168.200.254>};
vpn_exclude_dst1={<0.0.0.0,0.0.0.0>};
#ifndef IPV6_FLAVOR
#define NON_VPN_TRAFFIC_RULES ((src1 in vpn_exclude_src) and (dst1 in vpn_exclude_dst))
#else
#define NON_VPN_TRAFFIC_RULES 0
#endif
Is this right condition to exclude the internet traffic for the 192.168.200.0/24 network from the VPN?
Thanks in advance!!
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 4 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Introducing Cyata, Securing the Agentic AI EraTue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Introducing Cyata, Securing the Agentic AI EraTue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


