- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Re: Technology Partner News: Okta MFA for Check Po...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
DeletedUser
Not applicable
2018-09-13
12:56 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Technology Partner News: Okta MFA for Check Point
Happy to say that Okta has an Okta-certified RADIUS app and posted the integration guide with Check Point on their website. A RADIUS integration is perhaps a small thing, but one thing notable about the integration is this authentication setting: Accept password and security token in the same login request. When MFA is required in the Okta policy and this is enabled, then a user must add a comma to the end of their password, followed by their second factor keyword (such as a One-Time-Password from their Okta Verify app).
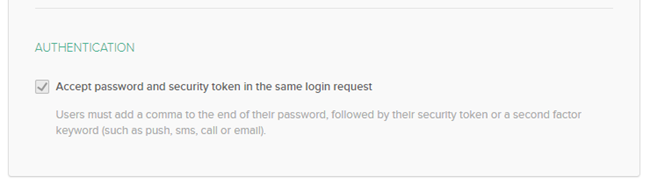
This is helpful in some Check Point cases where we don't support RADIUS access-challenge requests following the initial access-request to the RADIUS server. When there is an access-challenge, then our software needs to handle this in an interactive exchange with the user like in this example from our Remote Access VPN client.
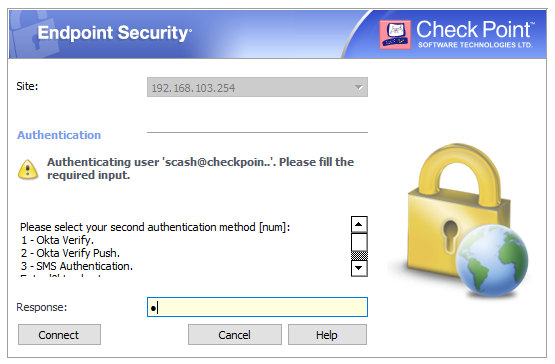
Not all of our clients support this.
| Client | Supports Challenge-Response |
|---|---|
| Remote Access | Yes |
| Mobile Access | Yes |
| Captive Portal | Yes, in R80.20 |
| SmartConsole | No |
| Gaia OS | No |
For those cases where you want MFA and our software doesn't currently support access-challenge, then this is a convenient way to do MFA via adding the second factor in the initial access-request to the RADIUS server.
- Tags:
- integration
- mfa
- okta
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Funny thing is I remember working with some folks at Okta on this some time ago.
Glad to see it's a formally supported/documented thing now ![]()
DeletedUser
Not applicable
2018-09-13
04:18 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Somehow I knew you had a hand in this 😉 Thanks Dameon.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Has anyone been able to get this to work? I'm struggling with it. Any help would be greatly appreciated.
DeletedUser
Not applicable
2019-01-29
01:02 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What problems are you running into? Anything unique about your configuration? thanks, bob
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just get unknown user in the CP logs with any credentials that I input. No
logs are generated on the Okta side unless I use an invalid user that is
not in Okta. Nothing unique as far as configuration.
DeletedUser
Not applicable
2019-01-29
01:27 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you see the access-request in a tcpdump from CHKP to the Okta RADIUS agent? What CHKP client are you trying to login with?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Interesting discovery with the tcpdump. If I use a user account that is
local to the check point user database I see the radius request and of
course that fails because its not in Okta. However if I use an Okta
username, I see an ldap request and no radius...Using Version VPN E80.82
endpoint client.
DeletedUser
Not applicable
2019-01-29
02:26 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That helps, so something in the CHKP configuration that needs to be tweaked. To be sure the CHKP-Okta piece works, you can always set RADIUS as the auth method in the user object where the user also exists in Okta. Not scalable, but some times nice to see something works 😉
To simplify things you may want to ignore RADIUS user group part of the Okta docs and check your External User Profile settings.
.............
6. Navigate to SECURITY POLICIES and select Access Control. This displays Access Tools VPN Communities. Click on VPN Communities. Double click to open the RemoteAccess community and add the gateway object.
7. Click Participant User Groups and accept the default All Users.
8. Click OK to save the settings.
9. The option to create an External User Profile (generic*) is only available using the legacy SmartConsole Client. To launch legacy SmartDashboard go under "Manage & Settings" and select the "Configure in SmartDashboard" for the Mobile Access option
10. In the lower left corner click on the Users object. Right click on External User profile and select New External User profile -> Match all users.
11. Click Authentication and select RADIIUS as the authentication scheme. Select the RADIUS server configured above, for example MyRADIUS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
9-11 has got me further...I'm seeing it hit Okta now, but for some reason
still fails. Checkpoint states radius servers not responding and okta
states authentication of user via radius: login failed. Not much detail.
Maybe I'll open a case with them and see what they have to say as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you remember what set of instructions you used for this. I am using the instructions from OKTA and it is just not working. Not getting a prompt for MFA on my vpn client
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Finally got it working. For the heck of it I decided to try changing the
radius secret and then it worked...Not sure if they have limitations on
characters or what, but I made it simpler. Thanks for your assistance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What about SandBlast Agent as the client? Do we support Okta/MFA for our Endpoint Security solution?
In summary, I'm trying to understand if our FDE blade would support preboot MFA without requesting the user for their credentials again for OS authentication. It doesn’t need to be Okta if we have any other MFA support for this purpose.
Any ideas will be much appreciated! 🙂
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter



