- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Re: Restriction on Remote Connections.
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Restriction on Remote Connections.
Hello,
Is it possible to restrict the origin of Remote Access VPN connections by country?
I have tried to "restrict" connections so that only 1 country can connect to my VPN.
I tried this from the firewall rule, using an "UPDATABLE OBJETC", but when I then try to work with other rules that I have, which are also RA VPN, I start to have errors in the installation of policies.
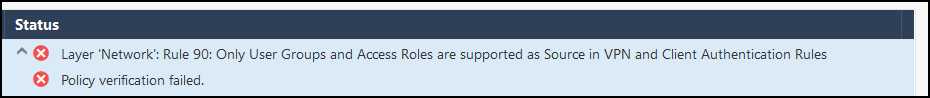
The rule 90 that I have, which is the one that causes me conflict, goes something like this:
Source: GRP_VPN@Any
Peru
Destination: Red_00
Community: RemoteAccess
Action: Accept
Services: Any
I am working with local users.
When I "delete" the "Update Object", I can install the policies without problems, but what I am trying to do is to make the access to my VPN connection more "restrictive".
Thank you for your attention.
22 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No bro, not possible. I even had case opened with TAC, went to escalation, they confirmed the same. Kind of sucks, because with Fortinet, its literally 4 clicks to get this done.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you get to share any SK?
Or were they just "cold" and said "No way, bye bye"?
hahaha 😞
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
LOL @Matlu ...no bro, there is no sk lol
Anyway, they just said in the case its not possible. Customer very disappointed, to say the least, but if it cant be done, cant be done. Maybe in R82, I dont know...
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You seem to have been "misunderstood".
LOL. It happens ... 🤣
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HAHAHAHAHA...it wont be first or last time bro 🤣🤣🤣🤣🤣
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You could try the following approach:
https://community.checkpoint.com/t5/Security-Gateways/Block-VPN-Traffic-by-Country/td-p/172695
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay, I will give that option to the customer, something to consider. Not as easy as setting it up on Fortigate gui, but at least it may work.
Thanks Chris,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Treats traffic, as if it were "DoS", can negatively impact on GW?
Can it cause CPU and Memory saturation of GWs?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats exactly thought I have as well...I really wish there was a way to block this in the rule using updatable country object. I sure hope it becomes available in next release. We actually have more and more CP clients asking about it.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To maximize performance, the DoS/Rate Limiting policy is enforced as early as possible in the packet flow. For most features this means it is enforced in SecureXL.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is an important question, for me, at least...does that method from the link you gave ONLY blocks vpn access or any traffic?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The syntax is an example, you can see the "service" parameter.
I know you will test it in your lab anyway as you should before trying it in the real world. 🙂
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think I sort of understand the syntax better now...as long as destination is external gateway IP, and source cc is actual country code, thats what matters. Not sure if cc syntax can be used multiple times in same command, but will try tomorrow in the lab...what I mean is say source cc:CN cc:EE ...multiple country codes like that.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please share with us the results of your tests, my friend. 🙌
And if you are successful, well, it could be nice to know what your procedure was. 🤙
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
See, the problem is, I dont have real external IP configured in my lab, so best I can do in the meantime is run the command and see if it takes it and let you know.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay, commands do work, which is awesome, BUT, only way to know 100% if its successful is to try it on real production fw with valid external IP address. By the way, multiple cc options dont work, see below. You simply use 2 letter country codes as per below link and what @PhoneBoy gave in his post.
Andy
Country Codes, Phone Codes, Dialing Codes, Telephone Codes, ISO Country Codes
[Expert@CP-TEST-FW:0]# fwaccel dos rate add -a b source cc:CA
uid="<65731a1c,00000000,e90a10ac,0000026b>"
[Expert@CP-TEST-FW:0]# fwaccel dos rate add -a d -l a service any source cc:CN cc:EE destination cidr:172.16.10.213/32 pkt-rate 0
ERROR: add quota: unknown key name 'cc:EE'
[Expert@CP-TEST-FW:0]# fwaccel dos rate add -a d -l a service any source cc:CN cc:FI destination cidr:172.16.10.213/32 pkt-rate 0
ERROR: add quota: unknown key name 'cc:FI'
[Expert@CP-TEST-FW:0]# fwaccel dos rate add -a d -l a service any source cc:CN destination cidr:172.16.10.213/32 pkt-rate 0
uid="<65731a7c,00000000,e90a10ac,00000414>"
[Expert@CP-TEST-FW:0]# fwaccel dos rate add -a d -l a service any source cc:FI destination cidr:172.16.10.213/32 pkt-rate 0
uid="<65731a84,00000000,e90a10ac,000004e5>"
[Expert@CP-TEST-FW:0]# fwaccel dos rate add -a d -l a service any source cc:EE destination cidr:172.16.10.213/32 pkt-rate 0
uid="<65731a8a,00000000,e90a10ac,00000504>"
[Expert@CP-TEST-FW:0]# ^C
[Expert@CP-TEST-FW:0]#
******************************************
[Expert@CP-TEST-FW:0]# fwaccel dos rate get
fwaccel dos rate add -i "<65731a1c,00000000,e90a10ac,0000026b>" -action bypass source cc:CA service any
fwaccel dos rate add -i "<65731a8a,00000000,e90a10ac,00000504>" -action drop -log alert service any source cc:EE destination cidr:172.16.10.213/32 pkt-rate 0
fwaccel dos rate add -i "<65731a7c,00000000,e90a10ac,00000414>" -action drop -log alert service any source cc:CN destination cidr:172.16.10.213/32 pkt-rate 0
fwaccel dos rate add -i "<65731a84,00000000,e90a10ac,000004e5>" -action drop -log alert service any source cc:FI destination cidr:172.16.10.213/32 pkt-rate 0
(4 rules found)
[Expert@CP-TEST-FW:0]#
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does your lab have a real external IP?
Does Mobile Access or IPsec VPN work in your LAB for remote connections?
If not, I can try, from my location, to reach your LAB, to see if it works, HAHA. 😅
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, escribiré esto en español jajaja. Como ya dije dos veces, no, no tengo una IP externa en mi laboratorio, por lo que la única forma de confirmarlo es hacerlo en undispositivo que sí la tenga. Los comandos funcionan
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We will have to 'sacrifice' a customer, and give it a try.
Let him be our 'trojan horse'. 🤣🫣
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
lol...or guinea pig as they say
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I will see later of I can do some natting on our lab Fortigate firewall to get real external IP working, so this can be tested properly.
Andy
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter