- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Unleashing Performance & Stability
with Harmony Endpoint E88.70!
It's Here!
CPX 2025 Content
Zero Trust: Remote Access and Posture
Help us with the Short-Term Roadmap
The Future of Browser Security:
AI, Data Leaks & How to Stay Protected!
CheckMates Go:
Recently on CheckMates
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Remote Access VPN
- :
- Re: REMOVE LOG IN OPTION FROM REMOTE ACCESS VPN
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
REMOVE LOG IN OPTION FROM REMOTE ACCESS VPN
Hello,
We have configured Identity Provider Authentication for remote access vpn users.
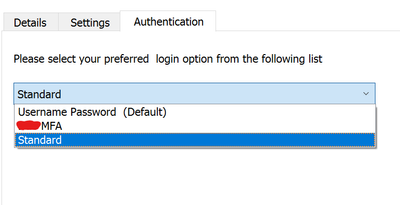
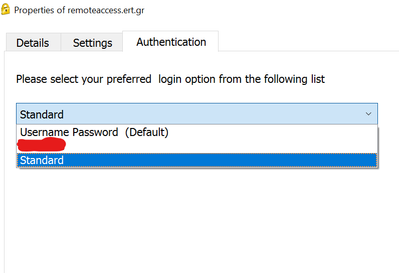
When we login with Check Point Mobile App for Windows we have the following options.
What we want is to remove the "Standard" login option.
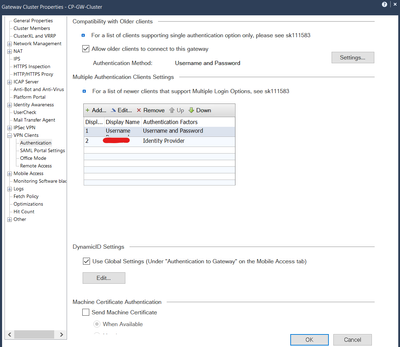
At Gateway Cluster Properties -> VPN clients -> Authentication -> Multiple Auth Clients Settings the configuration is the below.
Thank you
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can remove it from gateway properties, I cant recall what its called, I believe username/password, but will check later in the lab.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I can remove the username/password. The MFA becomes default authentication method, but "Standard" still remains.
I can't find any tab to remove it.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
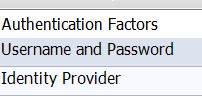
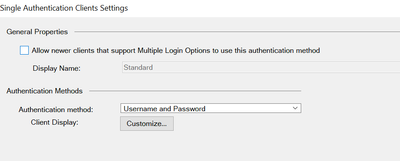
I believe this is what you need to uncheck.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
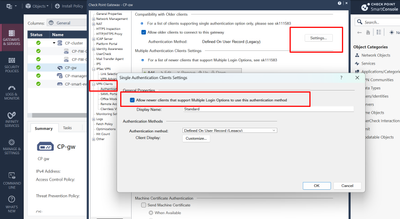
Hi Andy,
I have already done this without success. The Authentication method at your screenshot is the legacy one. We have configure it as "Username and Password", does it matter?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Which Authentication method is presented after choosing Standard ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you please send screenshots of how thats configured? Please blur out any sensitive info. I know 100% this is possible, as I had done it before, just cant recall now exactly how...
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
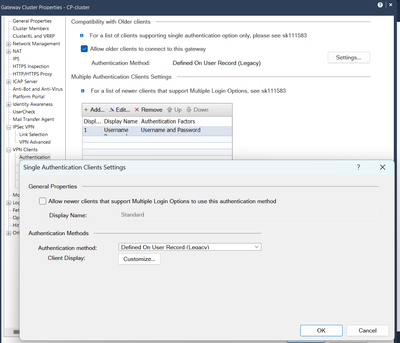
Sure. The current one is the below.
I did uncheck the box, as below, but the "Standard" authentication method still appears at the mobile client
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
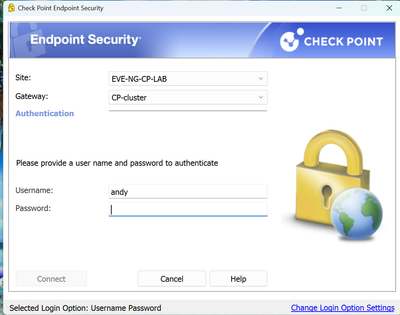
Here is what I just tested in the lab and worked fine, does NOT show standard in the list anywhere. I dont believe you would need to delete/re-create VPN site just for this, but to test that theory, you can have one user try and see result they get.
Kind regards,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Based on your test the authentication method must be "Defined on user record (legacy)". Unfortunatelly I cannot change the authentication from "Username and password" and I will explain why.
We have connected more than one domains with the firewall. In these domains there are same sam account names (eg test@domain1, test@domain2 etc). In this case with authentication method "Defined on user record (legacy)", when a vpn user enters credentials at the Mobile app, search takes place only in one domain.
However, I tested with authentication "Username and Password" and it works only if site is recreated. It this case "Standard" authentication method is disapperared. It is ok for my case.
Thank you very much for the assistance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In that case, maybe contact TAC and do remote session to find the best option. Its not really feasible to ask your users to delete/re-create the site. I know in the past, with one large cusotmer we have, couple of my colleagues had to do some modifications in trac.config file and push it via GPO to make things work.
Best regards,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sure. It would be very helpful if the site has not to be recreated.
I will contact TAC and come back with solution.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think say if you had dozens of users, not a big deal, but if company has 100s of employees, its not a scalable "solution".
Let us know what TAC tells you.
Best regards,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Sure, I will come back with feedback.
I more question please.
Can I restrict remote access vpn access from Capsule VPN for mobile (Android & IOS) based on username that users login?
This is because, when Identity provider authentication is selected, 2MFA is not working in R81.10. This is gonna be solved in take 113(it is not recommended right now).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not that I know of. I would wait for jumbo to be recommended.
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Tue 01 Apr 2025 @ 11:00 AM (IDT)
Simplifying Zero Trust with Infinity Identity: Centralized, Scalable, Secure - EMEATue 01 Apr 2025 @ 06:00 PM (IDT)
Simplifying Zero Trust with Infinity Identity: Centralized, Scalable, Secure - AmericasWed 02 Apr 2025 @ 03:00 PM (CEST)
The Power of SASE: Smarter Security, Stronger Network - EMEAWed 02 Apr 2025 @ 02:00 PM (EDT)
The Power of SASE: Smarter Security, Stronger Network - AmericasThu 03 Apr 2025 @ 01:00 PM (CEST)
Meet the Experts: Transforming Security Operations with Impactful Intelligence!Tue 01 Apr 2025 @ 11:00 AM (IDT)
Simplifying Zero Trust with Infinity Identity: Centralized, Scalable, Secure - EMEATue 01 Apr 2025 @ 06:00 PM (IDT)
Simplifying Zero Trust with Infinity Identity: Centralized, Scalable, Secure - AmericasWed 02 Apr 2025 @ 03:00 PM (CEST)
The Power of SASE: Smarter Security, Stronger Network - EMEAWed 02 Apr 2025 @ 02:00 PM (EDT)
The Power of SASE: Smarter Security, Stronger Network - AmericasThu 03 Apr 2025 @ 01:00 PM (CEST)
Meet the Experts: Transforming Security Operations with Impactful Intelligence!Thu 10 Apr 2025 @ 10:00 AM (EEST)
CheckMates Live Sofia - Maintenance and Upgrade Best PracticesTue 06 May 2025 @ 09:00 AM (EEST)
CheckMates Live Cyprus - Performance Optimization Best PracticesAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter