Need to vent a bit... 😉 We've grown pretty frustrated with CP's VPN clients. The issues surrounding needing Local Admin to install or upgrade SNX/SSL client or the Standalone Endpoint VPN client on corporate PCs that live OUTSIDE our internal LAN / Domain is really a PITA to manage. We turned to using the Check Point Capsule VPN from the MS Store as it does not need Local Admin privileges to install and pretty easy for our very non-technical healthcare providers to configure with just a phone call.
We have run into issues with the Capsule Client -- won't register in our DNS and Split Tunneling does not seem to work. We want Internet traffic to go out the user's local Internet. So I contact TAC over all the VPN Client issues.
I've read the SK about using MSIEXEC to install SNX/SSL. This requires we do this for every remote PC we have -- which is really not plausible. And when we upgrade to R81.20, we can be sure that the SNX version will change. Yes, I know how to modify slim_ver and snx_ver files to suppress upgrade. However, I was just informed by TAC that SNX/SSL does NOT support Win 11 yet -- with no date yet for official support. Well that explained the Install error "30" I was getting on my Win 11 Laptop (I have Local Admin rights). I asked if there was an SK on it and was pointed to the Generic SK and told if the OS is not specifically listed, it is not supported.
The Endpoint Standalone VPN client. Same general issues as SNX/SSL in that we'd have to reach out individually to install or update on the Remote PCs. It has a way to create a package with all the necessary settings for the user. I have the manual but quite haven't gotten it figured out. Even our old CP SE, couldn't figure it out! I miss the old method of using ORCA to modify the MSI's variables! Plus it was inferred that this client may not officially support Win11.
Back the Capsule Client in the MS store - which works on Win 11. Yes, I gather it is a shell wrapped around native Windows IPsec connectivity support. Regarding the issues mentioned above, we talked to Microsoft support, they say its Check Point responsibility. Check Point TAC says talk to Microsoft. I hate to side with Microsoft, but it is branded as a Check Point product - so Check Point TAC should be able to support it. Would love to figure out a way to incorporate it into our corporate PC image.
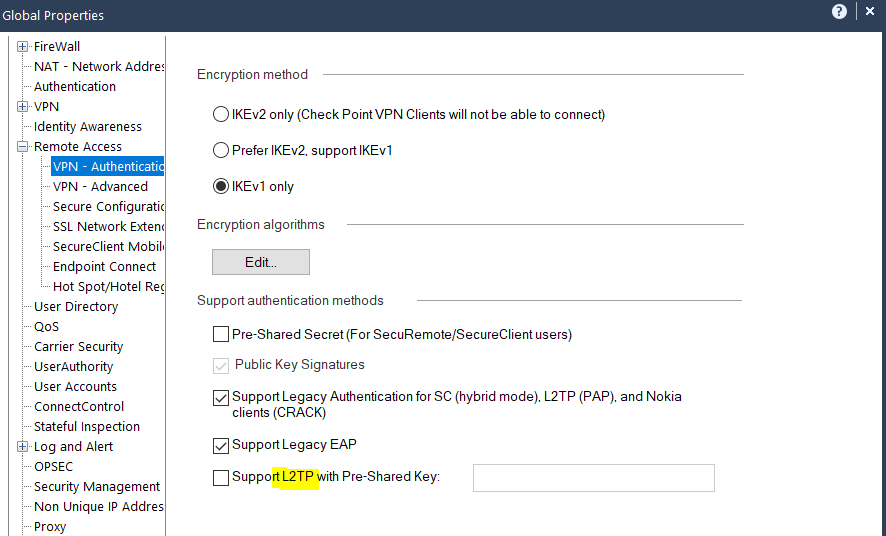
So we thought about trying L2TP, So I bring up sk63324. The screen shots look nothing like what we see in R81.10. I searched thru all the VPN settings on our GW and the RemoteAccess Community. I can't find anywhere where the L2TP PSK would be entered. We do have Radius and DUO config'd for 2FA or any VPN connection. We use OfficeMode IPs. So I am not sure if that suppresses some of the setting options shown in the SK. It seems that the sk should at least be updated.
So I am looking for hints on the L2TP setup in hopes it fixes some of the above issues regarding split-tunnel, client DNS registrations.
Thanks for "listening"!
Perry