- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Quantum SD-WAN Monitoring
Register HereCheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
MVP 2026: Submissions
Are Now Open!
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Re: Mobile Access - IP Pool Configuration
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Mobile Access - IP Pool Configuration
Halo All,
I was enable Mobile Access Blade for SSL VPN and follow the wizard.
And this is the traffic : USER (public) —INTERNET— Mobile Access (R81.10) — Core — Internal Apps.
Mobile Access has 2 interface :
- ETH1 : Public IP (facing to internet + portal access)
- ETH2 : Local IP (point2point with Core)
- + IP Pool VPN (default segment IP)
And Mobile Access configuration like below :
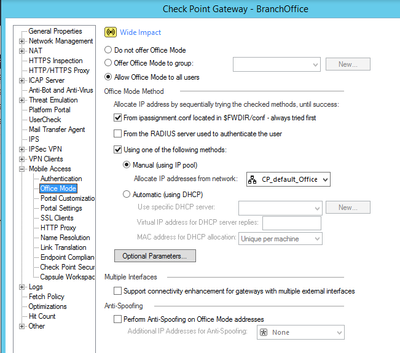
My question is, why all Mobile Access user when access to internal apps detected using ETH2 IP (Local IP) not Pool VPN IP? When i check on Mobile Access Log, there are only Public IP information from user.
Based on above information, is my configuration wrong? any additional configuration needed?
Thankyou!
Labels
- Labels:
-
Mobile Access Blade
-
Windows
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
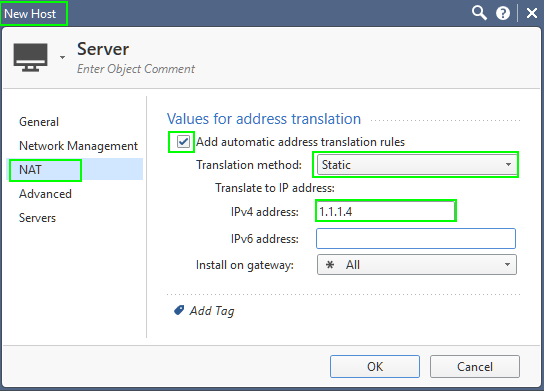
Both, Automatic NAT and Manual NAT should be used simultaneously. But if the properties of your Office Mode Pool look like the screenshot above, they are misconfigured. Use this one for references:
Set the Pool NAT properties as shown above, but add the NonNAT_Rule I have suggested previously.
If you are using Remote access with DNS forwarding to HQ and egress to the Internet resources, you want the pool to be NATed going outside. For access to internal resources, you do not- hence the Non_NAT Rule.
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
See Mobile Access R80.10 Administration Guide: Office Mode
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes i just compared my configuration with admin guide.
On $FWDIR/conf/ipassignment.conf i make sure on this config file there is no configuration related to Local IP and Pool VPN IP. So in my opinion will take over by Manual (using IP Pool), but i dont know why on Application detect the user using ETH2 Local IP, not Pool VPN IP. This one make me confused.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe ipassignment.conf would take precedence.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Theo yeah i believe so earlier, but after check the $FWDIR/conf/ipassignment.conf there is no configuration related to IP that i used on the firewal..
This is the capture :
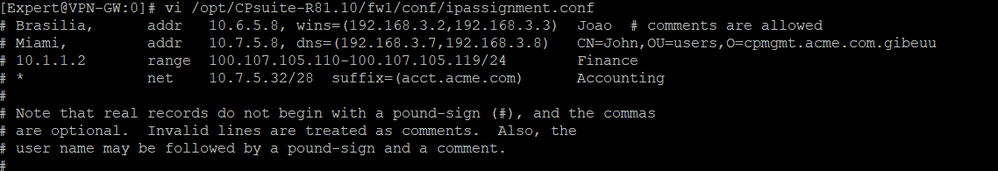
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Right, thats what every default ipassignment.conf would look like, so it does not appear it was modified manually.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I assume you are using SNX or the Mobile Access vpn client on your remote machines in order to get an Office Mode IP address, it would be useful a capture what you see to understand better. I will assume you are checking only the logs for decrypted packets, maybe there is a NAT causing this behavior. To start you can go to the logs and look for blade:"Mobile Access" search your login and take note of the office mode ip assigned, then look for that IP address and check what you see, if there is a NAT you should find it here.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Likely a NAT issue.
I suggest creating a NO_NAT_for_Remote_Access rule in your NAT policy and configuring it as:
CP_Default_Office_Mode_Pool to Internal_Networks, Original, Original.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Agree, likely your hitting default/atuo NAT rules similar to:
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Chris_Atkinson and @Vladimir
Thank you for your reply, currently i dont have access to the Gateway. i will it again on Thursday.
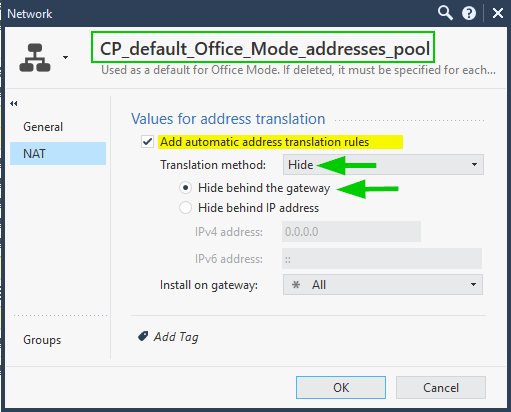
your suggestion is using manual nat or automatic nat? because i did some nat test before, by default VPN-IP-Pool is enable Hide NAT like below, but after i uncheck the NAT option, there is no differentiation. Is it similar with your suggestion using Manual NAT or Automatic NAT?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Both, Automatic NAT and Manual NAT should be used simultaneously. But if the properties of your Office Mode Pool look like the screenshot above, they are misconfigured. Use this one for references:
Set the Pool NAT properties as shown above, but add the NonNAT_Rule I have suggested previously.
If you are using Remote access with DNS forwarding to HQ and egress to the Internet resources, you want the pool to be NATed going outside. For access to internal resources, you do not- hence the Non_NAT Rule.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter