I was using the approach described on the documentation and everything is running fine without machine cert auth:
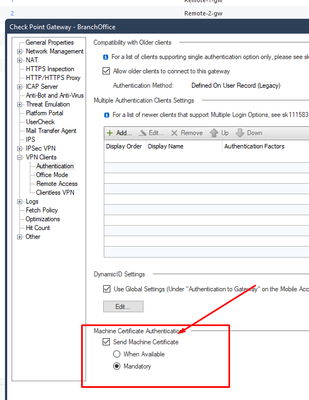
Thinking as a more secure way trying to narrow down the access roles to the specific OU containing the machines as well.
Checked also this one :
sk170140
Some logs from the trac.log:
[ 5520 6368][8 Jun 0:19:17][RaisCertManager] SetFriendlyNameOnToken: __start__ 0:19:17.241
[ 5520 6368][8 Jun 0:19:17][RaisCertManager] GenerateFriendlyNameWithSerial: __start__ 0:19:17.241
[ 5520 6368][8 Jun 0:19:17][RaisCertManager] RaisCertManager::_GenerateFriendlyNameWithSerial: ERROR!! subject or serial is empty, return empty string
[ 5520 6368][8 Jun 0:19:17][RaisCertManager] GenerateFriendlyNameWithSerial: __end__ 0:19:17.241. Total time - 0 milliseconds
[ 5520 6368][8 Jun 0:19:17][RaisCertManager] SetFriendlyNameOnToken: __end__ 0:19:17.241. Total time - 0 milliseconds
[ 5520 6368][8 Jun 0:19:17][] fwCAPIProvider_imp::GetToken: Machine certificate, index 1.
[ 5520 6368][8 Jun 0:19:17][] fwCAPIToken::fwCAPIToken: enter (1) start (03331588, imp: 01E0A9F8)
[ 5520 6368][8 Jun 0:19:17][] fwCAPIToken_imp::Init2(PCCERT_CONTEXT TheCert): enter... machineCtx is 1
[ 5520 6368][8 Jun 0:19:17][] MyprintCertName:fwCAPIToken_imp::Init2(PCCERT_CONTEXT TheCert) enter...
[ 5520 6368][8 Jun 0:19:17][] MyprintCertName:fwCAPIToken_imp::Init2(PCCERT_CONTEXT TheCert) cert name is: CN=test.contoso.local
[ 5520 6368][8 Jun 1:15:36][Rais_CAPICERT] Rais_CAPICERT::capi_cert_sign: Failed to sign Buffer
[ 5520 6368][8 Jun 1:15:36][] fwPubKey::SetMachineCtx: enter.. about to set to 0
[ 5520 6368][8 Jun 1:15:36][] fwWinPubKey_imp::SetMachineCtx: about to set machine contex to 0.
[ 5520 6368][8 Jun 1:15:36][Rais_CAPICERT] capi_cert_sign: __end__ 1:15:36.930. Total time - 5 milliseconds
[ 5520 6368][8 Jun 1:15:36][Rais_CAPICERT] CAPICert::Sign: __end__ 1:15:36.930. Total time - 5 milliseconds
[ 5520 6368][8 Jun 1:15:36][Rais_CAPICERT] Rais_CAPICERT::CAPICert::Machine_Sign: done.
[ 5520 6368][8 Jun 1:15:36][IKE] create_MM5(hybrid authentication): Failed to sign hash with the machine's certificate (-996)
[ 5520 6368][8 Jun 1:15:36][rais] [DEBUG] [RaisMessages::CreateMessageSet(s)] message: (msg_obj
:format (1.0)
:id (ClipsMessagesInternalError)
:def_msg ("Internal error; connection failed. More details may be available in the logs")
:arguments ()
)
[ 5520 6368][8 Jun 1:15:36][TR_FLOW_STEP] TR_FLOW_STEP::TrConnEngineConnectStep::operation_failed: Cb arrived
[ 5520 6368][8 Jun 1:15:36][FLOW] TrConnEngineConnectStep::operation_failed: user message set: (msg_obj
:format (1.0)
:id (ClipsMessagesInternalError)
:def_msg ("Internal error; connection failed. More details may be available in the logs")
:arguments ()
I am having hard time to understand why it is not working while I have the whole chain of certificates enrolled and on the relevant local machine relevant areas, have used the same PKI certificates in this case, just created a new one on the Personal Certificates on local machines since the subject was missing and we edited an existing template on the CA server in order to create a new request having the possibility to fill in the "Subject" filed there.
Not sure what important task I might have missed to mention here, please let me know if more needs to be described by me.
Thank you and best regards.