- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Hybrid Mesh
- :
- SASE and Remote Access
- :
- Re: How to increase VPN timeout limits?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
How to increase VPN timeout limits?
We currently have our VPN users set to an 8 hour timeout. We have one supplier that needs this to be longer though. Is there any way to increase the length of time without doing it for all users?
Currently running E80.81 for the client and R77.30 on our gateways.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I must be reading his comment wrong. I see it saying I have an 8 hour max. He also says I can only change it in the gui or guidbedit.
The doc I posted says I can go to 1440 so I'll assume that is still the max.
So you are saying that my change below looks ok?
:neo_user_re_auth_timeout (
:gateway (endpoint_vpn_user_re_auth_timeout
:default (1440)
24 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
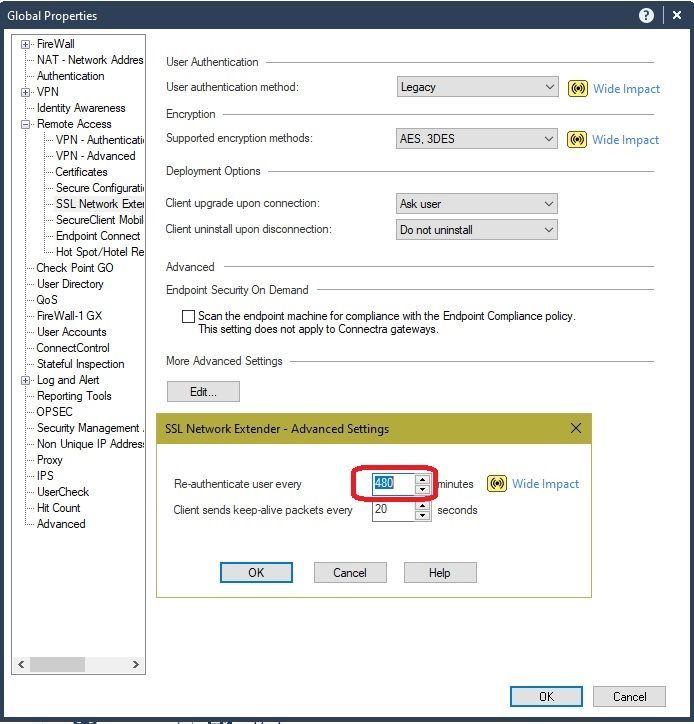
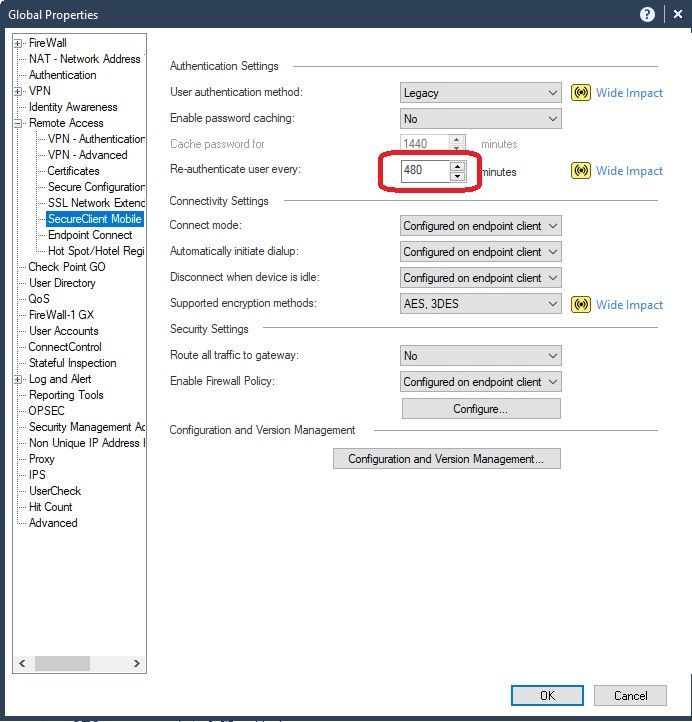
I think that this 8 hours is not a sort of timeout but concretely the Re-Authentication period.
In the Remote Access Clients for Windows 32/64-bit Administration Guide E80.72 and Higher we can learn that we can change the value in In Authentication Settings of Global Properties > Remote Access > Endpoint Connect
But this can be also change more specifically per Security Gateway or per client using the trac.defaults neo_user_re_auth_timeout variable.
Could you try changing this value and telling us if that answer to your needs?
Cybersecurity Evangelist, CISSP, CCSP, CCSM Elite
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you want to do it per user group: Remote Access clients configuration based on group membership
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's exactly what I was looking for. Putting int he required paperwork now to test this next week. Will update with results.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Will this work when the user belongs to multiple groups and is there anything I should be wary of regarding this.
The user currently is currently in 4 different user groups. These are used in 4 different VPN rules.
Was thinking of making a new group called ExtendedTimeout and making the ExtendedTimeout.ttf with a 24 hour timeout. Would I just add the user to this group along with the groups they already have? Does this new group need to be used in an access rule anywhere?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't believe the group has to be used in the rulebase, the group just needs to exist and users need to be members of it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Went to make the change this morning but can't find how to properly change the value in the ttm file.
I assume that the section we want to change is the neo_user_re_auth_timeout
From this doc I found the max is 24 hours though. We wanted to change it something closer to a week for this one specific account.
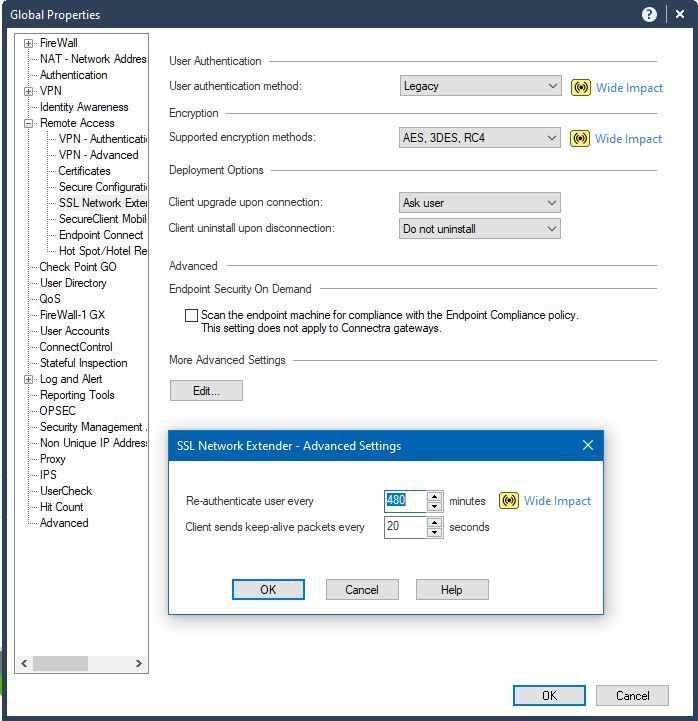
This screenshot is from an older doc I found.

Do these values still hold true for max? And if I am able to change it to something else what is the proper syntax?
Currently running R77.30
Finding the docs confusing.
Would I change
:neo_user_re_auth_timeout (
:gateway (endpoint_vpn_user_re_auth_timeout
:default (client_decide)
to
:neo_user_re_auth_timeout (
:gateway (endpoint_vpn_user_re_auth_timeout
:default (1440)
Really want 10080 instead of 1440.
Help please!! ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In sk75221 Remote Access TTM Configuration relevant for the used version, we find that:
Attributes that were defined in the Security Management (SmartCenter) database schema cannot be changed in the TTM file. They can only be changed via SmartDashboard or via the GuiDBEdit tool. Examples: tunnel_idleness_ignored_tcp_ports, tunnel_idleness_timeout, location_awareness_dc_check, location_awareness_enabled etc. More information on these attributes can be found in the Admin Guide. Parameter tunnel_idleness_timeout is listed in sk42850 with a similar comment.
But i think i have found your 8 hours limit:
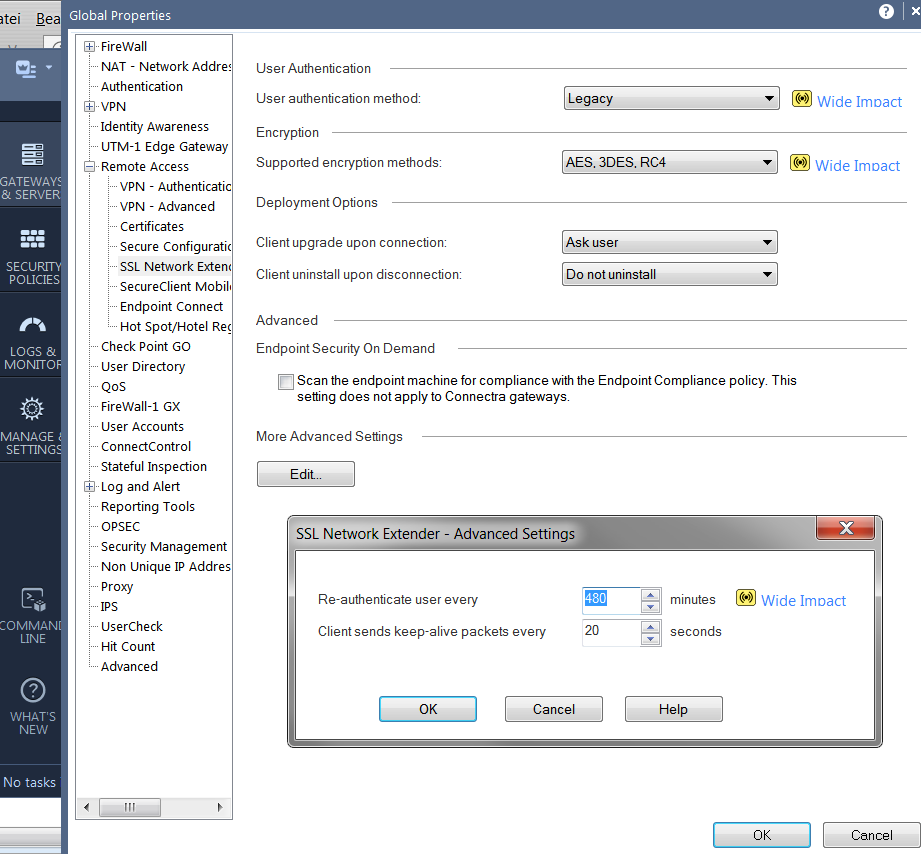
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you look at my message you see that there is a limit of up to 1440 minutes from what I'm seeing. That is 24 hours.
I was asking how to modify the ttm file correctly to use this value. Also the screenshot you showed is from the new version which is different from what I understand.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
According to what I'm reading, this should be the correct approach (your modifications to trac_client_1.ttm).
Note while Guenther is showing a screenshot from R80.x, it's the same in R77.30 as well (just "looks" different).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I must be reading his comment wrong. I see it saying I have an 8 hour max. He also says I can only change it in the gui or guidbedit.
The doc I posted says I can go to 1440 so I'll assume that is still the max.
So you are saying that my change below looks ok?
:neo_user_re_auth_timeout (
:gateway (endpoint_vpn_user_re_auth_timeout
:default (1440)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All of those things are true.
Your change looks ok
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The only document refering to neo_user_re_auth_timeout is R70 VPN Administration Guide, so i am really eager to know if this works !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I found the answer: endpoint_vpn_user_re_auth_timeout is refered to in sk62581 EndPoint Connect users required to re-authenticate every 480 minutes
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Seems to have worked guys. I have made the changes and added myself to the group. VPN'd in and I have the 1440 timeout in my settings now.
Still need to leave things connected for a day and double test though.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @David_Won , how did you change it, via the ttm file or you follow the screenshot of @G_W_Albrecht? Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
I just add my question to this thread, because I think the topic is fitting.
How to increase the session length when using "Check Point Capsule VPN" from Microsoft Windows Store?
At the moment the connection drops after 8 hours.
Best regards,
morris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Pretty sure it is these three settings, they are linked so if you change one of them it automatically changes the other two:
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear IT and security guy , after you changed the minutes in Global Properties => remote Access => Endpoint Security VPN or End point Connect
please shutdown client on the computer that using remote access and turn it on again .
its impotent to make it active.
i am using Gaia 80.10
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear IT and Security Guys
for make sure the time expire will increase , you have to turn off (shutdown) the client end point connect
and turn on , on the workstation.
i am using gaia R80.10
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there a reason to post twice?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Guys,
has anybody achived this to get it working? to set a specific duration without getting asked for re-authentication?
there are so many parameters to try here ...
i have exactly the opposite usecase, the customer wants to limit the time the user can stay connected with Client VPN!
the re-authentication timeout in SmartConsole only triggers a pop-up to reauthenticate ... of course the user enters a password.
did anybody made it working with this setting?
neo_user_re_auth_timeout (
:gateway (endpoint_vpn_user_re_auth_timeout
:default (1440)
i also saw, when a user has set specific timeslot for allowing a VPN connection, this settins only prevent NEW connections after the timeslot has expired, but running connection doesnt time out ... ;-(
how can you kick out a remote user when the time is up?
automatically not manually of course ...
i fear this is only possible with some scripting to collectt all expired time objects from the rulebase, search for the users which are using this affecting rules and kick them from Clienbt VPN ...
please keep in mind every user has different time objects, i cannot globaly say time is up at 05:00pm
this is also an awesome idea: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
to have different trac_client_1.ttm for different groups ... (employes / external)
best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello again,
has anybody tried this options?
)
:neo_implicit_disconnect (
:gateway (endpoint_vpn_implicit_disconnect
:default (client_decide)
)
)
:neo_implicit_disconnect_timeout (
:gateway (endpoint_vpn_implicit_disconnect_timeout
:default (client_decide
would be interessting to know how the work in real world
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
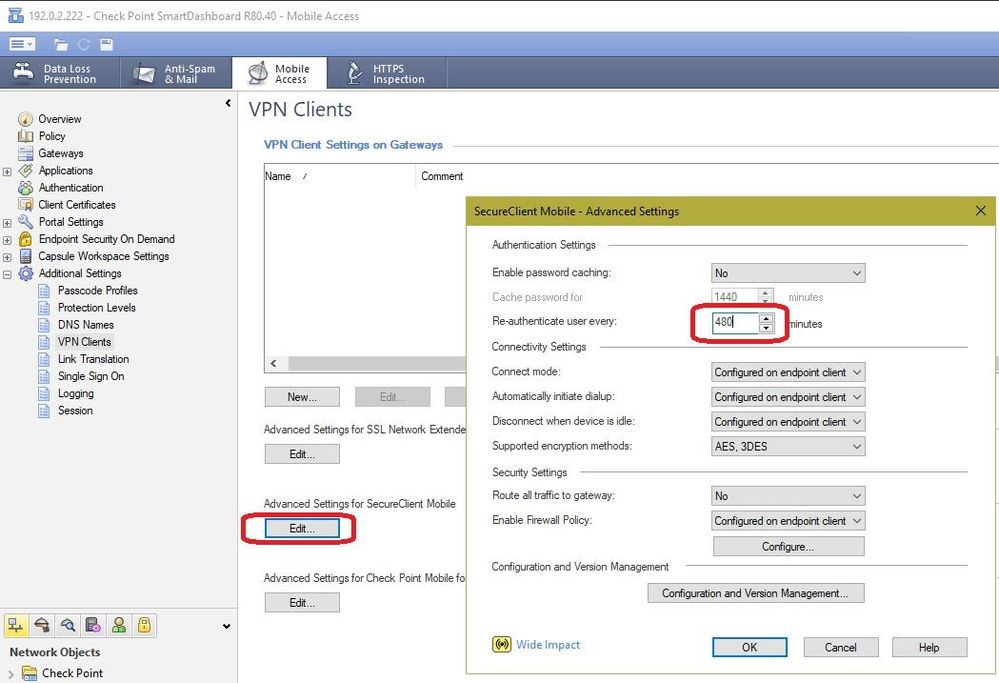
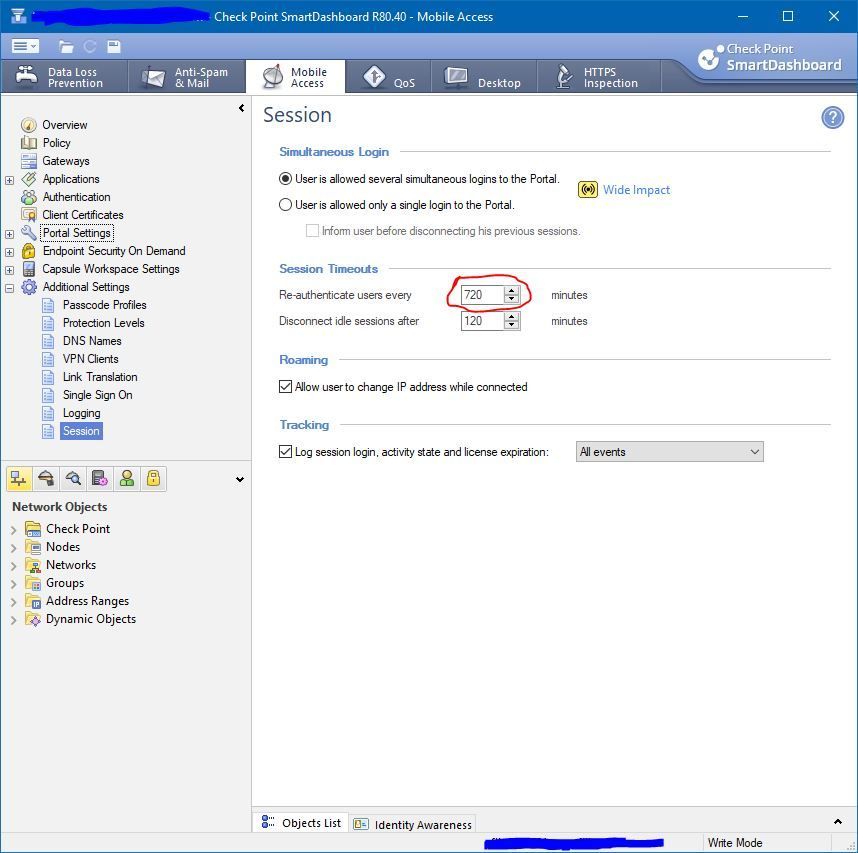
In my environment, there are two places where the SNX Timeout is defined, and they are not linked..
Our environment is still using the Legacy Mobile Access Policy for managing the Mobile Access, so perhaps that is why these two settings do not agree, but our timeout is the intended 12 hours:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This post from 2018 pops up as the most popular answer. To updated it for 2026 and Quantum Spark R81, the setting can be found here:
Device>Advanced>Advanced Settings>Remote Access VPN - Endpoint Connect re-authentication timeout (in minutes)
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 4 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesTue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANThu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesTue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter