- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E5:
Powering Prevention: The AI Driving Check Point’s ThreatCloud
The Great Exposure Reset
AI Security Masters E4:
Introducing Cyata, Securing the Agentic AI Era
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Hybrid Mesh
- :
- SASE and Remote Access
- :
- How to enable Secure Client Verification?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to enable Secure Client Verification?
I'm using the checkmates to learn, my interest is in the VPN service that I was able to replicate. I used with an workstation running the last Check Point Endpoint security client and it connects fine. I want to test secure client verification to validate for example if my antivirus is running and my machine is on my domain. I saw compliance options inside Mobile Web Access, at the rules dashboard there is a link to open a new dashboard that allows me to create a new rule or edit the 3 defaults (high, medium and low), however it never runs on my client.
I searched and my guess is that it only works with mobile vpn client and not Check Point Endpoint Security (that if I understood properly is stronger -so I prefer use it to test). I found this article (https://namitguy.blogspot.com/2020/04/implementing-secure-client-verification.html) suggesting that I have to enable a special feature at Remote access -> Secure Configuration Verification. However I don't see it on the CheckMate labs. Maybe is it a feature on old version? Doesn't exist anymore?
Also, it says to enable IPSEC and Policy Server feature, and than a policy named desktop security. All fine, except that the rules at desktop security appears to be related with inbound and outbound rules and not process checks for example. What am I missing?
Also, once it's enable the only way to create the rules is editing the file mentioned with vi (command-line)?
The official pdf looks more or less the same https://community.checkpoint.com/t5/Remote-Access-VPN/White-Paper-Check-Point-Compliance-Checking-wi...
I could not find, is there any command (command line) to verify if secure client verification is enabled and my checkpoint is using the current local.csv file?
All help is very welcome!
Labels
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SCV is definitely an older feature, however customers still use it both with Check Point Mobile and Endpoint Security VPN.
SCV is also limited to Windows clients currently.
The Desktop Policy is actually firewall rules for the client, yes.
And yes, it is required to utilize SCV.
See: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Gotcha @PhoneBoy. Is there a better way to enforce such king of checks since it's an old feature?
Since SCV only works on Windows, do you know how is possible to prevent any computer that is not Windows (such as Mac) to log-in on my checkpoint vpn?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The SCV check would fail on anything that can't run SCV and you can configure (in Global Properties, I believe) whether that would be allowed or not.
The other way to do it would be Endpoint Compliance, which requires Endpoint licensing (or legacy ACCESS licenses).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@PhoneBoythank you for answer.
Before asking questions I tried to configure SCV to fail on anything that can't run SCV, but I failed miserable. Can you please give me more details?
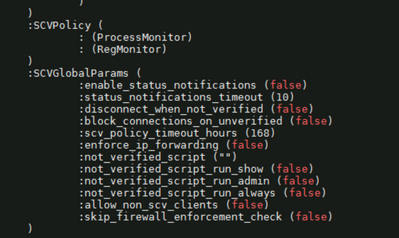
Below is my scv config to test
and my global properties
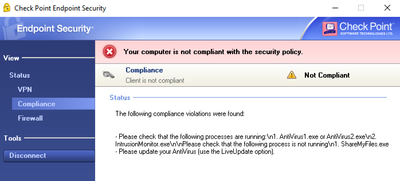
my windows fail because it's not compliant
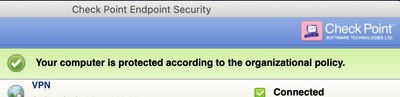
but my mac always work, no matter what i do it connect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The Mac is showing compliant because it's using Endpoint Compliance and not SCV.
Can the Mac actually connect to the relevant resources?
If so, I recommend a TAC case for further troubleshooting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks @PhoneBoy
Is there a way to ignore endpoint compliance and force that any client that doesn't support SCV will not log on my vpn?
I tried to create a endpoint compliance to test (the default high) and there is no AV on this mac but it still connects fine.
Yes, the mac is able to access my internal file share via this vpn
Sorry for ignorance, what is a TAC case? I'm not a customer...I use the lab to learn Checkpoint amazing tools
An alternative could be to allow only computers (Windows) to log on my vpn and have SCV pass, all other clients (Linux, Mac) I want to deny directly. Is it possible?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Even a non-compliant computer is allowed to connect to the VPN.
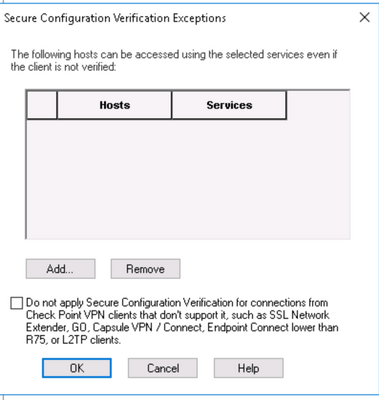
However, they would only be permitted access to the specific items allowed in the screenshot (i.e. for remediation purposes).
All make sure local.scv is configured to not allow non-SCV clients to connect.
Basically the opposite of: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
Yes, TAC requires having a support agreement.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Got it @PhoneBoy
I think that I can't see the screenshot (where to define what resources are allowed to remediation purpose). Do you have it anywhere else? Restrict to only one server or maybe none could be an solution...
Mine is configured as :allow_non_scv_clients (false)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's actually in the screenshots you've already provided (Secure Configuration Verification Exceptions)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @PhoneBoy. I played a lot with that screen and no matter what I do, Mac clients are allowed to connect at VPN and reach any internal server. 😞
Any guess?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What version/JHF of gateway is involved?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey, did you already tried to do?
:disconnect_when_not_verified (true)
:block_connections_on_unverified (true)
as well as
:allow_non_scv_clients (false)
In the global Properties i didnt have to anything in mine.
This is will make if you are not compliant it will block the connection, even tho the VPN can Log in, after 20 seconds you will be dropped
Best Regards,
Perdro Filipe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @pfilipe,
I tried it and many combinations, just to make sure I tried again now...
:SCVGlobalParams (
:enable_status_notifications (false)
:status_notifications_timeout (10)
:disconnect_when_not_verified (true)
:block_connections_on_unverified (true)
:scv_policy_timeout_hours (168)
:enforce_ip_forwarding (false)
:not_verified_script ("")
:not_verified_script_run_show (false)
:not_verified_script_run_admin (false)
:not_verified_script_run_always (false)
:allow_non_scv_clients (false)
:skip_firewall_enforcement_check (false)
I connect on my Windows and it works as expected. On Mac with last endpoint security client no matter what I do, I keep connected and can reach any internal server 😞
Have you tried it with the last mac client?
Do you use CheckMate Labs? I'm asking because I'm using it and I'm not sure if there is anything different there.
In theory I see that people claim that it works, but I'm ashamed that I can't make it work.
https://supportcenter.checkpoint.com/supportcenter/portal?action=portlets.SearchResultMainAction&eve...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @afranklin
By " it works as expected" you mean if Windows client is not compliant it is not able to access encryption domain and when compliance status is changed access is restored?
Also in the Access Control -> Policy do you have "Remote Access" community configured in VPN column for the rules allowing traffic from RA users to encryption domain?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 5 | |
| 4 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Fri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáThu 12 Mar 2026 @ 05:00 PM (CET)
AI Security Masters Session 5: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 12 Mar 2026 @ 05:00 PM (CET)
AI Security Masters Session 5: Powering Prevention: The AI Driving Check Point’s ThreatCloudTue 17 Mar 2026 @ 10:00 AM (CET)
Industrial Cybersecurity in Practice: Manufacturing & Utilities - EMEATue 17 Mar 2026 @ 03:00 PM (CET)
From SASE to Hybrid Mesh: Securing Enterprise AI at Scale - EMEAFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáTue 24 Mar 2026 @ 06:00 PM (COT)
San Pedro Sula: Spark Firewall y AI-Powered Security ManagementAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter