- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Discover the Future of Cyber Security:
What’s New in Check Point’s Quantum R82
Pick the Best of the Best of
CheckMates 2024!
Share your Cyber Security Insights
On-Stage at CPX 2025
Simplifying Zero Trust Security
with Infinity Identity!
Zero Trust Implementation
Help us with the Short-Term Roadmap
CheckMates Go:
What's New in R82
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Remote Access VPN
- :
- Re: Endpoint VPN users facing extreme slowness
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Endpoint VPN users facing extreme slowness
We are currently using Checkpoint Appliance 23500 in our Data Centre which is running in Cluster (Active/Standby).
We have approx: 2500 to 3000 active remote VPN users connecting to the firewall at a time during Peak business hours.
The Internet on the Checkpoint Firewall is 2Gbps, and it peaks upto 800Mbps during business hours.
There is 20 CPU's, and we have Multi-Threading enabled so total 40 Virtual CPU's, the CPU peaks to max 55% during the peak business hours.
Hub mode is configured to route all traffic through the gateway (due to security reasons we cannot change it).
Enabled blades:
[Expert@QTS-CP-NW-FW02:0]# enabled_blades
fw vpn cvpn urlf av appi ips identityServer anti_bot content_awareness mon vpn
Most of the Remote VPN users have an Internet speed of about 200Mbps, some even have 500Mbps.
But after connecting to Checkpoint Endpoint VPN the speed goes below 15 Mbps (Download) and Upload (50 Mbps), which is affecting 2000+ users.
Below are some of the verification done from our side:
1. We have auto_detect set for endpoint_vpn_ipsec_transport in Guidbedit Firewall properties.
2. SecureXL is enabled:
[Expert@QTS-CP-NW-FW02:0]# fwaccel stats -s
Accelerated conns/Total conns : 10/39553 (0%)
Accelerated pkts/Total pkts : 163746283249/335101509859 (48%)
F2Fed pkts/Total pkts : 9663120065/335101509859 (2%)
F2V pkts/Total pkts : 2927705054/335101509859 (0%)
CPASXL pkts/Total pkts : 0/335101509859 (0%)
PSLXL pkts/Total pkts : 161692106545/335101509859 (48%)
QOS inbound pkts/Total pkts : 0/335101509859 (0%)
QOS outbound pkts/Total pkts : 0/335101509859 (0%)
Corrected pkts/Total pkts : 0/335101509859 (0%)
3. We tried to change the Remote VPN Phase 1 and Phase 2 encryption algorithm to lower encryption AES-128 SHA-1, but still no improvements.
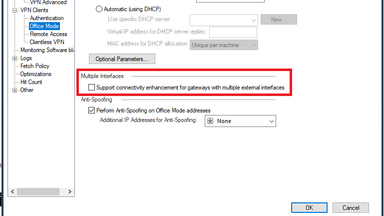
Also we have Multiple Interface option in VPN Clients --> Office Mode checked.
"Support connectivity enhancement for gateways with multiple external interfaces"
Need assistance to identify what is causing the network slowness issue in checkpoint VPN.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello!
oh great thing ...
I know about this option, but on a new version like 81.10 and newest SmartConsole i dont find this setting anymore ...
where is it?
Does it only exists if the gateway has configured more then one external interfaces ?
Or has it been removed from the SmartConsole?
Maybe its now in the depths of GuiDBedit ...
perhaps somebody knows the answer 🙂
so i dont have this on my R81.10 enviroment ...
OLD
NEW
best regards
20 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I read that you have 3000 RA clients in Hub mode - so when you divide GWs 2Gbps by 3000x2 (as most traffic goes thru the GW 2 times), what is left for each client ? Routing all connections makes a heavy load...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @G_W_Albrecht ,
Thank you for your quick response.
We have netflow enabled on the Gateway and as per the bandwidth utilisation report it never exceeds 800Mbps, if bandwidth was an issue we should have seen it peaking up to 2Gbps right.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the traffic on each of the 2 x 2000+ connections? 15 Mbps (Download) and Upload (50 Mbps) times 2000+ times two ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @G_W_Albrecht,
Actually I forgot to mention the below points as well:
1. We ran the speedtest, during non-business hours, that is at 2am EST when the active remote VPN users where around 50, the results were the same.
2. During the peak hours we also ran speedtest from the Servers within the DC (which are behind the CP firewall) we get speed upto 700 Mbps for download on these servers, the point to note is all the traffic is going only via the single 2Gbps circuit.
So not sure if bandwidth could be the reason which is causing the VPN slowness.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would consult with TAC about this !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @G_W_Albrecht for checking on this, actually we already have a ticket opened with Checkpoint Support for the same, currently its escalated to Tier-3 but still we are unable to find the root cause of the issue, so I thought to get help from the Checkpoint Community.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I second @G_W_Albrecht, hub mode might be the main reason for slow connectivity.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It may be partially a client side issue and should be addressed via the TAC.
That said with appropriate controls on the endpoint you don’t need to “route all traffic” back to your gateways.
To me, that seems like a much more scalable approach.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You don't mention your code version, make sure you are running at least R80.40 Jumbo HFA Take 53+ where major scalability improvements were added for Visitor Mode traffic. Do you know if your users are utilizing Visitor Mode?
Need to know your CoreXL split, and what does individual core utilization look like during busy periods on SND/IRQ vs Firewall Worker cores? Also need to see netstat -ni to ensure network interfaces are running cleanly without frame loss. Please provide output of Super Seven commands, ideally taken when Remote Access VPN traffic is high.
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can second that - Visitor mode can be an issue, see sk159372: Visitor Mode in Remote Access clients
Even with R80.40 Jumbo HFA Take 53, when the limitation on the maximum number of simultaneous Visitor Mode connections of 1024 was lifted, Visitor mode can only work by adding additional encapsulations to the traffic...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Timothy_Hall ,
We are running R80.30 Take 196.
NAT-T is enabled in VPN Clients > Remote Access, also as of checking now we have 1900+ users connected to RA VPN and only 3 users part of Visitor mode.
We had high CPU on the SND Cores before we enabled Multi-Queue (before June 2020), after we enabling Multi-Queue and adding more cores to the SND (currently 6 cores for Multi-Queue and 34 Cores for FW Workers) we have not seen SND's crossing above 60% CPU during peak hours.
I have attached all the outputs here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your firewall appears to be well-tuned and not struggling. Your issue kind of sounds like this SK, but your SNDs don't seem to be overloaded:
sk165853: High CPU usage on one CPU core when the number of Remote Access users is high
NAT-T should be getting handled in the kernel, but what does the CPU utilization of vpnd look like when things are slow? I'm wondering if some condition is forcing large amounts of RA VPN traffic to get handled by vpnd.
Beyond that, it could be some kind of low MTU issue in the network path causing issues with IPSec and the inability to fragment. Try forcing a slow client to use either Visitor Mode or NAT-T as specified here and see what happens: sk107433: How to change transport method with Endpoint Clients
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Timothy_Hall , @G_W_Albrecht , @_Val_ , @PhoneBoy ,
Thanks all for your help on this, we were able to get this fixed at last.
After working with about 6 Checkpoint Engineers from TAC and 8 hours of troubleshooting, we were able to identify, the culprit for this issue was the Multiple Interfaces option in VPN Clients which was checked.
Even though we only had a Single WAN Interface, the option was kept checked for a very long time (more than 2 years), but the impact was felt when covid started and large number of users migrated to Remote VPN.
The internet speed test was less than 2 Mbps when it was checked and it went upto 40 Mbps after this option was unchecked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great to know it is resolved! Thanks for sharing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Excellent news!
Curious, if you can say: Was this similar to the kernel parameter "fw ctl set int tunnel_test_do_in_kernel 1" ? (as in sk164933 and sk128652). Your stated solution to disable the probing for multiple interfaces seems to be similar to the effects of that kernel value. Perhaps Val could elucidate further.
Either way, congrats and I can imagine your collective relief!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello!
oh great thing ...
I know about this option, but on a new version like 81.10 and newest SmartConsole i dont find this setting anymore ...
where is it?
Does it only exists if the gateway has configured more then one external interfaces ?
Or has it been removed from the SmartConsole?
Maybe its now in the depths of GuiDBedit ...
perhaps somebody knows the answer 🙂
so i dont have this on my R81.10 enviroment ...
OLD
NEW
best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Tal_Paz-Fridman can you check into this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
any update ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, you seem to be pointing current stats however what is your past baseline? Have you tried to remove any traffic from the route 0 hub mode with sk167000 ( works really well ). Perhapss alleviating some O365 / Teams or whatever you want can help out with that SK. Are you using any sort of QoS ( either on chkp or elsewhere )?.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @514numbers ,
We have certain limitations in our environment for deploying the sk167000 as we have a set of users for whom outlook won't work if they are not connected to VPN (this was done for security reasons), also wanted to know if Checkpoint has a feature for creating multiple VPN profiles for Remote VPN (a feature which we used for Cisco ASA firewall) in this case we can have different settings for different group of users connecting to the same Gateway.
Regarding QoS we do have it enabled, I have shared the enabled_blades output in the initial Post.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 9 | |
| 5 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Tue 26 Nov 2024 @ 10:00 AM (CET)
EMEA Session: Automated Collaborative Prevention with 3rd Party Endpoint SolutionsTue 26 Nov 2024 @ 03:00 PM (CET)
Navigating NIS2: Practical Steps for Aligning Security and ComplianceTue 26 Nov 2024 @ 05:00 PM (CET)
Discover the Future of Cyber Security: What’s New in Check Point’s Quantum R82Tue 03 Dec 2024 @ 10:00 AM (GMT)
UK Community CNAPP Training Day 1: Cloud Risk Management WorkshopTue 03 Dec 2024 @ 05:00 PM (CET)
Americas CM Session: Automated Collaborative Prevention with 3rd Party Endpoint SolutionsTue 26 Nov 2024 @ 10:00 AM (CET)
EMEA Session: Automated Collaborative Prevention with 3rd Party Endpoint SolutionsTue 26 Nov 2024 @ 03:00 PM (CET)
Navigating NIS2: Practical Steps for Aligning Security and ComplianceTue 26 Nov 2024 @ 05:00 PM (CET)
Discover the Future of Cyber Security: What’s New in Check Point’s Quantum R82Tue 03 Dec 2024 @ 05:00 PM (CET)
Americas CM Session: Automated Collaborative Prevention with 3rd Party Endpoint SolutionsTue 03 Dec 2024 @ 10:00 AM (GMT)
UK Community CNAPP Training Day 1: Cloud Risk Management WorkshopWed 04 Dec 2024 @ 10:00 AM (GMT)
UK Community CNAPP Training Day 2: Cloud Risk Management WorkshopAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter