- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Hybrid Mesh
- :
- SASE and Remote Access
- :
- Checkpoint VPN with Microsoft 2-Factor Authenticat...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Checkpoint VPN with Microsoft 2-Factor Authentication
Hello everyone
I would like to share with you how I managed to get VPN users to use Microsoft Azure Multi-Factor Authentication.
I saw in some posts that this was possible by using MFA Server, but Microsoft stopped offering MFA Server on July 1, 2019.
What I needed to do:
1 - Office 365 users with MFA enabled.
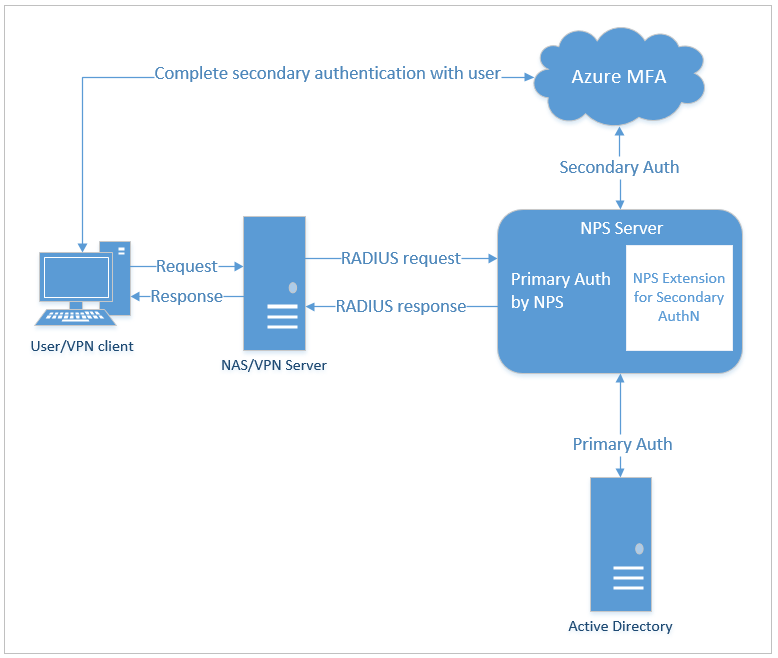
2 - Dedicated NPS Server.
All Radius requests made to this server will have MFA directed to Microsoft.
3 - NPS extension for Azure MFA
This extension will direct your MFA requests to Microsoft.
You can find the installation and download instructions at the link below.
The user can define which method will be used in the Microsoft portal.
I tested the methods below on VPN Clients, Mobile Access and Capsule Workspace and they all worked perfectly.
- Notification through mobile app
- Verification code from mobile app
- Text message to phone
I hope this post helps you
Good luck
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Everything I needed to configure the NPS server I found on the link https://docs.microsoft.com/pt-br/azure/active-directory/authentication/howto-mfa-nps-extension#sync-...
66 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Excellent!!!! Thank you for share.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for sharing.
Was any testing completed with 'Secondary Connect' in this configuration?
Just curious how it worked if tested.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
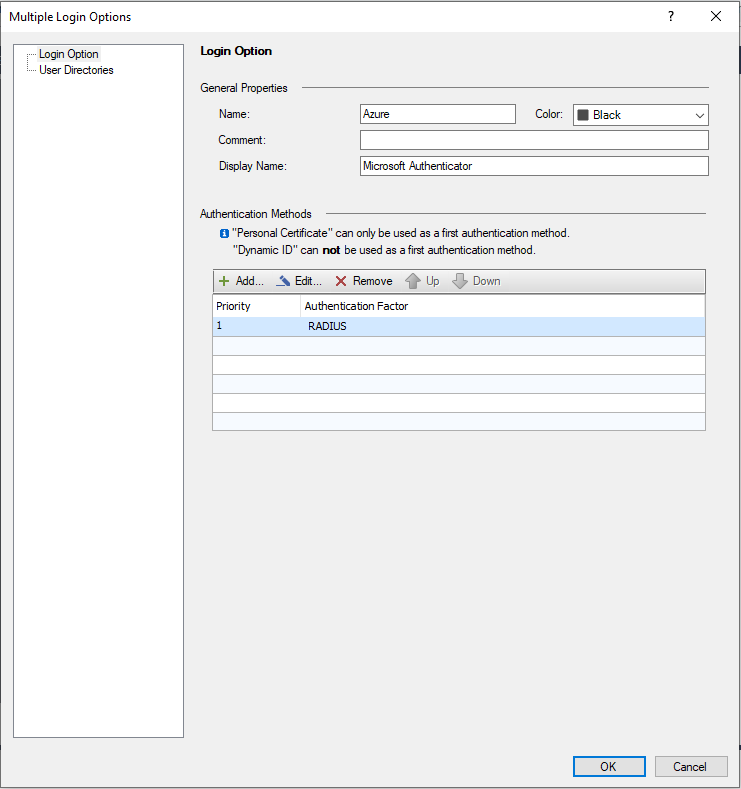
We currently use the Dynamic ID.
I created a new profile for testing Microsoft MFA.
When the user will connect he can choose which one to use.
After the tests we will keep only one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Rodrigo
As concerns Management server configuration for 2FA, can you please share it with us?
BR,
Kostas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You need to direct authentication to the Radius server.
You will need a Radius server with NPS extension for Azure MFA installed.
Remember that all requests to this Radius server will have MFA requests.
This setting is the same for Mobile Access.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Rodrigo:
I have a doubt. What kind of messages does the NPS send to the Firewall CheckPoint (VPN Server)? Is a Access-Challenge?
Regards,
Fabian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You may need to extend the RADIUS timeouts to allow for slower RADIUS responses because the end user needs extra time to satisfy the MFA response. SK112933 covers the configuration changes needed on the Management server, including the trac_client_1.ttm file used by the Endpoint suite clients.
Note that if you need to change the trac_client_1 file, you can set it in fwrl.conf to push it from management onto the gateways each time a policy is installed. Let me know if you need the specifics and I'll drop it into this post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Jason_Dance I have MFA working successfully with Microsoft Authenticator but not with SMS
Users trying SMS are challenged for the code but when they enter the code they receive via text message the authentication fails.
I think it may be the timeout issue.
I have looked at sk75221 and the trac_client_1.ttm file but I am not sure I understand what is required.
Are you able to post a copy of your working configuration?
I can see where to make the change on trac.defaults on the client but I am hoping to do this in one location and have it auto update all the clients when they next connect.
Thanks
Pedro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Pedro_Silva its been a while since I did it, but I remember having to roll out the trac_client_1.ttm file to the machines through our software deployment solution because it didn't come down from the gateway properly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Jason_Dance are you able to share the file contents? I found the documentation a little unclear as to the correct format.
Thanks
Pedro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Pedro,
did you solve SMS problem? i have same issue like you, everything works except SMS
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry, we have moved to another vendor and I can't find any notes about the solution we used. I do think it was a timeout issue.
Suggest contacting checkpoint support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks! Np! i have found solution ...
Make sure that the password encryption protocol between the NPS and NAS servers supports the secondary authentication method that you're using. PAP supports all the authentication methods of Azure AD MFA in the cloud: phone call, one-way text message, mobile app notification, and mobile app verification code. CHAPV2 and EAP support phone call and mobile app notification.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I wanted to get back to this question as I have got this working in the lab and have validated the results.
With Secondary Connect (transparently connect users to distributed resources) users get an MS Authenticator 'Approve' request every time the remote access client connects to another gateway.
So for sites that have Remote Access users relying on Secondary Connect to access resources distributed across the globe using the NPS Extension for Azure MFA is not the best user experience.
To my knowledge there is not a way to change the behavior of the NPS Extension so it will NOT send another request to Azure MFA if a previous authenticated session is already established.
Has anyone had a different experience with the setup of Secondary Connect and the NPS extension for Azure MFA?
Cheers!
--AJ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you ever end up finding a solution for secondary connect? We make heavy use of it as well
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for sharing this.
Moving it to the Remote Access space.
Moving it to the Remote Access space.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great info Rodrigo, did you have to do any specific configuration on the NPS server outside of getting the extension?
I've gotten a new AU configured with using Radius and cannot get a prompt for an MFA code.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Make sure you don't have any punctuation or special characters in your Radius Shared Secret.
A single ' caused my configuration to break. The NPS server was authenticating the user but then failing to pass the information back to the gateway.
My working configuration is:
RADIUS server object in Checkpoint Smart Console - configured for Radius Version 2.0 and MS_CHAP2
NPS server with Network Policy to Grant Access to AD User groups using matching Authentication Method.
On NPS Server you can see the authentication events in Event Viewer under Custom Views\Server Roles\Network Policy and Access Services
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Everything I needed to configure the NPS server I found on the link https://docs.microsoft.com/pt-br/azure/active-directory/authentication/howto-mfa-nps-extension#sync-...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Very helpful, thanks for sharing!
(Refer also sk114263)
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Configuring an External User Profile (generic*) with Radius authentication on SmartDashboard is still needed for this, right??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It depends on your policy. My configuration allows VPN connection by AD group. Regardless of whether it is per AD user, or per local user, authentication needs to be sent to the radius server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the documentation, could you say what you did on CheckPoint's side to make this work. We have been struggling the last few weeks to make this work, and haven't made any headway. I've configured the RADIUS server with the NPS extension, and we've setup RADIUS authentication on the gateway, but we keep getting a username/password error. Is there another way to set this up that will allow it to work? Would you mind sharing what your working setup looks like? We've been banging our head against the wall the last few weeks, and as you can tell it's starting to show. Appreciate any help that you can give.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm sorry for the late reply.
At CheckPoint I just needed to set up a new radius server and direct authentications to it.
You can even put MFA on who will connect to SmartConsole,
At CheckPoint I just needed to set up a new radius server and direct authentications to it.
You can even put MFA on who will connect to SmartConsole,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We cant get mobile app notification method to work!
Verification code and SMS to phone work fine!
Any ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you post steps for configuring for SMS to phone or Verification code? I've been struggling to get this to work at all!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1 - Your company must have at least one free Azure AD account, and your on-premises AD users must be in sync with the cloud.
2 - In the user's guide, on the office 365 portal, there is the option to manage the double factor of authentication. There you enable the double factor for each user.
3 - The user needs to access the portal.office.com website and complete the configuration.
I don't know if that was your question.
Hope this helps.
2 - In the user's guide, on the office 365 portal, there is the option to manage the double factor of authentication. There you enable the double factor for each user.
3 - The user needs to access the portal.office.com website and complete the configuration.
I don't know if that was your question.
Hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Check if you are having problems with HTTPS Inspection.
In our case it only worked on the 3G network. Then I found out that it was URL inspection.
Now everything works great.
In our case it only worked on the 3G network. Then I found out that it was URL inspection.
Now everything works great.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For anyone running across this thread when setting this up.
You may also need to make sure your RADIUS udp service doesn't have aggressive aging and set a custom virtual session timeout matching the timeout you want. In my case aggressive aging was timing out the UDP virtual session after 15 seconds then the UDP replies were getting blocked by firewall stealth rule and "radius servers not responding" was getting logged.
Checkpoint VPN with Microsoft 2-Factor Authentication
Hello everyone
I would like to share with you how I managed to get VPN users to use Microsoft Azure Multi-Factor Authentication.
I saw in some posts that this was possible by using MFA Server, but Microsoft stopped offering MFA Server on July 1, 2019.
What I needed to do:
1 - Office 365 users with MFA enabled.
2 - Dedicated NPS Server.
All Radius requests made to this server will have MFA directed to Microsoft.
3 - NPS extension for Azure MFA
This extension will direct your MFA requests to Microsoft.
You can find the installation and download instructions at the link below.
The user can define which method will be used in the Microsoft portal.
I tested the methods below on VPN Clients, Mobile Access and Capsule Workspace and they all worked perfectly.
- Notification through mobile app
- Verification code from mobile app
- Text message to phone
I hope this post helps you
Good luck
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 4 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Mon 23 Feb 2026 @ 11:00 AM (EST)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - AMERTue 24 Feb 2026 @ 10:00 AM (CET)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - EMEATue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANMon 23 Feb 2026 @ 11:00 AM (EST)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - AMERTue 24 Feb 2026 @ 10:00 AM (CET)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - EMEATue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Introducing Cyata, Securing the Agentic AI EraFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter