- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Re: C2S - Libreswan 3.23 (Roadwarrior) and R80.30 ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
C2S - Libreswan 3.23 (Roadwarrior) and R80.30 - working
******************************
WORKING RELEASES:
CentOS 8.0
Fedora 31
Mint 19.2
Ubuntu 18.04.03 LTS
Ubuntu 19.10
******************************
Before you begin, please make sure you have a working Remote Access environment using one of the Check Point Endpoint Clients (Windows / MacOS).
OfficeMode is not supported with Libreswan, therefore IP Pool NAT is needed (ex. sk39327).
This is a guide to connect a Linux VPN Client based on Libreswan to your Check Point environment, using certificates from the InternalCA.
Beginning with libreswan all certificates are stored in the NSS database, therefore we need all certificates (User and CP GW) in P12.
Linux Mint 19.2
1) Download the ISO Image linuxmint-19.2-cinnamon-64bit.iso which uses libreswan: 3.23 (netkey)
2) After Mint 19.2 Linux was installed, install the latest libreswan binary using
# sudo apt-get install libreswan
3) Initialize the NSS Database
# sudo ipsec initnss
4) check Database by running
# sudo certutil -L -d sql:/var/lib/ipsec/nss
Gateway / SmartCenter
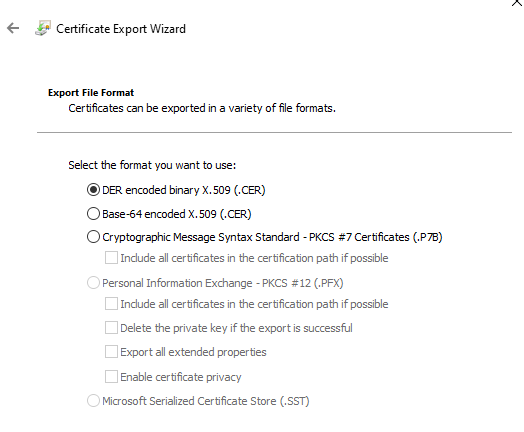
The first step is to export the Check Point VPN Gateway Certificate from the SmartCenter. Also create a local User in SmartDashboard and export the User p12 Certificate.
R80.30 Jumbo Take 191 - Standalone Firewall VPN Object: home-fw |
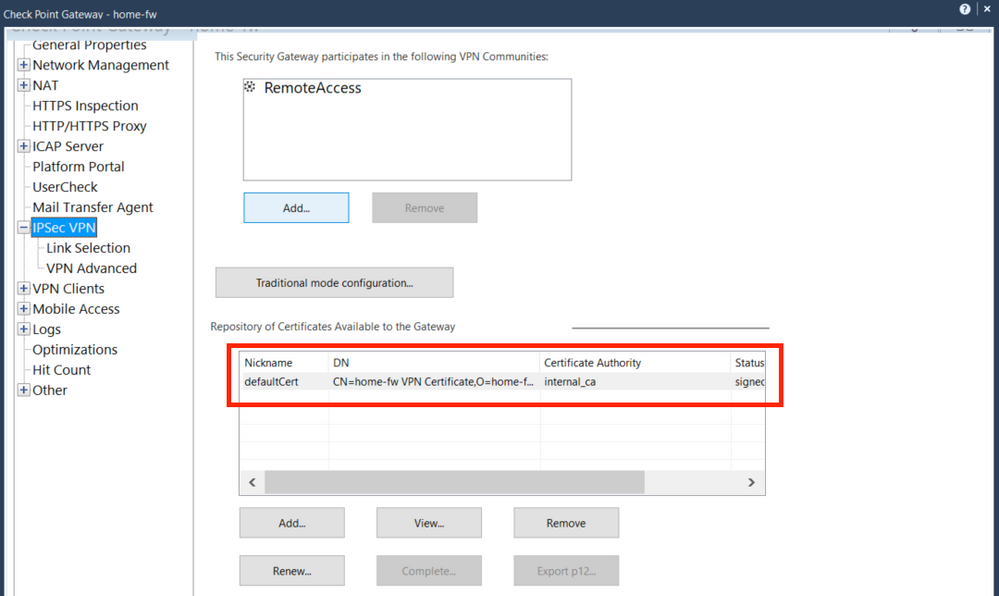
1) Export the Firewall p12 VPN Certificate (home-fw) from the SmartCenter. To check the Certificate name, open the FW object in SmartDashboard - IPSec VPN - Certificate Nickname (usually defaultCert).
Run in CLI (bash) on the SmartCenter:
Usage: export_p12 -obj <network object> -cert <certobj> -file <filename> -passwd <password>
Mgmt# export_p12 -obj home-fw -cert defaultCert -f home-fw.p12 -passwd 123456
A file named "home-fw.p12" will be generated. Copy this over to the Linux VM.
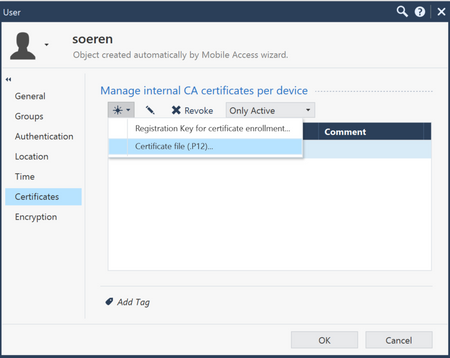
2)
In the User object create a p12 certificate and copy the file over to the Linux VM. For example: soeren.p12
Make sure that this user is part of the Remote Access community, you can check if the connections works with a Check Point VPN Client using Username / PW for example.
Linux Mint 19.2
Now it is time to import the certificates and to do the libreswan config
1)
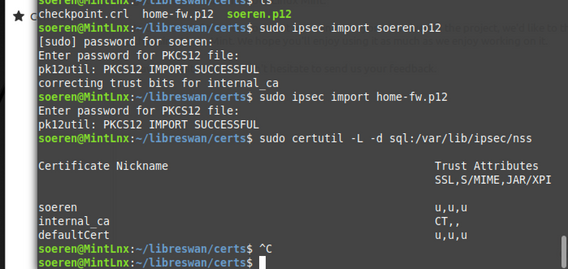
Both p12 certificates home-fw.p12 and soeren.p12 are imported using the command "ipsec import"
# sudo ipsec import home-fw.p12
# sudo ipsec import soeren.p12
The following command should display all certificates, also the Certificate Nicknames. The Nickname is important for the libreswan configuration later on.
# sudo certutil -L -d sql:/var/lib/ipsec/nss
# sudo certutil -L -d sql:/etc/ipsec.d # Fedora # CentOS
soeren.p12 uses the Certificate Nickname "soeren" and home-fw.p12 uses the Certificate Nickname "defaultCert".
2)
In /etc/ipsec.conf only enable the logging.
# sudo vi /etc/ipsec.conf # /etc/ipsec.conf - Libreswan IPsec configuration file
#
# Manual: ipsec.conf.5
config setup
# Normally, pluto logs via syslog. If you want to log to a file,
# specify below or to disable logging, eg for embedded systems, use
# the file name /dev/null
# Note: SElinux policies might prevent pluto writing to a log file at
# an unusual location.
logfile=/var/log/pluto.log
#
# Do not enable debug options to debug configuration issues!
#
# plutodebug "all", "none" or a combation from below:
# "raw crypt parsing emitting control controlmore kernel pfkey
# natt x509 dpd dns oppo oppoinfo private".
# Note: "private" is not included with "all", as it can show confidential
# information. It must be specifically specified
# examples:
# plutodebug="control parsing"
# plutodebug="all crypt"
# Again: only enable plutodebug when asked by a developer
# plutodebug=none
#
# NAT-TRAVERSAL support
# exclude networks used on server side by adding %v4:!a.b.c.0/24
# It seems that T-Mobile in the US and Rogers/Fido in Canada are
# using 25/8 as "private" address space on their wireless networks.
# This range has never been announced via BGP (at least up to 2015)
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12,%v4:25.0.0.0/8,%v4:100.64.0.0/10,%v6:fd00::/8,%v6:fe80::/10
# There is also a lot of information in the manual page, "man ipsec.conf"
#
# It is best to add your IPsec connections as separate files in /etc/ipsec.d/
include /etc/ipsec.d/*.conf
3) Create a new file called "ra.conf" and "ra.secrets" in /etc/ipsec.d/
#sudo touch /etc/ipsec.d/ra.conf
#sudo touch /etc/ipsec.d/ra.secrets
4) edit the /etc/ipsec.d/ra.conf file
#sudo vi /etc/ipsec.d/ra.confconn home
# Right side is libreswan - RoadWarrior
right=%defaultroute # or IP address of the Client
rightcert=soeren # Certificate Nickname of the users
rightid=%fromcert # Certificate ID
# Left side is Check Point
left=xxx.xxx.xxx.xxx # put here your Gateway IP Address
leftsubnet=192.168.0.0/24 # put here your company's network range or 0.0.0.0/0 for any
leftcert=defaultCert # Certificate Nickname of the CP GW
leftid=%fromcert # Certificate ID
# config
type=tunnel
keyingtries=3
disablearrivalcheck=no
authby=rsasig
#ike=aes256-sha1;modp1536 # force AES256, SHA1; DH5 in IKE Phase 1
#phase2alg=aes128-sha1 # force AES128, SHA1 in IKE Phase 2
ikelifetime=8h # IKE Lifetime 8h for IKE Phase P1
salifetime=1h # SA Lifetime 1h for IKE Phase P2
pfs=no # No PFS in IKE Phase 2
mtu=1400 # lower MTU size, if not, several Web Sites won't be accessible
ikev2=no # IKEv2 is not supported by Check Point in RemoteAccess
keyexchange=ike
auto=route
5) Start ipsec with systemctl
# systemctl enable ipsec
# systemctl start ipsec
# systemctl status ipsec (to check if ipsec was started successfully)
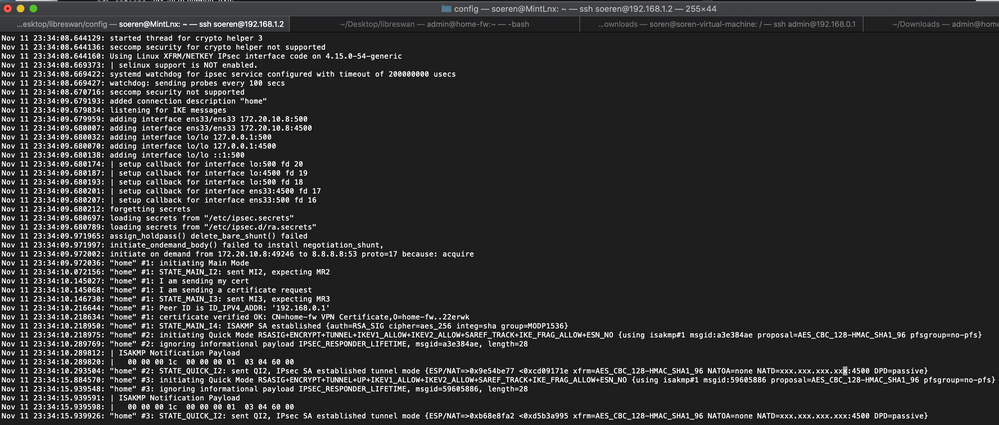
6) Initiate VPN connection to Check Point Gateway
# sudo ipsec auto --add home
# systemctl restart ipsec
# sudo ipsec auto --up home
Connection from Client was successfully initialized.
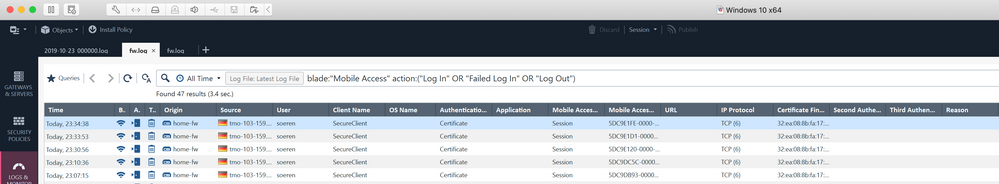
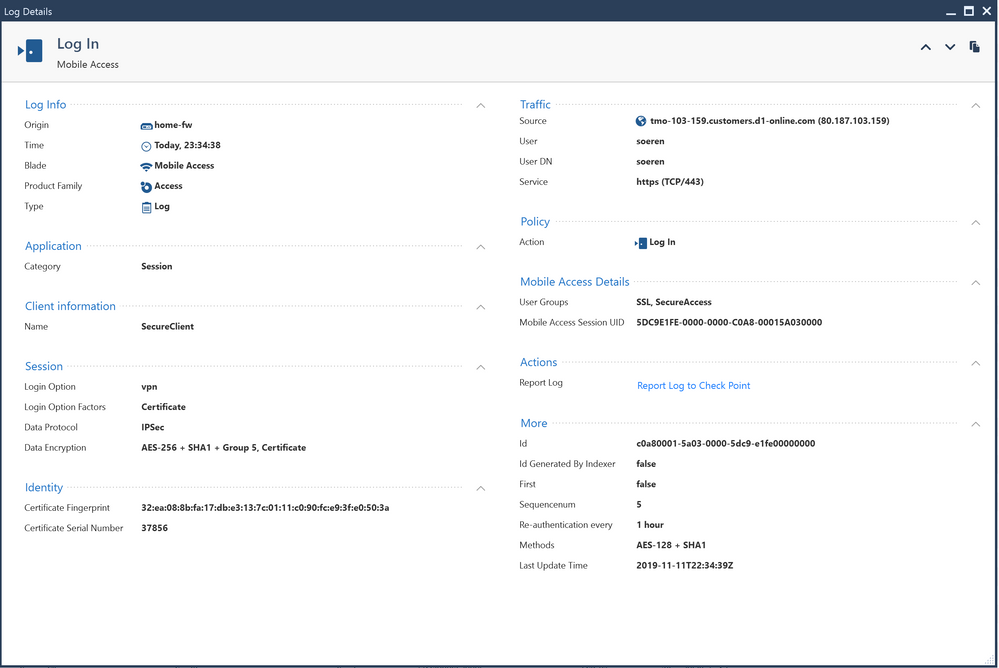
7 ) Logs from Check Point GUI
I still need to test DPD (Dead Peer Detection). If the VPN is removed from the CP side, the connection won't be re-established from libreswan.
23 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I know there is a plan to add official support for Freeswan at some point.
That said, this looks quite promising.
That said, this looks quite promising.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It also works on Fedora 31 and the latest libreswan 3.29.
1)
You must use ikev2=no, otherwise it won't connect. I updated the configuration example above
2)
The NSS Dabase is saved in /etc/ipsec.d. To check the database run:
# certutil -L -d sql:/etc/ipsec.d
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
On Linux Arch which is preferable? This or StrongSwan
https://community.checkpoint.com/t5/Remote-Access-Solutions/C2S-Libreswan-3-23-Roadwarrior-and-R80-3...
?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It looks like Linux Arch uses Libreswan 3.29 which works quite well in other Distributions. I would recommend Libreswan.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for posting this solution. Really appreciated.
I guess you did not use Office Mode (assigning an "intranet" IP address to the client), right?
I got it working with Office Mode (from the user point of view - SmartViewMonitor still says Office Mode = false) when I set the IP address the Windows client would get assigned by Office Mode in the leftsourceip field in ipsec.conf (in my config, left is the client side). But this is a static config. Getting the client IP from the gateway like the Windows or MacOS client does, would be much better. Assigning DNS servers and DNS search domains is a quite related problem.
Any ideas how to to this (without using PPP (in using L2TP over IPsec))?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tobi,
this works using IP Pool NAT under the Gateway Object.
*********
SmartDashboard - Gateway Object - NAT - IP Pool NAT - Use IP Pool NAT for VPN Clients only
*********
Let me look into the DNS problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the quick answer!
I cannot see this option in R80.30 SmartConsole on a R80.30 VPN gateway object (may its because we are using IPsec-VPN blade only and no Mobile Access blade?).
I can see the IP pool option in gateway object -> IPSec VPN -> Office Mode and it is set to Manual (using ip pool). This works fine for the windows and macos clients, they are getting addresses from this range.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
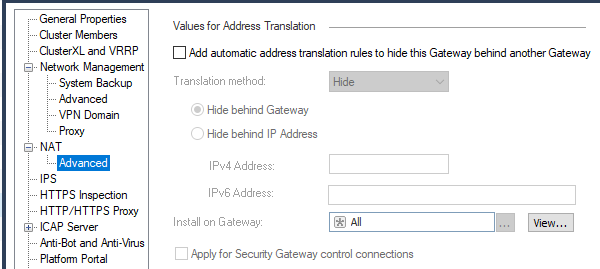
You have to enable IP Pool NAT in Global Properties:
*************
Global Properties - NAT Network Address Translation - Enable IP Pool NAT
*************
After you enabled it, you can use it under the Gateway Object.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you, I was missing this master switch for the IP NAT Pool feature.
Using the IP NAT Pool feature is a really good idea to overcome the problem, that libreswan seems to be unable to aquire the Office Mode IP address from the gateway like the proprietary client does.
However, do you know how this interfers with Office Mode for the proprietary client? Can there be a conflict, when using the same network for Office Mode ip assignment and IP NAT Pool for VPN clients? What is happening with static assignments from $FWDIR/conf/ipassignment.conf? I know the last one is preferred over the Office Mode pool, but how will this been put in order with IP NAT Pool?
I would suspect that the IP NAT Pool feature will just NAT all VPN clients traffic, not taking care which IP address they are using inside the tunnel (Office Mode from static assigment, Office Mode from pool or the orginal client IP address when Office Mode is not used (like with libreswan)). As result, this would break the static assignment of static IP addresses to rich clients using ipassignment.conf.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In my setup I use Office Mode and IP Pool NAT for Clients. It works in parallel.
For example:
- Libreswan -> IP Pool NAT
- Endpoint SecuRemote -> IP Pool NAT (as far as I remember)
- Capsule Connect iOS -> Office Mode
- L2TP Linux Client -> Office Mode
- Endpoint macOS -> Office Mode
- Endpoint Windows -> Office Mode
ipassignment.conf comes only in place when Office Mode is used, so I don't see any problem if you use all these features at the same time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm getting the following error in the client: ignoring informational payload INVALID_ID_INFORMATION, msgid=00000000, length=12
and this one in the smartconsole: Main Mode Sent Notification to Peer: invalid id information
Any ideas?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
t´s not work on RHL8 or RHL Workstation ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am sure it works, because I tried it on CentOS which is very similar to RHL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried to follow this guide, but have difficulties in fitting the instructions to my situation.
From Windows I can connect to a CheckPoint VPN with CheckPoint Endpoint Security VPN client.
The only data I was given are:
- A VPN Site IP
- One .p12 certificate file
- user
- password
I know nothing about the SmartCenter or SmartDashboard; I just have one .p12 file, while this guide refers to two .p12 files.
More specifically I suppose my .p12 certificate corresponds to the soeren.p12 in the guide, but I don't know how to obtain the other .p12 file (correspondent to home-fw.p12 I suppose).
Is there a chance that I can fit this guide to reach my goal, that is, connecting to the same VPN from Linux with LibreSwan even without this second .p12 file ?
Thank you very much
Vincenzo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your gateway administrator would have to provide this file as it is an export of the relevant gateway's public VPN certificate.
This is not required for official Check Point clients, but it is required for this particular third party client.
This is not required for official Check Point clients, but it is required for this particular third party client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
thank you!
I don't have the chance to contact of the gateway admin, but I'm guessing:
1) does the Gateway corresponds to the IP VPN server I am given for the connection?
2) assuming yes for the previous point, if I point my browser to the IP in HTTPS I see that the site has a certificate: is it this that I would own? In this case which export format should I choose?
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Generally, yes, but no, you cannot get it from the web browser.
The certificate that might be available via a web browser is different from the VPN certificate.
The only way to obtain this is from your administrator.
The certificate that might be available via a web browser is different from the VPN certificate.
The only way to obtain this is from your administrator.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A question. When the site administrator generates the p12 certificate, has he to use the password of the private key? Or is he exporting the public key with a new password? (the first case would be a serious security concern!). Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for sharing, can someone guide me what I am doing wrong? I am getting NO_PRPOSAL_CHOSEN, please see below
002 "home" #4: initiating Main Mode 104 "home" #4: STATE_MAIN_I1: initiate 003 "home" #4: ignoring informational payload NO_PROPOSAL_CHOSEN, msgid=00000000, length=12 003 "home" #4: received and ignored notification payload: NO_PROPOSAL_CHOSEN 010 "home" #4: STATE_MAIN_I1: retransmission; will wait 0.5 seconds for response 010 "home" #4: STATE_MAIN_I1: retransmission; will wait 1 seconds for response 010 "home" #4: STATE_MAIN_I1: retransmission; will wait 2 seconds for response
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am getting following rejection on CheckPoint log: Main Mode Failed to match proposal:AES-128, SHA1, Certificate, Group 5 (1536 bit);
Which settings should I modify?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You could change the settings in Global Properties - Remote Access - VPN Authentication - Encryption Algorithm to allow more algorithms.
or you could change the settings in libreswan to match the actual settings of your Check Point Firewall.
ike=aes128-sha1;modp1536
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you very much, I did manage to connect, but It I get stuck after connect. Any proposal what could be wrong? See log below
ar 13 20:52:27.509522: "x" #1: initiating Main Mode
Mar 13 20:52:27.527734: "x" #1: STATE_MAIN_I2: sent MI2, expecting MR2
Mar 13 20:52:27.549413: "x" #1: I am sending my cert
Mar 13 20:52:27.549450: "x" #1: I am sending a certificate request
Mar 13 20:52:27.567464: "x" #1: STATE_MAIN_I3: sent MI3, expecting MR3
Mar 13 20:52:27.599959: "x" #1: Peer ID is ID_IPV4_ADDR: '....'
Mar 13 20:52:27.600004: "x" #1: loading root certificate cache
Mar 13 20:52:27.603443: "x" #1: certificate verified OK: CN=xfw VPN Certificate,O=checkpointmgmt.checkpointmgmt.8pkvbf
Mar 13 20:52:27.604121: "x" #1: Authenticated using RSA
Mar 13 20:52:27.604298: "x" #1: STATE_MAIN_I4: ISAKMP SA established {auth=RSA_SIG cipher=AES_CBC_256 integ=HMAC_SHA1 group=MODP1536}
Mar 13 20:52:27.604344: "x" #2: initiating Quick Mode RSASIG+ENCRYPT+TUNNEL+IKEV1_ALLOW+SAREF_TRACK+IKE_FRAG_ALLOW+ESN_NO {using isakmp#1 msgid:efd0b9ac proposal=AES_CBC_128-HMAC_SHA1_96 pfsgroup=no-pfs}
Mar 13 20:52:27.642980: "x" #2: STATE_QUICK_I2: sent QI2, IPsec SA established tunnel mode {ESP/NAT=>0xe9ee1d3e <0xc09a579f xfrm=AES_CBC_128-HMAC_SHA1_96 NATOA=none NATD=.....:4500 DPD=passive}- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The client is connected, it is fine. You can also check this in your logs. Probably you need to enable IP Pool NAT too, see description above. Also the client should not be in the same network range like your Encryption Domain.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter