- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E5:
Powering Prevention: The AI Driving Check Point’s ThreatCloud
The Great Exposure Reset
AI Security Masters E4:
Introducing Cyata, Securing the Agentic AI Era
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Hybrid Mesh
- :
- SASE and Remote Access
- :
- Re: Azure SAML Auth - forceAuthn=true
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Azure SAML Auth - forceAuthn=true
A drawback to SAML auth is that when connecting to VPN it just logs you straight in - no further auth needed (assuming your machine/browser is already logged into your MS365 account).
For some this is fine. For others it isn't, and they still want to be prompted for some credentials when logging into VPN.
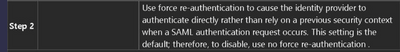
There's a nice little hack to the /opt/CPSamlPortal/phpincs/simplesamlphp/config/authsources.php file, to set
forceAuthn=true
This forces you to do a full login every time. I.e. manually typing your username, password, then responding to MFA. At the end of the sign-in you get the box to save details so you don't have to enter them every time. But that effectively does nothing. Next time you log in, you still have to do the entire authentication bit again.
But that's what I just set in the file above, so what's the problem?
Does anybody know of a way to achieve a halfway house on this? For example, rather than manually having to type my email & password every time, is there an option available to JUST prompt for the MFA on each login?
I've got several customers using this. They're not happy without "forceAuthn=true" because they get no prompts at all. But they're also not happy with having to manually type the email & password every time either. They just want the MFA bit. Is there a way??
I thought the problem of having to manually enter full credentials every time was linked to the SAML pop-up window not using the machine browser's cached info. I was hoping that E87.30 (using the machine default browser) would fix this and remember who is logged in, therefore only prompting for MFA, but it doesn't 😞
Does anyone know any tricks to make VPN login prompt every time for MFA, without requiring the full username/password too?
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
https://support.checkpoint.com/results/sk/sk180948
Checkpoint released an SK article about this parameter.
This file can be found on any Main line gateway.
SMB devices do not support SAML at this time.
22 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If its something like below:
...then answer is no, CP does not have this ability and Sales told me last year that this would be RFE. So, to expand on it, without boring you with the whole story, here is the jist of it. Customer wanted their users to be forced to re-authenticate, even if they put their laptops to sleep and came back 45 seconds later and CP VPN solution cant do that currently.
Best,
Andy
"Have a great day and if its not, change it"
Andy
"Have a great day and if its not, change it"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well... the forceAuthn=true line in the config file absolutely does this. Tested over and over again. 100%. Log out, then immediately log back in and you're prompted again for creds. So that bit is fine and works well.
With forceAuthn=false (or just without the line in the config file at all - the default unless you've specifically updated the file) then is does the normal SSO and logs you straight it without any further prompting for creds or authentication.
So we have both extremes here.
What my customers want is something in the middle. They don't want to have to enter the full creds every time, BUT they do want to be prompted for the MFA bit (e.g. Microsoft Authenticator pop-up on their phone). It seems this half-way option is not currently possible? Unless anyone knows how it can be done? Maybe it's an Azure setting rather than a firewall thing, but if it is, I don't currently know it, and would love to be enlightened 😁😁
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A kk, thats good to know, because nothing of sort worked for that a year ago, thats great info @biskit . I dont believe what your customer wants might be possible, unless there is some syntax for it on Azure side? Not sure...
Andy
Best,
Andy
"Have a great day and if its not, change it"
Andy
"Have a great day and if its not, change it"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The way SAML works is that we initiate the connection to the IdP, which authenticates the user and sends us a SAML assertion about the relevant user.
The authentication flow happens entirely in the IdP.
The only way we can influence this is by sending forceAuthn=true to tell the remote end not to reuse the existing session, thus going through the full authentication flow.
If you want a different authentication flow, this needs to be configured on the IdP itself.
Whether the IdP supports your desired authentication flow is a separate question.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I cannot find forceAuthn=true anywhere in /opt/CPSamlPortal/phpincs/simplesamlphp/config/authsources.php
First and foremost is this setup on SMS or on GWs ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is set up on the gateway (where the authentication takes place).
While it is possible to make this configuration change, it is UNSUPPORTED and currently documented in an internal SK.
Please consult with the TAC: https://help.checkpoint.com
The correct (and proper, supported) place to configure this is on the IdP itself.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
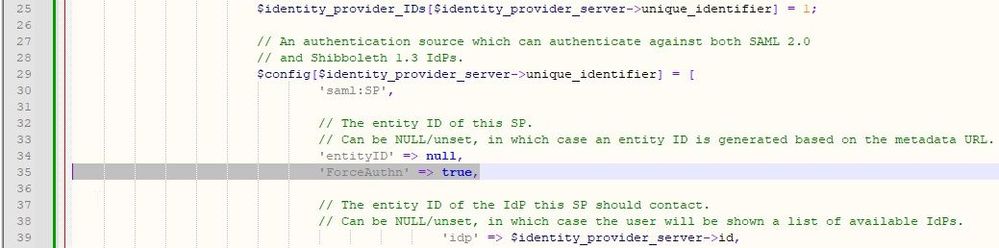
you need to add it manually
// The entity ID of this SP.
// Can be NULL/unset, in which case an entity ID is generated based on the metadata URL.
'entityID' => null,
'ForceAuthn' => true,
// The entity ID of the IdP this SP should contact.
// Can be NULL/unset, in which case the user will be shown a list of available IdPs.
'idp' => $identity_provider_server->id,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
https://support.checkpoint.com/results/sk/sk180948
Checkpoint released an SK article about this parameter.
This file can be found on any Main line gateway.
SMB devices do not support SAML at this time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for finally getting this in SK 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I know this is bit old thread, but still make a rise for this great article.
I can confirm this also really works greatly with sparks in local conf and smart 1 cloud.
Still I am missing attribute or configuration option that would do logout from M365 when we disconnect vpnclient so that the session would not be still on, even though it wont effect this because this forceauthn still requires to reauth.
Br.Tunish
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @biskit , where did you put that string?
I' ve checked the file but I don't know where it should be set.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Open /opt/CPSamlPortal/phpincs/simplesamlphp/config/authsources.php in Notepad++
Insert new line at line 35
'ForceAuthn' => true,
Your file should then look like this:
CP told me it needed a cpstop/cpstart, but I've found it just works on the fly.
Just to reiterate what Phoneboy said - this was given to me by TAC to "try" and is not a supported solution. Backup your file before you start playing 8)
This is a global setting and will force all users to enter their AAD password every time (and then AAD MFA if it's configured). My users get very sick of this very quickly as their AAD passwords are half a mile long. The issue of only prompting for MFA each time (and not the whole password too) is a failing of Azure IDP, not Check Point. If any Azure wizards find a way around this, pleeeease let me know!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Again, the proper, correct place to configure re-authentication requirements in the IdP.
Consult with your IdP vendor for the exact steps required to do this.
The forceAuthn=true is a "workaround" that doesn't work with all IdPs and, as you described, has other side effects.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The issue is with how SAML works with a SP and a IDP.
if you configured the SP to send the Force auth. This tells the IDP to redo auth each time, thus eliminating SAML as a single sign on feature, into a normal Auth method.
This ForceAuthn parameter is a custom SAML parameter that can be used by (SP) service providers to present to (IDP) Identity Providers.
I have found that some IDP's allow it, and some that ignore it, as ForceAuthn is a optional parameter.
But Checkpoint does not handle the 2nd factor in this scenario.
The IDP vender is doing an additional Factor on their end.
Thus this would fall under their action and not checkpoint.
If the IDP vender could allow the SSO for SAML, but force the MFA aspect, then that would be what you are looking for.
I would see about if the Vender of the IDP has anything they can enable for there side.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just a wee follow up on this - I have managed to get the client to request password and MFA through Azure IDP. I know this is not just MFA as needed yet just password & MFA works pretty well. Using "Conditional Access" within the enterprise application with a few tweaks helped me get there. If the client is running it lets the user reconnect, yet if you shutdown the client or reboot your laptop it will for a reauth.
If this is of any use to anyone I can fully document my work and share here 🙂 Might be a specific use case but thats certianly what we were looking for.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you could share what you did, I think it would be extremely helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @phate_82 ,
it would be great to share your work here, because I think, thats just what my customer wants, what you have implemented.
I cannot use
forceAuthn=true
because the customer runs on a VSX and that would compromise all other users.
I couldn't find the file /opt/CPSamlPortal/phpincs/simplesamlphp/config/authsources.php in any subdirectory of any CMA to make it work only for this customer.
Thanks in advance
Christian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a gateway side edit, which is probably why this is the case.
Seeing this per VS would likely be an RFE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Add me to the list - please share what you've done - I've been trying different Conditional Access settings with no success as of yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you explain or anyone else what you did in Azure Checkpoint App so user need to enter their MFA each time. Thanks !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you are on R81.20 jhf 89 or higher, please follow https://support.checkpoint.com/results/sk/sk180948
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As I am not a fan of supported configurations. Wondering if you have a solution here it seems many are looking forward to it. Feels like work we have been doing is close but still not functional.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 4 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 12 Mar 2026 @ 05:00 PM (CET)
AI Security Masters Session 5: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 12 Mar 2026 @ 05:00 PM (CET)
AI Security Masters Session 5: Powering Prevention: The AI Driving Check Point’s ThreatCloudTue 17 Mar 2026 @ 03:00 PM (CET)
From SASE to Hybrid Mesh: Securing Enterprise AI at Scale - EMEATue 17 Mar 2026 @ 02:00 PM (EDT)
From SASE to Hybrid Mesh: Securing Enterprise AI at Scale - AMERTue 24 Mar 2026 @ 06:00 PM (COT)
San Pedro Sula: Spark Firewall y AI-Powered Security ManagementThu 26 Mar 2026 @ 06:00 PM (COT)
Tegucigalpa: Spark Firewall y AI-Powered Security ManagementAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter