- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure the Workspace)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Mastering Endpoint Security -
Best Practices for 2024
Check Point Named Leader
In Mobile Threat Defense
Regulatory Compliance Update
For Non-US DoC Versions
Customer Threat Prevention
& Vulnerability Management Survey
CheckMates Toolbox Contest 2024
Make Your Submission for a Chance to WIN up to $300 Gift Card!
CheckMates Go:
Identity Awareness Best Practices
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Remote Access VPN
- :
- Endpoint VPN DNS Headbender
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Endpoint VPN DNS Headbender
OK. I am officially crying "uncle" and am asking for your advise.
In the process of setting up a demo lab for the client to demonstrate the various remote access options, I've run into this situation:
Endpoint connects to the gateway in a hub mode and TCP traffic is working fine, (i.e. no problem establishing RDP sessions).
The DNS however, does not.
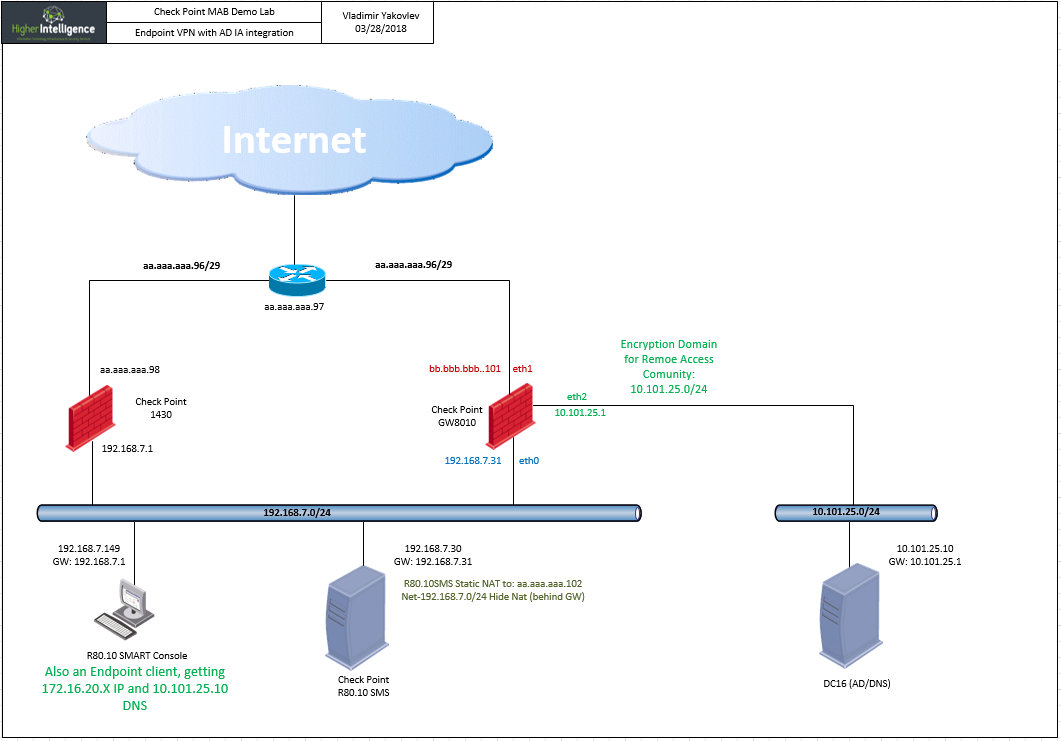
Latest findings indicate that disabling SecureXL makes this problem go away.
According to the client, dns queries are being send to a correct remote server:
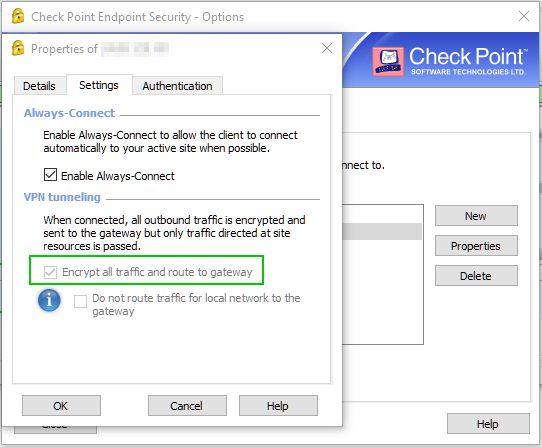
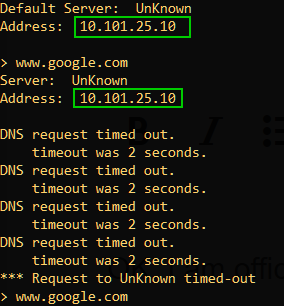
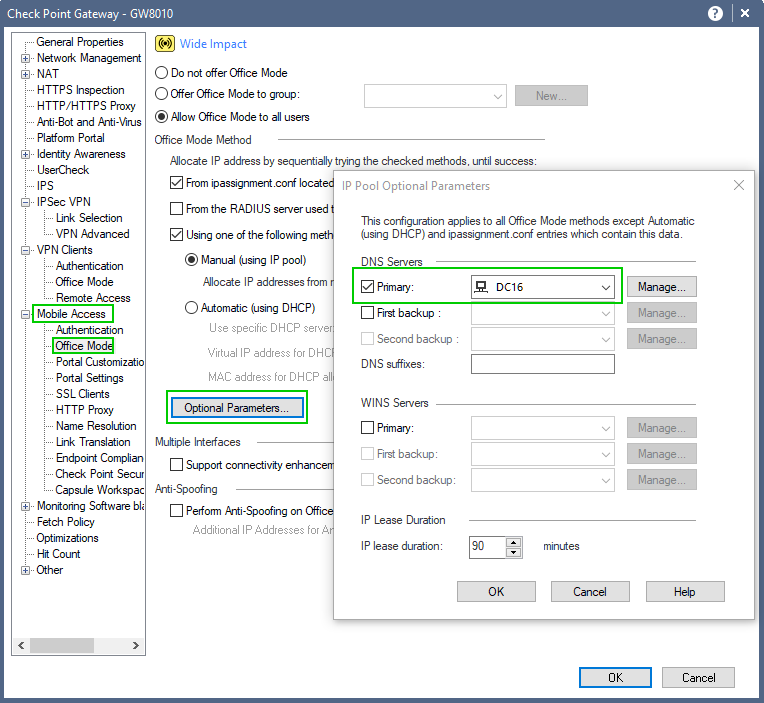
This is the DNS server configured in the Office Mode Optional Parameters:
Packet capture on the client seem to suggest that all is well:
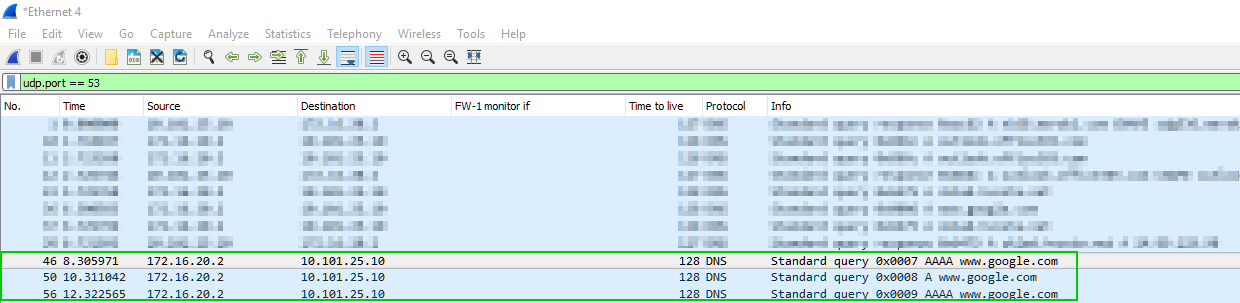
But the firewall, after encrypting session claims that the queries are being addressed to another IP (client's WiFi DNS):

Session:
Time: 2018-03-28T16:05:42Z
Interface Direction: inbound
Interface Name: eth1
Connection Direction: Incoming
Id: c0a8071f-2116-0000-5abb-bd5600000000
Sequencenum: 1
Hll Key: 11932664019562776808
Duration: 60
Last Update Time: 2018-03-28T16:06:39Z
Update Count: 2
Connections: 21
Aggregated Log Count: 34
Creation Time: 2018-03-28T16:05:42Z
Source: 172.16.20.2
Destination: 10.101.25.10
Destination Port: 53
IP Protocol: 17
User: ADUser1 (aduser1)
Source User Name: ADUser1 (aduser1)
Src User Dn: CN=ADUser1,CN=Users,DC=higherintelligence,DC=com
Destination Machine Name:dc16@higherintelligence.com
Service ID: domain-udp
Source Zone: External
Destination Zone: Internal
Action: Decrypt
Type: Session
Policy Name: MobileAccess_for_GW8010
Policy Management: SMS8010
Db Tag: {C961B499-D18A-6E48-B9D9-09023460FFBE}
Policy Date: 2018-03-28T13:44:48Z
Blade: Firewall
Origin: GW8010
Service: UDP/53
Product Family: Access
Logid: 288
Marker: @A@@B@1522209601@C@93556
Log Server Origin: 192.168.7.30
Orig Log Server Ip: 192.168.7.30
Lastupdatetime: 1522253202000
Lastupdateseqnum: 1
Severity: Informational
Rounded Sent Bytes: 1600
Confidence Level: N/A
Rounded Bytes: 9968
Stored: true
Rounded Received Bytes: 3568
Packets: 46
Total Bytes: 9981
Client Inbound Packets: 23
Client Outbound Packets: 23
Server Inbound Packets: 23
Server Outbound Packets: 23
Client Inbound Bytes: 3008
Client Outbound Bytes: 6973
Server Inbound Bytes: 3569
Server Outbound Bytes: 1600
Received Bytes: 3569
Sent Bytes: 1600
Access Rule Name: MAB Access to DC
Access Rule Number: 9.3
Rule UID: 69d6915f-7f98-4f28-9bf8-e9338d879611
Layer Name: Inline_FW_MAB
Interface: eth1
Description: domain-udp Traffic Decrypted from ADUser1 (aduser1)(172.16.20.2) to 10.101.25.10
Layer Uuid Rule Uuid: 9457d7fd-104e-494a-bf23-522eae8d2530_b84bc8fb-5623-47d2-9b6a-2fd8d54988a4, 05184d6c-b55e-4fc2-bb2c-8a8b5dd8d213_69d6915f-7f98-4f28-9bf8-e9338d879611
Bytes (sent\received): 9.7 KB (1.6 KB \ 3.5 KB)
Drops:
Id: c0a8071e-2091-a809-5abb-bd6233fb0003
Marker: @A@@B@1522209601@C@93320
Log Server Origin: 192.168.7.30
Time: 2018-03-28T16:05:54Z
Interface Direction: inbound
Interface Name: eth1
Id Generated By Indexer:false
First: true
Sequencenum: 4
Source Zone: External
Destination Zone: Internal
Service ID: domain-udp
Source: 172.16.20.2
Source Port: 55011
Destination: 192.168.7.1
Destination Port: 53
IP Protocol: 17
User: ADUser1 (aduser1)
Source User Name: ADUser1 (aduser1)
Src User Dn: CN=ADUser1,CN=Users,DC=higherintelligence,DC=com
Action: Drop
Type: Connection
Policy Name: MobileAccess_for_GW8010
Policy Management: SMS8010
Db Tag: {C961B499-D18A-6E48-B9D9-09023460FFBE}
Policy Date: 2018-03-28T13:44:48Z
Blade: Firewall
Origin: GW8010
Service: UDP/53
Product Family: Access
Logid: 0
Access Rule Name: MAB Layer Cleanup rule
Access Rule Number: 9.6
Rule UID: 7ec99f73-e125-4ac3-8882-f342d8c518c0
Layer Name: Inline_FW_MAB
Interface: eth1
Description: domain-udp Traffic Dropped from ADUser1 (aduser1)(172.16.20.2) to 192.168.7.1
I am aware of the Windows 10 DNS leakage issues and have addressed those, but this does not look like it, as the queries being actually forwarded to the gateway and not blasted out of Wi-Fi.
I'll collect and attach the trac.log from the Endpoint VPN client later if you want to take a look at it.
Thank you,
Vladimir
- Tags:
- dns
- endpoint vpn
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Looking at timestamps, there's 12 secs between DNS request to the "right" DNS and the "wrong" one I would guess client didn't receive response to the first request so it started trying any DNS it can find on any other interface, resulting in using WiFi DNS. Probably windows behaviour. Check if first request was forwarded to DNS and response arrived to DNS OK. Hope you understood where I'm trying to get to
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Fairly short thread with some answers
Windows 10 DNS resolution via VPN connection not working - Super User
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've seen this, but it is not a viable solution, as each new Wi-Fi connection resets metric on adapter.
By design, Windows 10 will blast DNS requests to any and all connections that have DNS registered with them simultaneously and use the results that have arrived fastest.
So if you have a non split-brain DNS for your domain and are trying to access internal resources (that are also have public records) via VPN, you are kind-of out of luck.
In my case, it is attempting to query Wi-Fi's DNS, but those requests are encapsulated and shoved through the VPN.
May have something to do with the topology of the lab.
Let me run the wireshark on DC and see what it is seeing in terms of the query origin.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't really have much experience with remote clients, but these SKs offer some possibilities to try or at least check:
DNS Query on VPN client with Office Mode IP address takes a very long time to succeed
Endpoint Security VPN client using local DNS server before using its assigned Office Mode DNS
DNS does not work through VPN tunnels
But I suspect that you already read all SKs found by search "DNS VPN".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for suggestions.
I have read those and much more on the subject than I care to admit:)
First, the sk103678 is in compliance.
Second, the sk103455 is in compliance.
Third, the sk62483 is in compliance.
But the plot thickens: Disabling SecureXL makes the DNS traversal work as expected.
Does this new revelation ring any bells?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's probably worth a TAC case if disabling SecureXL solves the issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am having problems opening POC cases with TAC, as the account that I am using with NFR licenses does not have active CP support.
At some point, I may have to ask you to associate my Checkmates account with my own email, since I myself maintain active support contract.
I am just concerned about possible confusion it may cause, since the my current Checkmates account and email is the one that it assigned to a bunch of clients as a technical support contact.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unfortunately, the identifier for CheckMates accounts is based on your UserCenter account and I don't have a way to affect that.
I know who you are, though--no confusion on my end ![]()
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 25 Jul 2024 @ 11:00 AM (EDT)
CP Tips and Tricks 2024 #12: Dynamic Access Policies using Data Center ObjectsThu 01 Aug 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: What's new on Check Point CloudGuard!Tue 06 Aug 2024 @ 05:00 PM (CEST)
Americas CheckMates Live - Infinity XDR/XPR Q2 Product UpdatesThu 25 Jul 2024 @ 11:00 AM (EDT)
CP Tips and Tricks 2024 #12: Dynamic Access Policies using Data Center ObjectsThu 01 Aug 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: What's new on Check Point CloudGuard!Tue 06 Aug 2024 @ 05:00 PM (CEST)
Americas CheckMates Live - Infinity XDR/XPR Q2 Product UpdatesAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


