- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
The Great Exposure Reset
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Product Announcements
- :
- SourceGuard - Source Code Security and Risk Analys...
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
SourceGuard - Source Code Security and Risk Analysis
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
2019-12-30
12:07 PM
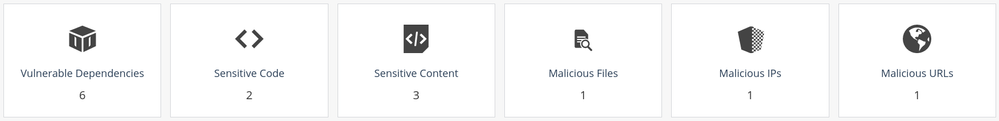
As developers we are all in charge of the security of our code. here at Check Point we have some strict policies requiring developers to go through review processes to make sure their code is secure from dependencies and other vulnerabilities.
With the transition to SaaS based development and continuous delivery, the need to run this review process quickly and automatically while making sure our code is secure and safe for use, brought us to develop an in-house tool designed to help our developers with source code security automation.
With the common use of 3rd party generated code, which may originate from different sources such as libraries, SDKs and other dependencies, an automatic vulnerability detection and remediation is required, which runs during and after the CI/CD pipeline in order to prevent threats that were discovered after deployment, as well as use new detection capabilities in retrospect.
The many incidents we have encountered of customers accidentally exposing keys, passwords and other secrets in their code, and eventually falling victim to instances abuse in their public cloud accounts by cryptominers, as well as being vulnerable due to use of vulnerable resources, is what encouraged us to open SourceGuard poc to a wider developer/DevSecOps community and external users to experiment with.
now available at: Check Point Infinity Portal
we welcome feedback and participation. big traction and significant usage, will help turn this from poc into formal solution.
Built By Developers – For Developers
SourceGuard is designed to leverage Check Point's different prevention technologies and services, providing source-code security and visibility into the risk analysis of projects. With a simple, cross-platform CLI tool (Docker: sourceguard/sourceguard-cli:latest), users can customize exclusions and control ignore list (such as testdata and others) with easy integration to any pipeline.
Getting started:
- Register, activate and login at:Check Point Infinity Portal
- From the available services menu, choose “SourceGuard” and hit “Try Now”.
- Download and install SourceGuard CLI according to your OS.
- Generate token, copy and save it.
- Scan a project by running: sourceguard-cli --src <project path>
6 Comments
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter