- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Fest 2025!
Join the Biggest Event of the Year!
Simplifying Zero Trust Security
with Infinity Identity!
Operational Health Monitoring
Help us with the Short-Term Roadmap
CheckMates Go:
Recently on CheckMates
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Product Announcements
- :
- Endpoint Security / SandBlast Agent Newsletter - V...
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Endpoint Security / SandBlast Agent Newsletter - Version E83.20
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
2020-08-27
08:29 AM
Hi all,
We are happy to announce the release of Endpoint Security Client E83.20.
The complete list of improvements can be found in the version release’s Secure Knowledge sk168081.
But here are the most exciting ones…
New windows support
E83.20 has full support (all blades and packages) for Windows 10 20H1 (version 2004)
Browser Extension support Microsoft Edge (Chromium) & Chrome for Mac
SandBlast Agent Browser Extension now supports Microsoft Edge (Chromium) and Chrome for Mac with the following capabilities:
- URL Filtering (WebUI only)
- File Download Protection
- Credential Theft protection including Zero-Phishing and Corporate-password-reuse protection
The extension is installed automatically together with the new version
Supported & Next To Come:
E83.20 for macOS
The version supports the following capabilities:
- Anti-Malware blade is now GA
- URL Filtering with SandBlast Agent Chrome Browser Extension
- Advanced VPN features are now also available on Mac:
- Multiple Factor Authentication
- Multiple Entry Point
- Implicit Mode
- Secondary Connect
Follow sk166955 for more information on the E83.20 release for macOS.
New advanced protections
- "Pass The Hash" detection in Behavioral Guard has been enhanced, to recognize more “Pass The Hash” attempts.
Pass The Hash is used by an attacker to do remote authentication by utilizing the hash of an account password. In other words, the attacker does not need the actual plaintext password.
This technique in essence allows for lateral movement in an organization. - Improved malicious LNK files detection
Behavioral Guard was enhanced, to detect malicious LNK files (windows shortcut / direct link to a file). It analyzes the target of a LNK file to determine if the LNK file itself is malicious.
LNK files are mostly though not exclusively utilized maliciously to start LOLBins (Living Off The Land Binaries) like Windows OS executables. Some common targets for malicious LNK files include CMD, powershell, and wscript.
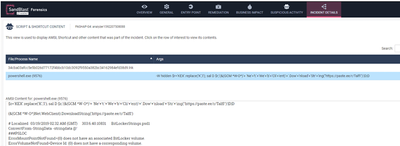
In addition, the Forensics Analysis now can determine whether the attack originated from an LNK file and the Forensics Report shows the targets of all LNK files in an incident.
Content view in the Forensics report
The Forensics Report now has been enhanced to show all AMSI content and LNK targets in a new single view called the Content View. This view is accessible under the Incident Details Menu option
Full Disk Encryption – pre-boot screen
The Full Disk Encryption pre–boot has a modernized look and feel along with updates to the color-theme and background images.
Stay safe,
Guy A.
3 Comments
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter