- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Firewall Uptime, Reimagined
How AIOps Simplifies Operations and Prevents Outages
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Product Announcements
- :
- Endpoint Security / SandBlast Agent Newsletter - V...
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Endpoint Security / SandBlast Agent Newsletter - Version E82.40
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
2020-02-19
01:18 AM
We are happy to announce the release of Endpoint Security Client E82.40.
E82.40 introduce new functionalities and quality improvements.
The complete list of improvements can be found in the version release’s Secure Knowledge sk164956
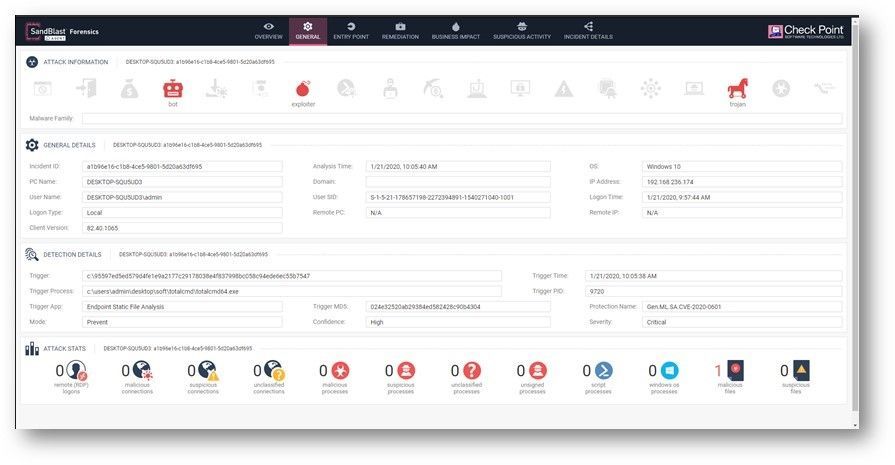
Windows CryptoAPI Spoofing Vulnerability – CVE-2020-0601
A spoofing vulnerability exists in the way Windows CryptoAPI (Crypt32.dll) validates Elliptic Curve Cryptography (ECC) certificates.
An attacker could exploit the vulnerability by using a spoofed code-signing certificate to sign a malicious executable, making it appear the file was from a trusted, legitimate source.
The user would have no way of knowing the file was malicious, because the digital signature would appear to be from a trusted provider.
SandBlast Agent can detect and prevent this vulnerability for un-patched systems.
Behavioral Guard enchantments
- Meterpreter Reverse Shell detections are now active by default.
- Reverse shell attacks obtain control over a compromised system, an attacker usually aims to gain interactive shell access for arbitrary command execution which is very complex to detect.
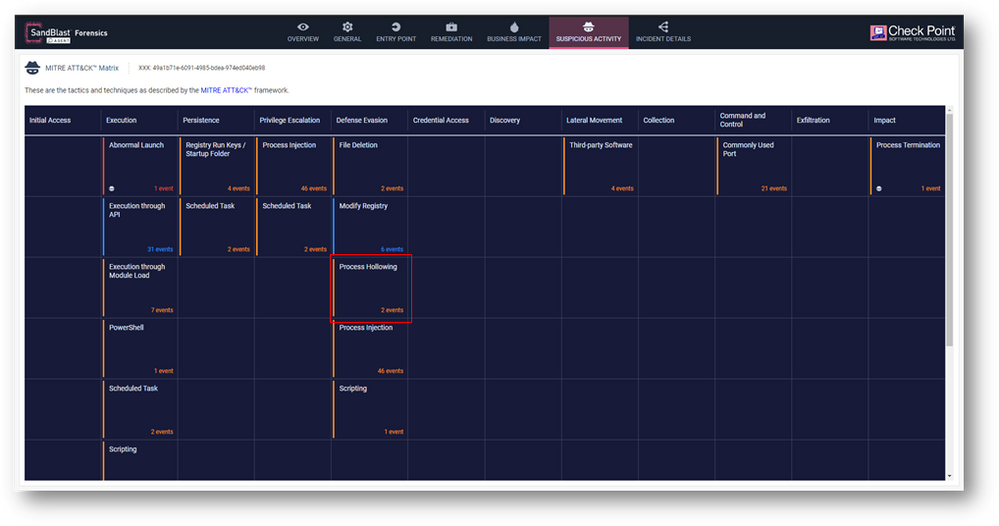
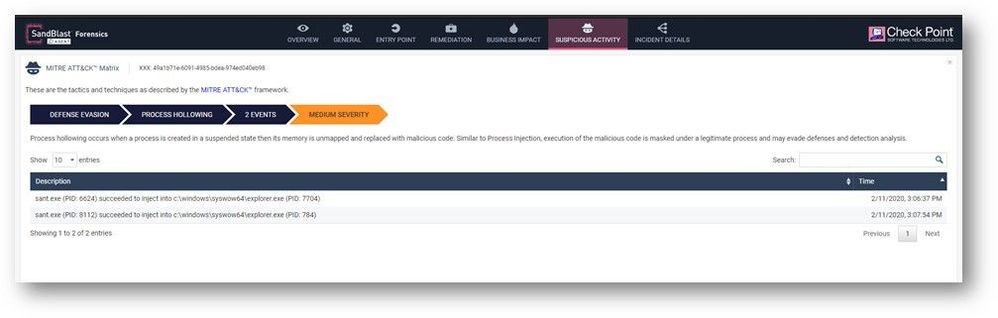
- New injection detections including Process Hollowing are now active by default.
- Process Hollowing is a code injection technique in which the executable section of a legitimate process in the memory is replaced with malicious code.
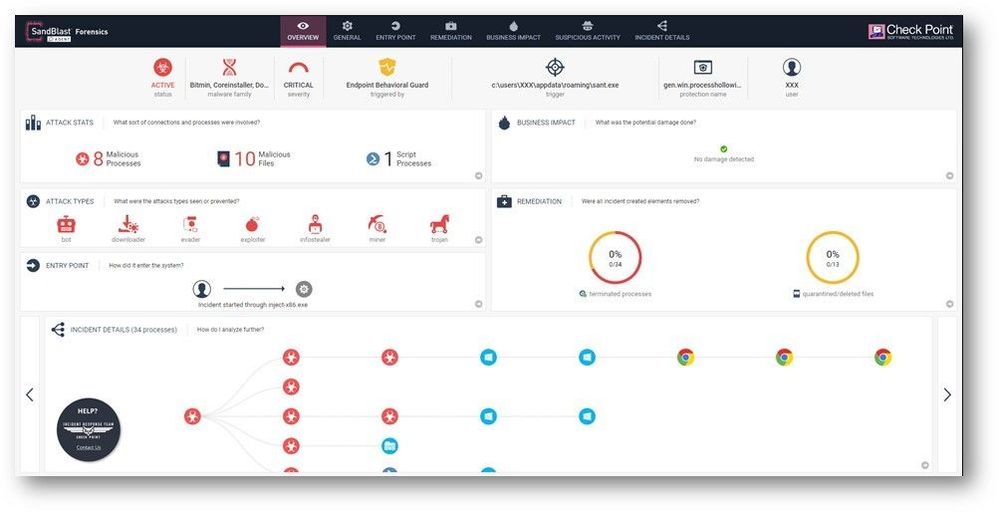
- Forensics can now identify starting points of attacks originating from lateral movement and Windows Management Instrumentation (WMI). Indirect execution on a single machine through WMI is now detected and followed in the Forensics Analysis.
- Behavioral Guard now detects Windows-reported CVEs to generate a log and Forensic Analysis.
Below is a forensic report for Process Hollowing
Threat Prevention enhancements and fixes
- Improves performance slightly by removing unnecessary logs from Behavioral Guard.
- Fixes an issue in the Forensics Log Card to report a trigger rather than the process of a trigger.
- Fixes an issue with a Forensic crash in a Virtual Disk Infrastructure (VDI) environment.
- Anti-Bot detection status now updates to the server User Interface continuously for additions and removals from the client.
- Fixes an issue that can cause the Anti-Exploit service to crash in x86 systems, after an upgrade.
- Fixes a rare issue where the machine hangs during an upgrade (related to a driver that Anti-Exploit uses).
- Fixes an issue where Anti-Exploit may not work immediately after an upgrade.
- Resolves the issue where an Anti-Malware infection event is not showing in SmartEndpoint Reporting, if special characters are in the path.
- Resolves an issue where Anti-Malware reporting does not update in SmartEndpoint, after the infections list changes in the Anti-Malware blade.
- Fixes an Anti-Malware system scan memory issue, when scanning files with alternate data streams.
Data and Access Protection enhancements and fixes
- Resolves an incorrect report about the Full Disk Encryption blade not running during a Windows shutdown, when the Deployment Agent (CPDA) does not receive a shutdown notification.
- Sets BCDBOOT as the default on fresh installs.
- Fixes Unified Extensible Firmware Interface (UEFI) to use the customized image rebrandings of UEFI preboots.
- No longer forces a reboot when the pre-boot bypass is off, by policy.
- Resolves a possible issue where the Firewall blade has the Initializing status after an upgrade due to some missing dll files.
- Resolves a possible issue where registry parsing, while self-protection is active, causes a BSOD.
- Fixes the vsdatant.sys driver synchronization issue that causes a BSOD on driver unload.
- Resolves the issue where Long Term Evolution (LTE) and Universal Mobile Telecommunication System (UMTS) devices are not recognized as wireless by the "Disconnect wireless connections when connected to the LAN" feature.
- Fixes and removes the requirement to install Visual Studio 2017 runtimes when running the Media Encryption offline utility "Access to Business Data". Note: The Mac offline utility now supports macOS Catalina (10.15).
- Fixes an issue where the location inside the organization is not recognized properly.
- Adds the detection of McAfee Security Endpoint v10.6 into Secure Configuration Verification (SCV).
- Fixes an issue where the user is not able to use several question marks in the password.
Installer and general enhancements and fixes
- Resolves a possible issue where the client upgrade fails, when the Anti-Malware blade cannot reach a database file, after an ungraceful process termination.
- Resolves a sudden reboot, after a client upgrade finishes, before a custom countdown timer ends.
- Resolves an issue where Installer terminates on machines with specific locales, if the user has a name with specific localized UTF-8 characters.
- Resolves a possible issue where the installation fails, by waiting for a process from a previous installation to stop.
- Increases the timeout value for Windows Installer (MSI) to wait for Full Disk Encryption to finish a deployment in offline mode.
- Fixes the Full Disk Encryption uninstall, after a Windows 10 upgrade.
- Fixes an issue with the Deployment Agent (CPDA). Now, it tries to resend the UpdateRegister message, when the machine has network configuration changes, if the message did not go through, during startup.
- Resolves an issue where the "Disconnected Policy" is not defined, and appears in the display, when the client is connected.
- Fixes the issue of duplicate user objects for the same user in Other Users / Computers.
Best
Ami.B
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter