What is SandBlast Mobile?
Check Point SandBlast Mobile 3.0 is the most complete mobile security solution designed to prevent emerging fifth generation cyber attacks and to allow workers to safely conduct business. Its technology protects against threats to the OS, apps, and network, scoring the industry’s highest threat catch rate without impacting performance or user experience.
Only SandBlast Mobile 3.0 delivers threat prevention technology that:
- Performs advanced app analysis to detect known and unknown threats
- Prevents man-in-the-middle attacks on both cellular and WiFi networks
- Blocks phishing attacks on all apps: email, messaging, social media
- Prevents infected devices from sending sensitive data to botnets
- Blocks infected devices from accessing corporate applications and data
- Mitigates threats without relying on user action or mobile management platforms
SandBlast Mobile 3.0 uses a variety of patent-pending algorithms and detection techniques to identify mobile device risks, and triggers appropriate defense responses that protect business and personal data.
The SandBlast Mobile solution (“the Solution”) includes the following components:
- SandBlast Mobile Behavioral Risk Engine (“the Engine”)
- SandBlast Mobile Gateway (“the Gateway”)
- SandBlast Mobile Management Dashboard (“the Dashboard”)
- SandBlast Mobile Protect app (“the App”) for iOS and Android
When used in conjunction with a Unified Endpoint Management (UEM) solution, the SandBlast Mobile Solution provides integral risk assessment of the device to which the UEM can use to quarantine or enforce a set of policies that are in effect until the device is no longer at risk. Such policy enforcement could be to disable certain capabilities of a device, such as blocking access to corporate assets, such as email, internal websites, etc., thus, providing protection of the corporation’s network and data from mobile based threats.
Solution Overview
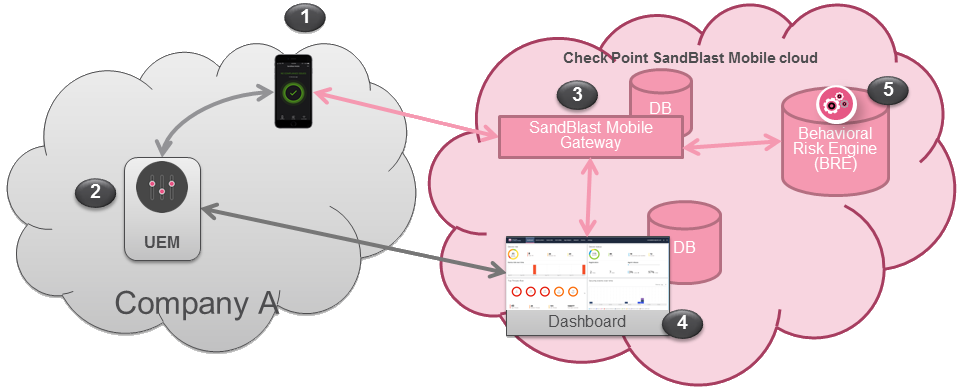
| Component | Description |
1 | SandBlast Mobile Protect app | - The SandBlast Mobile Protect app is a lightweight app for iOS® and Android™ that gathers data and helps analyze threats to devices in an Enterprise environment. It monitors operating systems and information about apps and network connections and provides data to the Solution which it uses to identify suspicious or malicious behavior.
- To protect user privacy, the App examines critical risk indicators found in the anonymized data it collects.
- The App performs some analysis on the device while resource-intensive analysis is performed in the cloud. This approach minimizes impact on device performance and battery life without changing the end-user experience.
|
2 | UEM | - Unified Endpoint Management (generalized term replacing MDM/EMM)
- Device Management and Policy Enforcement System.
|
3 | SandBlast Mobile Gateway | - The cloud-based SandBlast Mobile Gateway is a multi-tenant architecture to which mobile devices are registered.
- The Gateway handles all Solution communications with enrolled mobile devices and with the customer’s (“organization’s”) Dashboard instance.
|
4 | Management Dashboard | - The cloud-based web-GUI SandBlast Mobile Management Dashboard enables administration, provisioning, and monitoring of devices and policies and is configured as a per-customer instance.
- The Dashboard can be integrated with an existing Unified Endpoint Management (UEM) solution for automated policy enforcement on devices at risk.
- When using this integration, the UEM serves as a repository with which the Dashboard syncs enrolled devices and identities.
|
5 | Behavioral Risk Engine | - The cloud-based SandBlast Mobile Behavioral Risk Engine uses data it receives from the App about network, configuration, and operating system integrity data, and information about installed apps to perform in-depth mobile threat analysis.
- The Engine uses this data to detect and analyze suspicious activity, and produces a risk score based on the threat type and severity.
- The risk score determines if and what automatic mitigation action is needed to keep a device and its data protected.
- No Personal Information is processed by or stored in the Engine.
|
Related Content: View our lightboard session about the SandBlast Mobile Architecture.



