- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: smart event alerting of IPS prevent
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
smart event alerting of IPS prevent
I've been asked to set up an alert on traffic (even a single incident) that is prevented from an internal IP -> DMZ. This seems easy, but is not possible with Smart Event. It's rare that this traffic would be correlated, the PREVENT just shows up as a single log - type NOT correlated. THUS, the alert doesn't fire. Does anyone know if there is a way?
Creating Event Definitions (User Defined Events) - page 56 of the R77 smart event guide (I'm on R80.30, but this has the best documentation on user defined events. To create a user-defined event you must have knowledge of the method by which SmartEvent identifies events. This section starts with a high level overview of how logs are analyzed to conclude if an event occurs or occurred.
When you create a user defined event, there is a COUNT LOGS tab and inside a radio button 'single log', this NEEDs to be updated to say single correlated log for accuracy.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
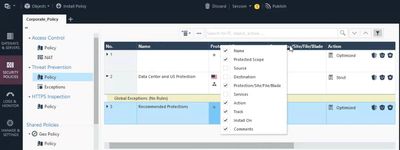
Right click on the rule headings and you can add source and destination columns.
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You're correct in that SmartEvent only works on correlated logs.
However, what you're asking can be done outside of SmartEvent.
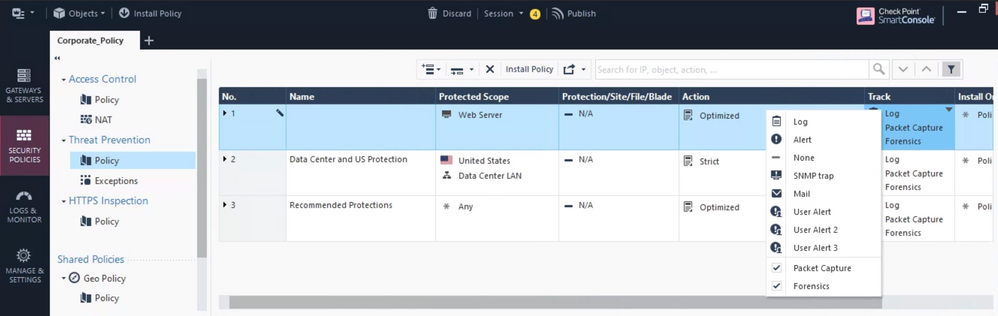
You can create an explicit rule for this server in your Threat Prevention policy and set the Track option to Mail and/or one of the User Alert options.
This will generate an email or run whatever script you specify on each log entry that is generated.
To configure Mail and/or User Alert options, refer to sk25941.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is a better solution for your case. Create a custom rule for Threat Prevention policy layer, put there IPs and zones you need as source and destination. Set tracking for custom alert, et voila…
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for these responses!
However, the 'protected scope' doesn't seem to be specific enough.
I have a very specific case - I want alert on if it's from this IP address, x.x.x.1 AND to this destination network y.y.y.0/24.
The protected scope is more of an 'either OR' not an 'AND'. IOW protected scope is if it's in/out to x.x.x.1 OR in/out to y.y.y.0/24.
Maybe, the best we can do is a twice daily report on TP associated with x.x.x.1.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Right click on the rule headings and you can add source and destination columns.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks!
This will work, it looks like the limitation is you are limited to 3 custom alerts. Alert no. 1, 2, & 3.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One called script can potentially do multiple things based on the input it receives.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there a list somewhere that shows the stream sent when you call an alert? What input does it receive? I can write a script to use the data the script receives when an alert is generated, but what does that input/stream list look like?
I know with an email alert, a nice attachment that looks like the full record of the Prevent or Drop is sent.
However, with a script what is sent to the alert/script as input. Yes, once you have that list, I can see how you can use it in a script to parse it and do different things.
Origin: $Origin
Blade: $Blade
Action: $Action
Attack Name: $Attack_Name
Attack Information: $Attack_Info
Source: $Source
Destination: $Destination
Severity: $Severity
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you were to look at the log entry as it's shown with either fw log or CPLogFilePrint, it would look something like that.
What is sent depends on what information is in the log.
What is sent depends on what information is in the log.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
TAC found more here: https://sc1.checkpoint.com/documents/R80.10/WebAdminGuides/EN/CP_R80.10_LoggingAndMonitoring_AdminGu...
This show how to pull the EVENT into the script.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
What scripting language/s can be used? LLast time I tried python on Gaia & tried to wanted to add new modules/libraries, CP said I would invalidate the support if I added new libraries. I think we talked about running a shell script that would call a python script on another server, but that would also involve passing the stream down to a different server.
Basically If attack_info = Zmap scan -> /dev/null, I want zmap secruity scans to be prevented but I don't want a case to fire off because of it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A bash script is where I would start as that doesn't require installing any other interpreters.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 16 | |
| 15 | |
| 7 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter