- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Improve Your Security Posture with
Threat Prevention and Policy Insights
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Untrusted SSL on Cluster's outside interface
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Untrusted SSL on Cluster's outside interface
Hello,
I have managed to implement internal CA signed SSL cert for our Cluster (with multiportal enabled).
All platform portals are accessible by internal interfaces and SSL is trusted and okay.
Accessibility of platform portal is as in following picture:

I read that IPSec do not use SSL cert. If I remove checkbox for "Including VPN encrupted interfaces" will our S2S IPSec VPN and RAVPN be interrupted?
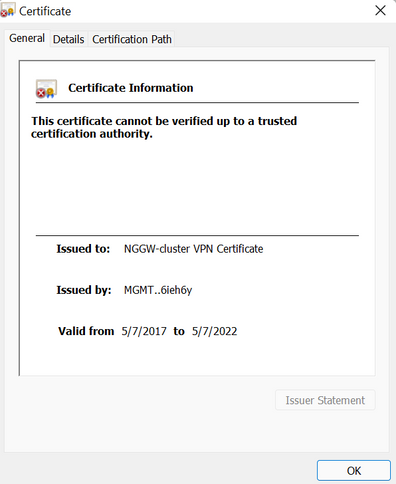
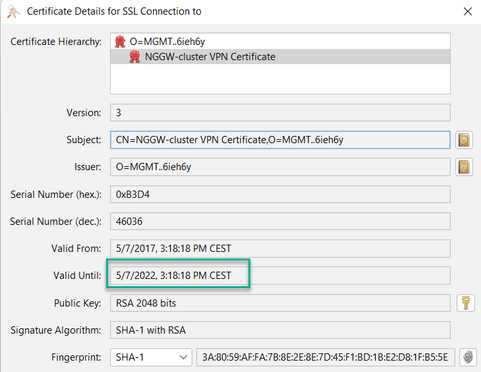
Our Check Point cluster public IP is not trusted. How to make cluster public IP not self signed/default certificate?
When we scan our public cluster IP by ssl checker we get not trusted warning in browser and following default cert is used:
How to change this cert too? Will it affect our VPNs?
Thanks.
17 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The platform portal setting you picture should have no impact on IPsec VPN or SSL VPN.
As for the untrusted certificate you see, if you're using Mobile Access Blade, you can replace it using something like: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello PhoneBoy,
Thanks.
Customer is using CPSB-EP-ACCESS-P-LICENSE for RAVPN not mobile access, but this untrusted cert is presented on outside interfaces in cluster (GW1, GW2 and VIP).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If MAB isn't active, it's the legacy SNX portal.
If you're not using SNX at all, might as well disable it as shown here: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks PhoneBoy.
So just once more, we can exclude IPSec VPN (S2S and RAVPN) that it does not use this self signed SSL on outside interface?
Having that in mind, only two features that can use self signed cert on outside interfaces are Mobile access blade or SNX legacy?
Is there a way to check it, to be sure what uses it (cli..)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you explain what the issue is with self signed certificates ? Usually, all portals use internal CA. You can replace the cert by a 3rd party 1 for MAB and SSL inspection, but there is no difference from a users viewpoint: If i want to access services, i would have to accept the self-signed certificate once. If i use a 3rd party certificate it also has to be accepted once. Looking at how certs are stolen or missused i prefer my own internal CA !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Albrecht,
Customer wants to avoid SSL check tools to not show self-signed cert warnings. I agree with You that encryption is guaranteed and they know that system is theirs. But again they want that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry, but this demand is absolute nonsense in my eyes as it adds nothing to security at all - Customer wants to avoid that SSL check tools he uses himself show him that his FW has a self-signed cert ?
I would rather suggest to care for more important things like DDoS Protection, allowed Ciphers and TLS versions instead...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I totally agree with You.
It is important to educate customers, but again if they want something so much what will make them happy (if it does not produce any consequence to system and security), it's okay.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The default web UI portal cert is good for 10 years and as far as vpn cert, that was changed recently to 1, rather than 5 years validity.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This cert is only valid until 7th May:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats because it was created in 2017...if it was created recently, only good for 1 year.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It sounds like if they dont want that, in that case, you may need 3rd party CA cert.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is best just to disable this cert (mab or snx).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IPSec VPN (either S2S or C2S) doesn't use this cert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does this self signed cert by MGMT CA, auto renew?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello PhoneBoy,
This cluster does not use mobile access blade (not active), nor it supports SSL Network Extender nor it Support Clientless VPN.
How to check what CP feature gives SSL client VPN cert on outside cluster interface?
Do I need to check this possible workaround:
Edit the 'index.html' file specifically for SNX. If SNX client connects to a cluster, then perform these changes on all cluster members (reboot / policy installation are not required).
[Expert@HostName]# cd $FWDIR/conf/extender [Expert@HostName]# ls -la index* [Expert@HostName]# cp index.html index.notworking [Expert@HostName]# rm -i index.html [Expert@HostName]# ls -la index*
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It may be active even if you've not explicitly enabled SNX, thus those steps might be appropriate.
However, it doesn't necessarily get rid of the initial TLS connection.
For that...you may need a TAC case, as I'm not sure how to change the certificate for (or better yet disable) the legacy SNX portal.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 16 | |
| 12 | |
| 9 | |
| 7 | |
| 6 | |
| 6 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Thu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter