- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Firewall Uptime, Reimagined
How AIOps Simplifies Operations and Prevents Outages
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: 🚀 This Month’s Spotlight: 4 Features You Shou...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
🚀 This Month’s Spotlight: 4 Features You Should Start Using Today - August 2025
Welcome Back to Our Quantum Management Spotlight
Every month, we shine a light on powerful features in Quantum Security Management’s SmartConsole that make your job easier, your environment cleaner, and your decisions sharper. These aren’t add-ons - they’re already included in your system, just waiting to be used.
This month, we’re spotlighting four features that every security admin should start using today.
🚀 This Month’s Spotlight: 4 Features You Should Start Using Today
-
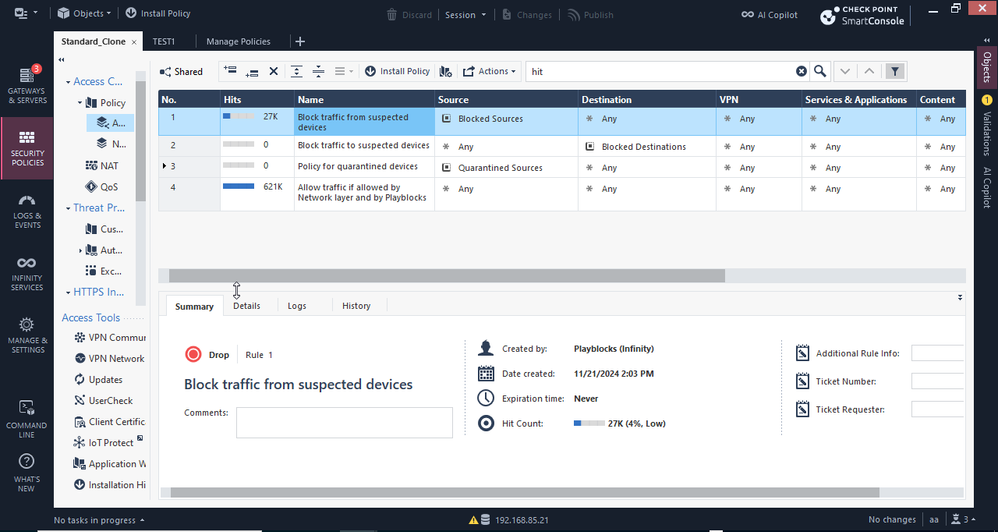
Hit Count in the Rulebase - know what rules truly matter
What it is:
Hit Count in the rulebase shows how frequently each rule in your Access Control or NAT policy matches traffic. You can view counts as numerical values, percentages of total traffic, or tiered levels (Very High, High, Medium, Low, Zero).
Use cases:
- Spot unused rules: Quickly identify Zero-hit rules and clean them out.
- Optimize performance: Shift high-traffic rules upward to improve efficiency.
- Validate policies: Confirm that critical rules are acting as intended.
Why you’ll love it: 💛
- Instant clarity – See real traffic impact without enabling logging.
- Already on – Hit Count is enabled by default so you can start right now.
- Cleaner policies – Keep your rulebase lean and relevant.
🆕 New in R82.10 and from R82 Jumbo Take 36
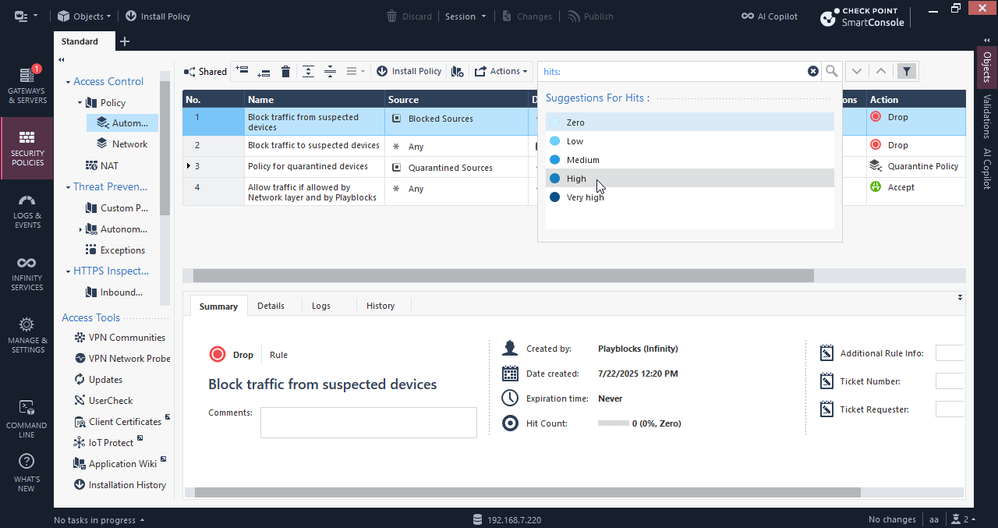
One of the most anticipated enhancements: you can now search rulebases by hit count values (both Access and NAT policies) directly in SmartConsole and the Management API.
Example: quickly find all Zero-hit rules for cleanup, or all rules exceeding 10,000 hits.
This capability streamlines audits and large-scale policy tuning.
How to view & filter Hit Count in the rulebase:
- In the rulebase, right-click the header row → Hits to show the column.
- Right-click any rule to choose timeframe (Day, Week, Month, 3 Months) and display format (Value, Percentage, Level).
- Use the new search bar to find rules by hit count value or range.
- Optional: Export CSV (now includes "Hits", "First Hits", "Last Hits").
Documentation & References
- R82: Hit Count in Rulebase — Administration Guide
- R82 Jumbo Take 36: Hit Count Search in SmartConsole & API
Also supported in the latest Web SmartConsole release for both SMC and MDS. Requires the latest Jumbo Hotfix update.
Hits column in policy:
Search by hits:
----------
-
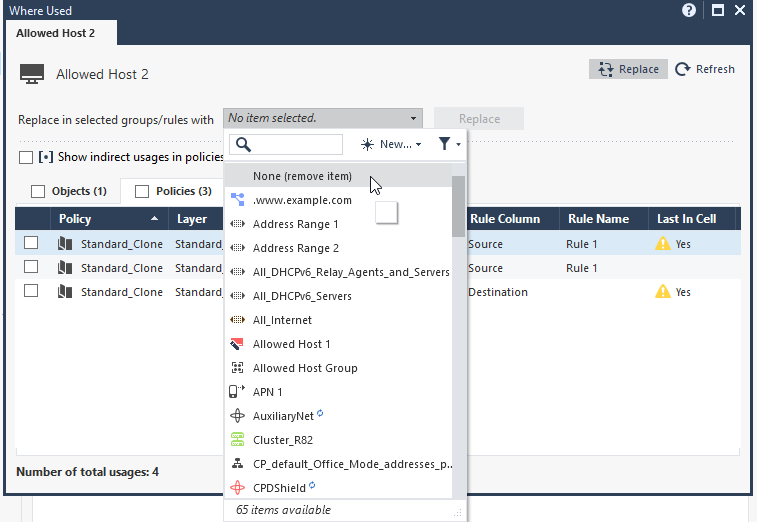
Where Used + Replace (Even with “None!”)
What it is:
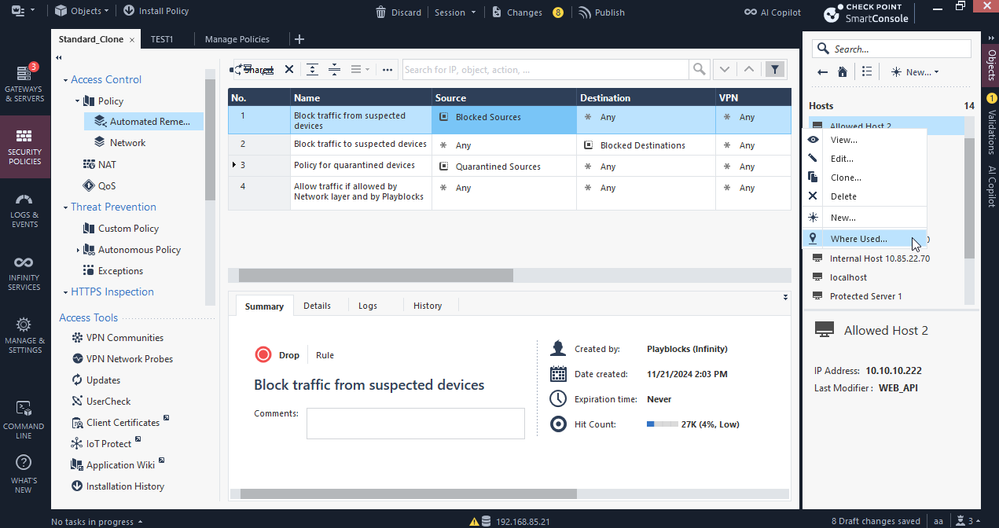
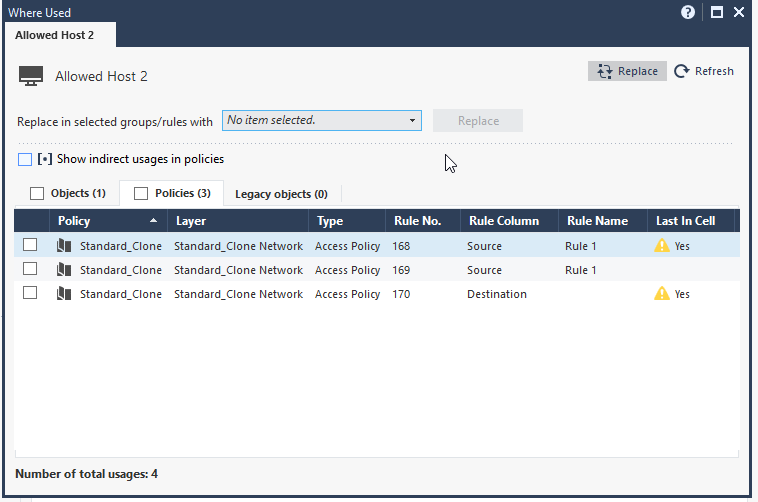
Many admins are familiar with the Where Used feature - it instantly shows every location where a specific object is used, whether in Access Control policies, NAT rules, groups, or elsewhere. What fewer people realize is that you can go a step further:
- Replace the object with another one - everywhere it’s used - in one action.
- Pro tip: You can even replace it with “None”, instantly removing it from all rules and objects in one sweep.
Use Cases:
- Bulk cleanup – Retire obsolete objects everywhere without manually editing each rule.
- Object replacement - Swap an old server object for a new one across your entire environment.
- One-click cleanup using Replace with None to remove unused or temporary objects everywhere they appear.
Why You'll Love It: 💛
- Massive time saver - turn what used to be hours of manual cleanup into seconds.
- Error-proof - ensures no forgotten references are left behind.
- Full coverage - works in Access Control, NAT, and group definitions.
How to Use It:
- Right-click an object in the Object Explorer or directly in the rulebase.
- Select Where Used to see all locations.
- Review the full list of all locations the object is used.
- Click Replace:
- select another object or
- choose None to remove the object from all rules in one action.
- Apply the change and Publish.
Right click on object:
Where Used menu:
----------
-
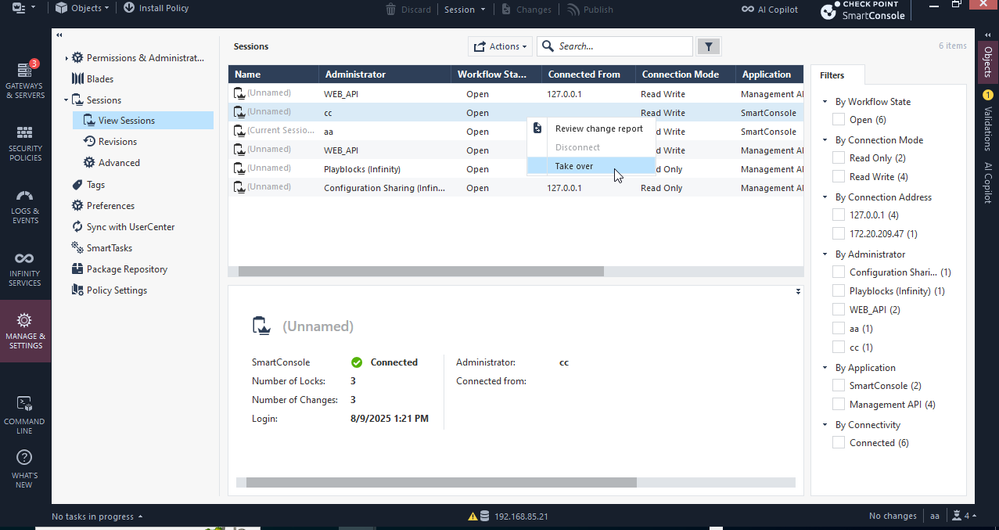
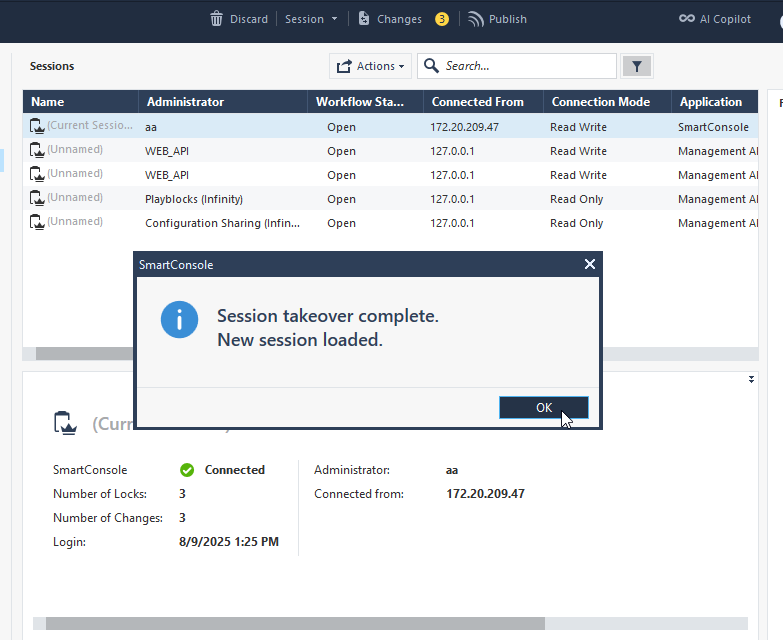
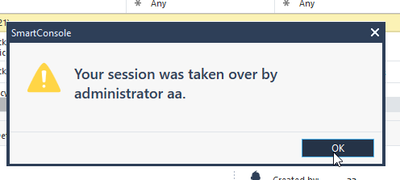
Session Take-Over - regain control instantly
What it is
The Session Take-Over feature in Check Point SmartConsole allows administrators to assume control of another user's session.
This is particularly useful when sessions are left open, potentially blocking critical changes or when an administrator is unavailable.
Use Cases:
- Resolve stale sessions: Quickly take over sessions that are no longer active or have been abandoned.
- Emergency access: Gain immediate access to perform urgent configurations or troubleshooting.
- Collaborative workflows: Facilitate teamwork by allowing multiple administrators to work on the same session.
Why You'll Love It: 💛
- Enhanced productivity: No need to wait for another administrator to finish their session.
- Improved security: Prevent unauthorized changes by ensuring only active sessions are in use.
- Seamless collaboration: Work together efficiently without session conflicts.
How to Use It:
- In SmartConsole, navigate to Manage & Settings > Sessions.
- Locate the session you wish to take over.
- Right-click on the session and select Take Over.
- Confirm the action when prompted.
Note: The ability to take over sessions requires appropriate permissions configured in your user profile.
Take over menu:
Operation completed:
View on the other session side:
----------
-
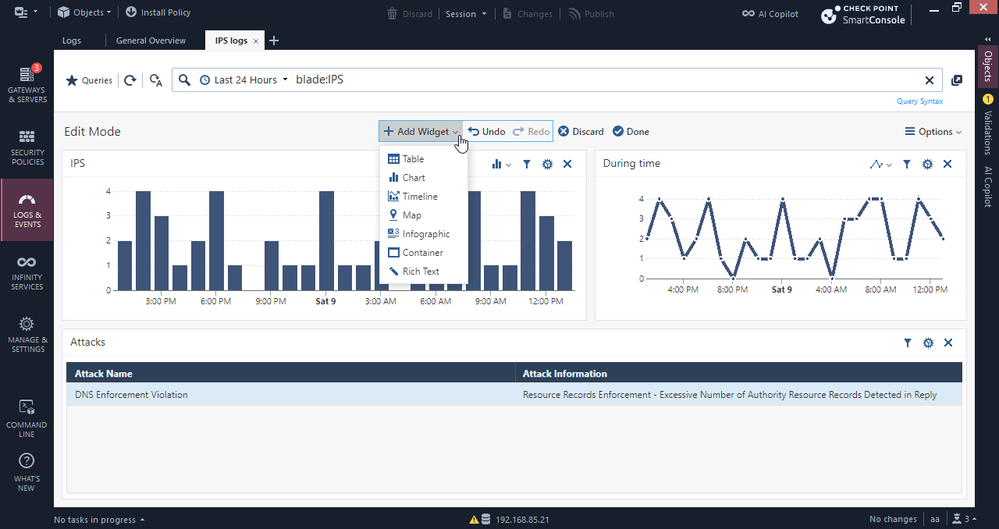
Custom Views in SmartView - tailor your monitoring experience
What it is:
Custom Views in SmartView allow administrators to create personalized dashboards that display specific data relevant to their monitoring needs. These views can include real-time traffic statistics, system counters, VPN tunnel statuses, and more.
Use Cases:
- Focused monitoring: Create views that concentrate on specific gateways, services, or user groups.
- Historical analysis: Set up views to analyze traffic patterns over defined periods.
- Performance tracking: Monitor system counters and VPN tunnel statuses to ensure optimal performance.
Why You'll Love It: 💛
- Personalized dashboards: Design views that align with your specific monitoring requirements.
- Enhanced visibility: Gain insights into areas that matter most to your operations.
- Efficient troubleshooting: Quickly identify issues by focusing on relevant data.
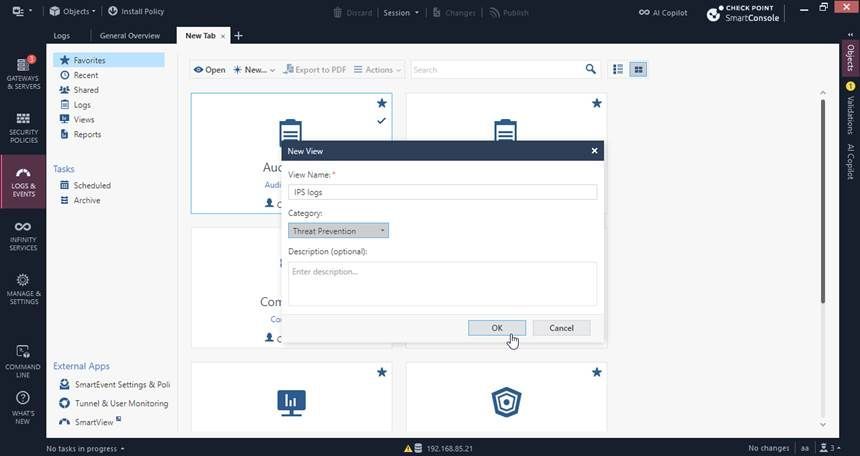
How to Create a Custom View:
- In SmartView, select New View.
- Choose the type of view you wish to create (e.g., Traffic, Counters, Users).
- Define the data sources and filters for your view.
- Customize the layout and appearance to suit your preferences.
- Save the view and access it anytime.
New View:
Example to new view:
✨ Why these features deserve your attention
Each of these four tools is already part of your Quantum Security Management platform:
- No extra licensing required
- Easy to activate and use
- Immediate, tangible benefits
Whether it’s cleaning up your policy, responding faster in emergencies, or improving visibility, these tools help you work smarter.
Ready to Elevate Your SmartConsole Experience?
Start using these features today.
Have feedback or a feature you’d like to see next month? Drop us a line at QuantumMgmt‑Feedback@checkpoint.com .
Missed our first spotlight? Catch up here:.
This Month's Spotlight: 3 Features You Should Start Using Today
Labels
- Labels:
-
SmartConsole
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Let me add here what you should STOP using.
1. Install-on field on rules.
Create a separate policy for each security gateway/cluster.
2. Manual NAT-rules
Use manual NAT only for complex NAT where you will have to translate source and destination or port.
In all other cases use automatic NAT. It keeps your environment a lot less complex.
3. Rules that have tens of objects
Consolidate rules when possible, use simple object groups (avoid nested groups though) and allow access based on identities instead of IP-addresses.
4. Large policies with no structure
Use unified policies with inline layers, use section headers and add a comment to each rule.
5. Ordered layers
Use unified policies rather than having a separate policy for every access control blade
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great tips!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2. Manual NAT-rules
Use manual NAT only for complex NAT where you will have to translate source and destination or port.
In all other cases use automatic NAT. It keeps your environment a lot less complex.
I really don't agree with this.
A lot of admins totally abuse automatic NAT, enabling it on each and every internal object (including host objects!), and soon the rules list is a complete unreadable mess, filled with literally hundreds of rules.
Using automatic NAT on large networks objets is okayish, but if you happen to use a lot of subnets on your internal networks, this quickly gets messy as well.
IMHO, it's much cleaner to use clearly named groups in NAT rules, and keep the rule count as low as possible.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I get your point. Automatic NAT can definitely get messy if it’s just switched on for every object without thinking, and I’ve seen those environments too. But I’ve also walked into sites with hundreds or even thousands of manual NAT rules, and those are just as painful to manage long-term.
For me, it comes down to using the right tool for the right job:
-
Automatic NAT works really well for simple source or destination translations. Keeping the NAT tied to the object makes it easier for most admins to follow and reduces overhead.
-
Manual NAT is the way to go when you need something more complex—source and destination together, port translations, or special cases. The flexibility is there, but you usually end up dealing with proxy ARP and extra steps.
So yes, automatic NAT can be abused, but when used properly it keeps things much cleaner. Manual NAT definitely has its place, but for most straightforward cases, automatic NAT usually makes life a lot easier.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there an API option to the replace feature? I did not see that option in the API guide.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
API for "replace where-used" will arrive in one of the upcoming JHFs.
We added it to enable this functionality in an upcoming Web SmartConsole as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Immediately after reading the tips I was searching through the API documentation for the replace feature and wanted to ask the same question. 😂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for sharing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can also find new views/reports in SmartEvent toolbox in the following link:
https://community.checkpoint.com/t5/SmartEvent/bd-p/SmartEvent
Kind regards, Amir Senn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You wrote: Optimize performance: Shift high-traffic rules upward to improve efficiency.
Afaik this is not important anymore with the new matchong algorithms ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am running R82 JHF T39 yet policy search with keyword hits is not available. What HF is this going to be released in?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can't try, but above screenshot shows keyword hit was used, instead hits.
Or maybe the Smart Console client needs to be also the newest version ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
the screenshot shows hits not hit - the first screenshot is not showing the keyword. Its the second one.
I am running latest SmartConsole available at Check Point
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 26 | |
| 12 | |
| 8 | |
| 7 | |
| 6 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 2 |
Upcoming Events
Thu 30 Oct 2025 @ 03:00 PM (CET)
Cloud Security Under Siege: Critical Insights from the 2025 Security Landscape - EMEAThu 30 Oct 2025 @ 11:00 AM (EDT)
Tips and Tricks 2025 #15: Become a Threat Exposure Management Power User!Thu 30 Oct 2025 @ 02:00 PM (EDT)
Cloud Security Under Siege: Critical Insights from the 2025 Security Landscape - AMERThu 30 Oct 2025 @ 03:00 PM (CET)
Cloud Security Under Siege: Critical Insights from the 2025 Security Landscape - EMEAThu 30 Oct 2025 @ 11:00 AM (EDT)
Tips and Tricks 2025 #15: Become a Threat Exposure Management Power User!Thu 30 Oct 2025 @ 02:00 PM (EDT)
Cloud Security Under Siege: Critical Insights from the 2025 Security Landscape - AMERWed 05 Nov 2025 @ 11:00 AM (EST)
TechTalk: Access Control and Threat Prevention Best PracticesAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter