- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- TLS1.3 inspection
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
TLS1.3 inspection
Hi again,
I managed now to enable TLS1.3 on my R81 Security Gateway.
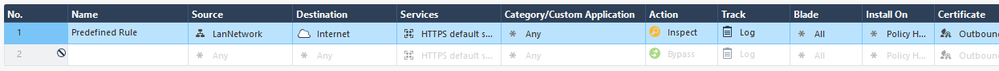
But the HTTPS Inspection doesn't work in case of TLS1.3 traffic:
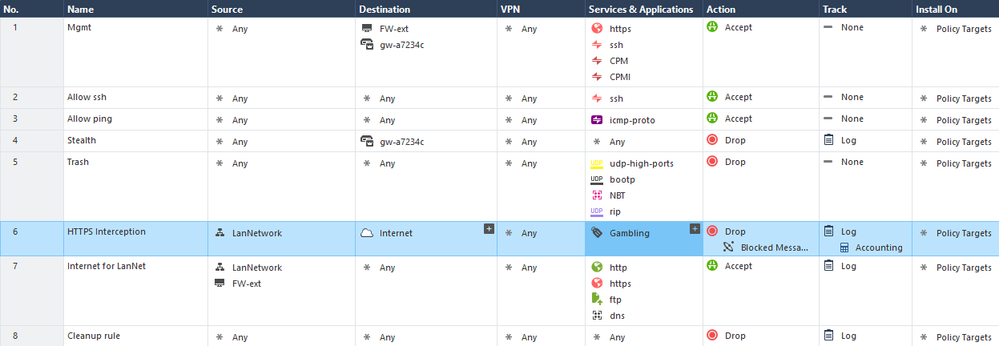
Just to be sure you have all in infos her my simple rulebase:
Is there any special rule I need to add to catch TLS1.3 traffic?
Thanks, Iko
21 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
First of all, disabling your bypass rule can cause performance issues.
Is USFW enabled? https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can you tell me how to verify if usfw is enabled?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
cpprod_util FwIsUsermode
cpprod_util FwIsUsfwMachine
Both commands should return 1.
What precise appliance are you doing this on?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I run a R81 Security Gateway with Mgmt-Gateway on same VM
Product version Check Point Gaia R81
OS build 392
OS kernel version 3.10.0-957.21.3cpx86_64
OS edition 64-bit
[Expert@gw-a7234c:0]# cpprod_util FwIsUsermode
0
[Expert@gw-a7234c:0]# cpprod_util FwIsUsfwMachine
0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What are the precise specifications (RAM, cores) on the VM?
Note that HTTPS Inspection for TLS 1.3 traffic requires three things:
- Being on R81 or above, which you are.
- Enabling TLSIO, which you clearly did here.
- Enabling User Space Firewall, which is only enabled by default for specific appliances.
The two commands indicate USFW is not enabled.
To enable them, issue the following two commands and reboot:
cpprod_util FwIsUsermode 1
cpprod_util FwIsUsfwMachine 1
Once you've done this, HTTPS Inspection of TLS 1.3 should work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
doesn't work for some reason:
[Expert@gw-a7234c:0]# cpprod_util FwIsUsermode 1
Unknown/Unsupported command 1
0 [Expert@gw-a7234c:0]# cpprod_util FwIsUsfwMachine 1
Unknown/Unsupported command 1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Should be:
FwSetUsermode, FwSetUsfwMachine
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks _Val_, this worked:
[Expert@gw-a7234c:0]# cpprod_util FwIsUsermode
1
[Expert@gw-a7234c:0]# cpprod_util FwIsUsfwMachine
1
Thank you both _Val_ and PhoneBoy
Iko
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
unfortunately, I had to remove the "accept as solution" because the TLS1.3 inspection still has some problem.
In the log I can see that the inspection works, but the client browser shows a "Secure Connection failed" message now.
Is there anything else I am missing?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Root certificate installed as trusted probably? 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I analyzed the traces, it looks like the firewall is striping off the supported_versions extension in the outgoing ClientHello now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
my bad, i didnt reboot.
now HTTPS requests workd again on client, but traffic is bypassed from interception again. but only TLS1.3 traffic
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What's the log card say on the bypassed log?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
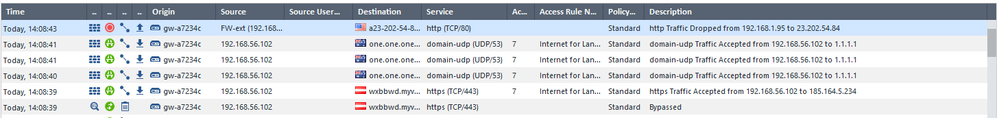
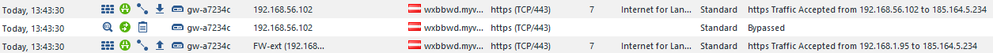
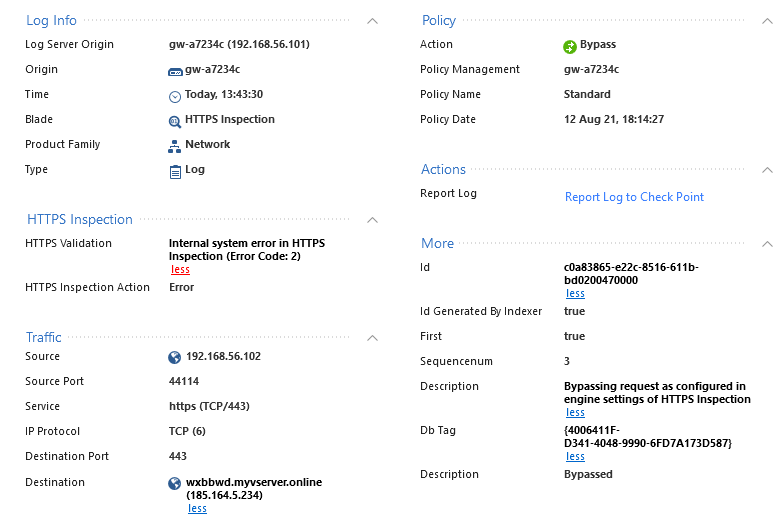
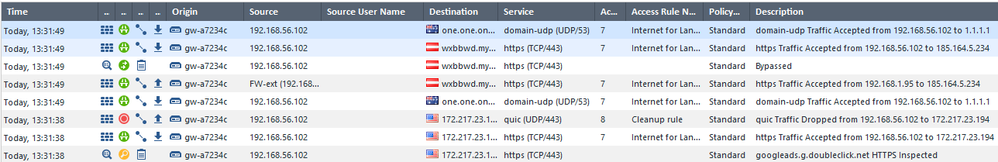
One request on the client always brings up 3 log entrys:
is this the log card?
Just for clarification: The accessed webserver is TLS1.3 only.
First log entry gets accepted. I think this is the first ClientHello sent without supported_versions extension, which makes it an TLS1.2 request. This is not what the webserver expects, so he replies with some version_alert. So the Firewall sends the ClientHello again, this time with supported_versions extension included (TLS1.3) -> This is what log entries 2 & 3 are about.
I just wonder why the bypass entry comes second!? Wouldn't it make more sense if the decision to intercept or not, is made already before the first request is sent. or is the order not really accurate, since this all happens in very short time?
just my thoughts ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The order may not entirely be accurate here, but the Internal System Error would explain why it is bypassing.
You’ll need to use this SK to debug what’s happening: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have tried these commands multiple times and after a reboot, the values are back to 0
cpprod_util FwSetUsermode 1
cpprod_util FwSetUsfwMachine 1
Also, I tried enabling TLSIO by adding fwtls_enable_tlsio=1 to $FWDIR/boot/modules/fwkern.conf; fw ctl get int fwtls_enable_tlsio shows it is 0 after reboot, If I try to set on the fly with fw ctl set int fwtls_enable_tlsio 1, I get the error "Set operation failed: failed to get parameter fwtls_enable_tlsio".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Alex_Lewis ,
Can you share on which version and platform you are trying to convert to USFW?
Thanks,
Ilya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2 gateway HA cluster running R81 Take 36 on Open Platform
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
in general if it's open platform so it should be USFW by default.
can you share which type to you have? how many CPU's it has?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dell PowerEdge R430, 16 cpus, 32GB ram
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Alex_Lewis ,
according to our hcl this type is not supported
https://www.checkpoint.com/support-services/hcl/
Thanks,
Ilya
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 16 | |
| 6 | |
| 5 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter