Hello Everyone,
We have a CheckPoint firewall running R77.30 (we are in the process of upgrading to R80.40) which has 2 VPN star communities configured to 2 external 3rd Party companies. These VPNs work correctly (one is a Cisco ASA and the other a Sonicwall) for traffic accessing the LAN services within each star community. A new requirement has arisen where the 3rd party at site A needs to be able to access a service hosted at site B. The 3rd parties are not be able to have their own direct VPN connection so traffic will traverse the CheckPoint firewall.
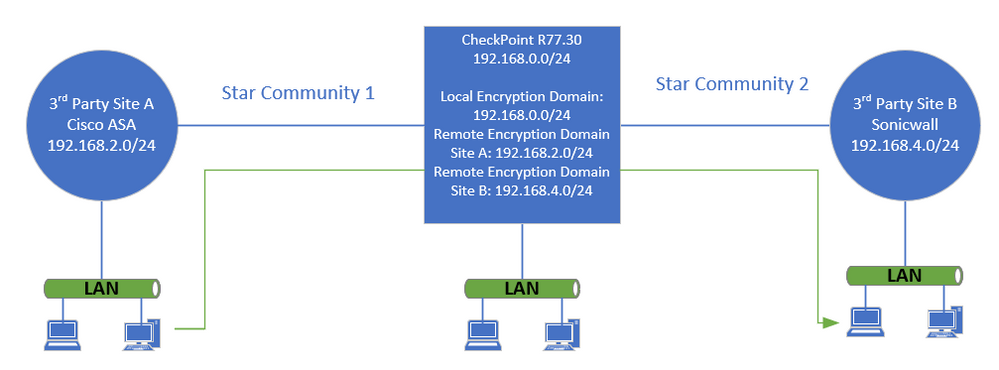
Encryption Domains:
CheckPoint Firewall:
Local: 192.168.0.0/24
Remote Encryption Domain Site A: 192.168.2.0/24
Remote Encryption Domain Site B: 192.168.4.0/24
Site A Firewall:
Local: 192.168.2.0/24
Remote Encryption Domain: 192.168.0.0/24
Site B Firewall:
Local: 192.168.4.0/24
Remote Encryption Domain: 192.168.0.0/24
I have tested creating the below NAT rule: (Disable NAT inside the VPN community is unchecked in both communities)
Source IP: 192.168.2.10 > Destination IP: 192.168.0.10 > Source NAT: 192.168.0.10 > Destination NAT: 192.168.4.10
The packet from site A will decrypt on the CheckPoint, apply the source / dest NAT and hit the firewall rule configured to allow traffic to the site B VPN tunnel. The packet is Accepted but not Encrypted so doesn’t traverse the site B VPN. I think this is due to the pre-NAT destination IP - 192.168.0.10 being defined in the CheckPoint local VPN encryption domain.
Is this option possible or should it be done a different way? I don’t know how I can send traffic across as I would need to add the site B remote encryption network into the CheckPoint local encryption domain.
Any suggestions or thoughts would be appreciated.
Thank you.



