- CheckMates
- :
- Products
- :
- Quantum
- :
- Management
- :
- Re: SecureXL qouta violatation
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SecureXL qouta violatation
Hello Mates,
Today my website experimented a DDOS attack. I use R80.10 firewall.
When search on smartlog, I see that CP had blocked Malicious IPs but I dont know why CP also blocked almost normal user IPs from internet who normal access to my website.
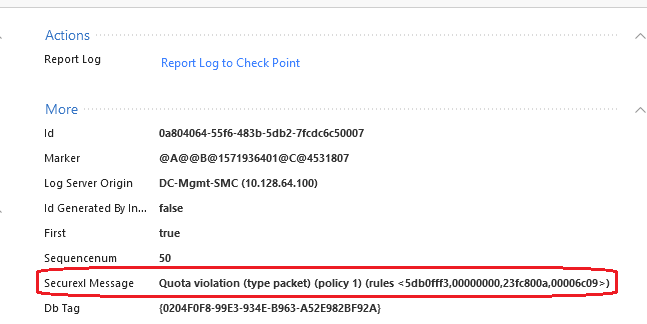
The log is below:
(P/S: I do not use Network quota of IPS blade)
Please help to explain!!!
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank phone boy,
After I issue command : fw samp del "uuid" ; the samp rule STILL has effect. Then I search on below link; they said we need more command to actual delete samp rule:
fw samp add -t 2 quota flush true (I did and now actually deleted samp rule)
Link : https://sc1.checkpoint.com/documents/R77/CP_R77_SecurityGatewayTech_WebAdmin/96330.htm
P/S : I am still looking for command to limit number of connections for EACH IP client to connect to my website
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Also in my case, CP block almost all normal IP, which access my website, not only some known malicious IPs as in sk103154.
I dont use rate limit connection :
[Expert@DC-Internet-Fw-01:0]# fw samp get
Get operation succeeded
no corresponding SAM policy requests
[Expert@DC-Internet-Fw-01:0]#
After I manual blocked malicious IPs from DDOS by adding rule in rulebase, the internet users can access my website normally
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
The output here
[Expert@DC-Internet-Fw-01:0]# fw samp get
Get operation succeeded
no corresponding SAM policy requests
[Expert@DC-Internet-Fw-01:0]#
Before the dropping happen, I issue command:
fw samp add -a d -l r quota service 6/443 source any destination cidr:<MY_WEBSITE_IP> concurrent-conns 50 flush true
but I deleted it right after with "fw samp del "uuid"
So, i dont know if this command has still have effect?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It would also apply for ALL traffic to your webserver, even if it was from a trusted IP.
Are those logs still generated from the time AFTER you deleted the samp rule?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank phone boy,
After I issue command : fw samp del "uuid" ; the samp rule STILL has effect. Then I search on below link; they said we need more command to actual delete samp rule:
fw samp add -t 2 quota flush true (I did and now actually deleted samp rule)
Link : https://sc1.checkpoint.com/documents/R77/CP_R77_SecurityGatewayTech_WebAdmin/96330.htm
P/S : I am still looking for command to limit number of connections for EACH IP client to connect to my website
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm pretty sure you cannot limit the number of connections to a destination IP address individually by unique source address in a single rule with fw samp in R80.10 and earlier. Doesn't look possible in R80.20+ either. The best you could do is specify multiple rules with different ranges or networks of source IPs and have a concurrent connection limit for each of those individual rules matching the same destination. The SAM rule matching here is relatively simple, and doesn't really track stateful elements like the number of concurrent connections to a destination by individual source address.
Exclusively at CPX 2025 Las Vegas Tuesday Feb 25th @ 1:00pm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This should track per source IP versus per rule.