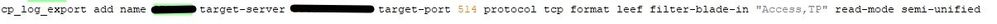- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Announcing Quantum R82.10!
Learn MoreOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Rule set with track none, but still logging #2
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Rule set with track none, but still logging #2
Hi,
There's an existing topic on this from Feb 2021 but no solution.
Rule set with track none, but still logging
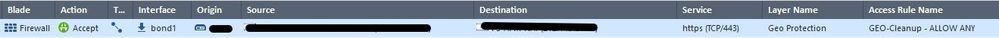
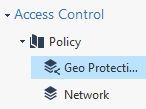
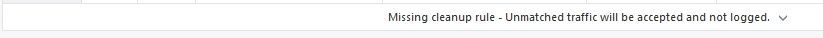
I've recently added a policy layer to manage geo protection using updatable objects, I wanted to remove logging for the cleanup rule which is allow any since all non-matched traffic should be forwarded to the 2nd layer which is "Network" so I have duplicate logging showing up.
I am using R81.10 , even though Track is "None" , the logs are showing, I tried the suggestions in the previous post, but to no avail.
Labels
- Labels:
-
Logging
-
SmartConsole
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
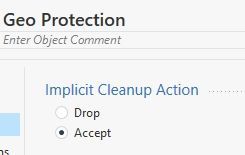
What happens if you delete that explicit cleanup rule and ensure that the Implicit Cleanup Action is set to action Accept under Advanced for that layer? Is there some reason you want to use an explicit cleanup rule without logging it?
Also try deleting everything in the Name column of the explicit rule and see what happens.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
- Deleted the explicit cleanup rule.
- Changed the implicit cleanup rule to accept for that specific layer.
- Changed Global Properties Track settings to not log implied rules
- Installed policy
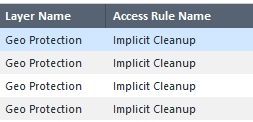
Still logging of Implicit Cleanup is showing for that particular layer.
One thing I can think of is the cp_log_export configuration we have to send logs to a destination syslog server, but I would expect that setting not to effect my SmartConsole log settings.
 |
Logging in SmartConsole still occurs:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I remember someone posting about exact same issue few months back...let me see if I can find that post and what the solution actually was.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What happens for traffic which matches a rule in the second layer which says not to log? Does it get logged twice, once (if so, on which layer?), or does it not get logged?
I'm wondering if the connection may be logged by all layers if any layer says to log it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe that's what I determined many moons ago when I noticed a similar issue: if a flow matches a rule in any layer that says to log, it will log for all the rules.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Never paid much attention to this problem, but I recall back in R65, whenever I helped someone with this, it always worked when you would set rule not to log. But then, again, there were no layers back then, so not sure if that was the reason why it worked...
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is it possible to request some hotfix for this? Since I have 2 layers, all allowed traffic passes the cleanup allow rule in the Geo Protection layer and then passes the allow rules in the Network layer. I don't want duplicate logging for the same traffic, and it doesn't help to see logs for the cleanup allow rule, the actual rules which determine access to our network/servers are the ones in the Network layer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats very valid request, for sure.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure, but I have a feeling this is an RFE, which would have to be handled through your local Check Point office.
I'll see if I can confirm with R&D.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you 🙏🏻
Anyway, I had to rollback the whole 2nd layer Geo Protection thing and stick to 1 layer because of this, the logging was useless otherwise since all traffic hit that 1 cleanup accept rule in the Geo layer and didnt log the actual rules from the Network layer which is the primary/meaningful one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just to close the loop on this, what you saw is, in fact, expected behavior.
If a flow matches multiple ordered layers and only one of the matched rules is set to log, you will see a log for all layers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm in this boat too, except I'm only seeing Single log entries - and they are part of the "Geopolicy" layer". Its cleanup rule allowing pass thru to the next ordered layer has taken over the logs!
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 15 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter