- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Fest 2025!
Join the Biggest Event of the Year!
Simplifying Zero Trust Security
with Infinity Identity!
Operational Health Monitoring
Help us with the Short-Term Roadmap
CheckMates Go:
Recently on CheckMates
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Management
- :
- Re: Renewal the DefaultCert internal_ca - date "No...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
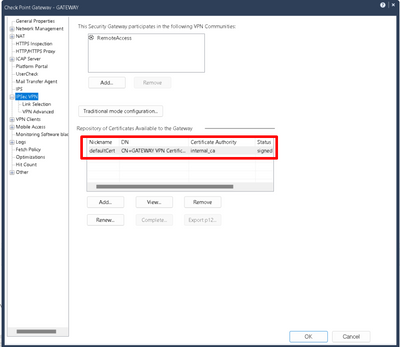
Renewal the DefaultCert internal_ca - date "Not Valid After" didn't change
Hello;
Today I had renew the Internal CA of my Checkpoint 5200 in vR80.10 using this process https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
After I had clicked on "renew" and "Install Policy" the certificate have change but not the "Not Valid After" date. This date will be expired in 2 weeks. The "Serial No" has change and the "Not Valid Before" date has been changed but with the day of yesterday, I don't understand why.
Here is the information of my product
Check Point Security Gateway | R80.10
Kernel: 2.6.18-92cpx86_64
Edition: 64-bit
Build Number: 462
Before the change I had those information
Not Valid Before: Wed Apr 15 12:54:06 2020 Local Time
Not Valid After: Sun Jul 24 15:04:16 2022 Local Time
Serial No.: 14942
After the operation, the "Not Valid Before" and "Build Number" have changed but not the "Not Valid After"
Not Valid Before: Tue Jul 5 12:36:58 2022 Local Time
Not Valid After: Sun Jul 24 15:04:16 2022 Local Time
Serial No.: 95282
Could you help me on this issue please ?
Regards
16 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From reading your posts, it sounds like you tried to renew a certificate issued by the Check Point Management Internal CA (e.g for a gateway), not the CA certificate itself. Your wording during your post is mixing these two topics.
But regarding your question: I think the Check Point Management Internal CA itself is about to expire. A CA cannot issue a certificate which lasts longer than its own end date. So please check the validity of the certificate of the CA itself.
If I'm right: For how to extend the validity of the internal CA itself, please see sk158096.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
As you said, the problem concern the ICA, This command show the Internal Certificate Authority certificate validity date which is 20 years by default.
# cpopenssl pkcs12 -in $FWDIR/conf/InternalCA.p12 -nokeys -nomacver -passin pass: 2>/dev/null | cpopenssl x509 -noout -enddate
notAfter=Jul 24 13:04:16 2022 GMT
My next step is to upgrade to R80.10 Jumbo HF take 290
I must install on Management Servers and Security Gateways before proceed with the renewal procedure of the ICA and then to the CA.
Thank you for your previous message and your link.
I will update the ticket with my procedure after all my actions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
make sure to not let it expire or you're in trouble 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why not just renew it from smart console instead? What does validity show there?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
because you can only renew the mgmt certificate via the console and not the root certificate, that one (root CA) requires a script from TAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I thought he meant below one, sorry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello
@the_rockThis one was the one that I've renewed and when I renew it, the date for "Not Valid After: " didn't change.
And the root cause of that is because the root CA will be not valid after Sun Jul 24, it can not be more than the date of the rootca
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
FYI the script I received from TAC has the following note:
1. All of the Gateways and Management servers in the environment are above the following Jumbo Hotfixes takes:
R80.40 Jumbo HF take 69
R80.30 Jumbo HF take 163
Fixed version for Security Management High-availability:
R80.40 Jumbo HF take 114
R80.30 Jumbo HF take 235
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For me it's R80.10 Jumbo HF take 290, I will have to do an upgrade before use the script.
The operation is scheduled for tomorrow noon.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I'm in a trouble.Via GAIAwebUI or CLISH
With GAIA i've this popup:
------------------------------------------
Import of package DeploymentAgent_000002205_1.tgz Failed
Error occurred while trying to read hf.config file
------------------------------------------
In CLI I've this message:
------------------------------------------
MGFWC01> installer import local /home/DeploymentAgent_000002205_1.tgz
Preparing package for import. This operation might take a few moments
Note: The selected package will be copied into CPUSE repository
Info: Initiating import of DeploymentAgent_000002205_1.tgz...
Interactive mode is enabled. Press CTRL + C to exit (this will not stop the operation)
Result: Import of package DeploymentAgent_000002205_1.tgz Failed
Error occurred while trying to read hf.config file.
------------------------------------------
Without upgrading CPUSE I can not upgrade the Jumbo Package.
------------------------------------------
Import of package Check_Point_R80_10_JUMBO_HF_Bundle_T298_sk116380_FULL.tgz Failed
This package is not supported by current Deployment Agent build.
Please install CPUSE version 2127 or above to import the package.
------------------------------------------
Have you some information that could help me ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The update for CPUSE itself ist not installed the same way, you install a update package (like JHFA) over CPUSE.
To update CPUSE itself, use this command:
installer agent install /home/DeploymentAgent_000002205_1.tgz
There is also a special button in Gaia Webinterface to update the CPUSE Agent (Install DA), next to the normal button to import a CPUSE package (Import package).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I've not this command available
> installer agent install /home/DeploymentAgent_000002205_1.tgz
CLINFR0329 Invalid command:'installer agent install /home/DeploymentAgent_000002205_1.tgz'.
TMGFWC01> installer agent
disable - Disable the Deployment agent service
enable - Enable the Deployment agent service
start - Start the Deployment agent process
stop - Stop the Deployment agent process
update - Update Deployment agent to a newer version
TMGFWC01> installer agent upd
TMGFWC01> installer agent update
TMGFWC01> installer agent update not-interactive /home/DeploymentAgent_000002205_1.tgz
CLINFR0329 Invalid command:'installer agent update not-interactive /home/DeploymentAgent_000002205_1.tgz'.
I've tried in Expert mode but I've not the command Installer at all with this privilege.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My fault. I didn't thing of the age of your Gaia/CPUSE installation. Back in the days of this old version, the procedure was different and the way how to do it was removed from sk92499.
You will find the procedure in the posted solution of this CheckMates thread:
https://community.checkpoint.com/t5/Security-Gateways/CPUSE-issue/td-p/87106
Please also read the comments below, there was a dash missing in the rpm command.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Alleluia
Thank you so much for this help, I've update CPUSE with your link and now I can install the jumbo package on management. (I did not use the point optionnal point 4 because of the Maintenance window required)
I've planned a new maintenance window tomorrow noon with:
-Upgrade CPUSE on the cluster of firewall
-Install the jumbo update on mgmr
-Install the jumbo update on firewall 1 & 2
-Renew ICA on mgmt only with the script that Checkpoint gave to me
-Renew defautlCert on cluster vith the smartConsole
Can you confirm that the ICA is only needed on management and not on the cluster of firewall (Firewall 1 & firewall 2)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm not familiar with the ICA renewal process in detail (20 years not yet reached :)) and I have never seen this script from TAC myself. You have to follow the procedure, TAC gave you, or ask someone who did it in the past.
But one simple answer, I can give to you: The ICA is hosted on the management. The gateways use certificates issued by that ICA (at least for SIC, sometimes also for IPSec VPN or various web portals), but they do not host the ICA. Some Check Point admins also issue certificates to users from that ICA, so the scope can be even larger. In some cases you would need to rollout the new ICA cert to the affected clients trust stores.
If you are just using that ICA for the SIC of these one gateway cluster, your are fine after renewing ICA and reissuing gateways certs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
The update was a success.
With the new command, I updated the CPUSE of the management and the 2 firewalls,
Installed the JumboPack on each of them, Management AND Firewall
Used the script that TAC gave me to update the ICA.
Updated the DefaultCert via the SmartConsole.
Thank you very much for your advice and help.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 13 Feb 2025 @ 03:00 AM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - APACThu 13 Feb 2025 @ 03:00 PM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - EMEAThu 13 Feb 2025 @ 02:00 PM (EST)
Navigating the Cyber Frontier: A Check Point Executive Briefing - AmericasFri 14 Feb 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 33: CPX 2025 terugblik!Tue 18 Feb 2025 @ 03:00 PM (CET)
Why Adding SASE to Your Network Infrastructure is a Win-Win - EMEATue 18 Feb 2025 @ 02:00 PM (EST)
Why Adding SASE to Your Network Infrastructure is a Win-Win - AMERICASThu 13 Feb 2025 @ 03:00 AM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - APACThu 13 Feb 2025 @ 03:00 PM (CET)
Navigating the Cyber Frontier: A Check Point Executive Briefing - EMEAThu 13 Feb 2025 @ 02:00 PM (EST)
Navigating the Cyber Frontier: A Check Point Executive Briefing - AmericasFri 14 Feb 2025 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 33: CPX 2025 terugblik!Tue 18 Feb 2025 @ 03:00 PM (CET)
Why Adding SASE to Your Network Infrastructure is a Win-Win - EMEATue 18 Feb 2025 @ 02:00 PM (EST)
Why Adding SASE to Your Network Infrastructure is a Win-Win - AMERICASAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter