- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Ask Check Point Threat Intelligence Anything!
October 28th, 9am ET / 3pm CET
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- R80.20 HTTPS Inspection Bypass for Office365
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.20 HTTPS Inspection Bypass for Office365
Good morning,
Here's our situation. We'd upgraded from R77.30 to R80.10 a couple months ago to take advantage of new features and to implement HTTPS Inspection, which we'd been told would be a more stable experience. Once we'd upgraded and during testing of HTTPS Inspection, we found our general O365 experience to be lacking. Microsoft recommends not to inspect that traffic, to have the cleanest connection between client and their servers.
We were going to apply the SK119562 Hotfix to our R80.10 Take 112 environment to take advantage of the Dynamic Objects, but ran into issues. Lo and behold, R80.20 went GA, so we changed our tact to upgrading to R80.20. We found the Updatable Objects for O365/Azure, and thought we could use those in our Bypass Rules. We've been told that those can only be used in Access Policies. Which is a shame, as this is exactly what we need.
1. Should we just use the Dynamic Objects in the Destination column in HTTPS Inspection rules, forgetting about these new "Updatable Objects"?
Unfortunately we have tried employing these Dynamic Objects in R80.20 and get this error.
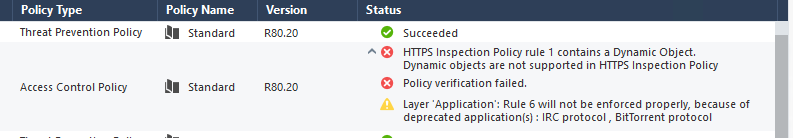
2. Does R80.20 just work better with Office 365 and there is no need for a specific Bypass Rule?
3. Any other suggestions/solutions?
I cannot believe that this would not have been thought about during the EA period for R80.20, especially as this SK119562 Hotfix was made available.
Regards,
Eric
17 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe the plan is to support those updatable objects in the HTTPS Inspection policy, but it's not supported currently.
It's possible this SK may also still be relevant (even though it mentions R77.20): Bypass for Office 365 in R77.20 HTTPS Inspection policy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It was picked up during the EA process, particularly with the new Updatable Objects in R80.20 being so vital to getting O365 to work. There is a JHF coming to support this but no estimate on timescale. It's a bit of a nightmare to add in the objects for O365 within the HTTPS Inspection policy but that seems to be the only way to do it at present. It has to be a source/destination bypass rule within the HTTPS Inspection policy otherwise the first packet is inspected to identify the application which breaks the connection to O365.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Unfortunately, updatable objects are not supported in HTTPS Inspection in R80.20.
You can sumbit RFE thru your SE to get support of O365 in HTTPSI policy in R80.20
Thanks,
Meital
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does Checkpoint have a best-practices document / whitepaper that explains how they recommend successfully deploying Office 365 services behind their Gateway? With so many customers making this migration to O365, this would be very helpful.
If no document exists, it may be beneficial to include best-practices for customers that are "all in" (use the heavy inspection blades + https inspection), "mostly in" (use heavy inspection blades, not https inspection), or FW-only customers.
It may also differ by code version, aka Updatable objects in R80.20, or some other method in previous versions.
Thanks for your consideration!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assume you mean clients behind your gateway ![]()
If you're using HTTPS Inspection: How to allow Office 365 services in Application Control R77.30 and above
If you're not using HTTPS Inspection but using R80.20, you can allow access to the Office 365 Services in your Access Policy:

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, I meant clients behind the GW that are connecting to O365, thanks ![]()
So, for now, if using HTTPS inspection, use App Control and don't try to bypass HTTPS (even though MS says to do so).
In the future, if Updatable objects can be used in HTTPS bypass rules, it may make sense to then allow the updatable objects in access control policy, and bypass HTTPS inspection for those same objects.
Thanks, this is helpful info.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello all, any news about a official best pratices doc or whitepaper from Checkpoint?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
they still did no implemented the dynamic objects for HTTPs Inspection policy so i don't believe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dor, did you have implemented https inspection on r80.20? the kernel parameter enhanced_ssl_inspection is on or off?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This has been an issue for some time.
The way we have had to implement the bypass is to import objects into the SMS via an API call and then use these objects within the HTTPS Inspection policy. That's been the only way to bypass HTTPS Inspection. If it isn't bypassed, there are no end of issues with authentication services as the first packet always gets inspected and that breaks trust.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I find importing gazillions of IPs crazy, impractical and really frustrating for end-users where every day something stops to work because M$ changed their IP range or because of the way HTTPS-I is currently implemented.
So, CheckPoint, please come up with an easy-to-deploy solution for this for all firmware supporting HTTPS-I (not only R80.20). I know this is partly not a vendor problem but it can only be properly solved by you.
Being polite I will skip my comments on the way M$ forces FW admins to compromise security for their online services to work. ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi We have the same issue. we are currently doing the bypass by creating a custom Office365 Application/site.
It contains 6 urls and seems to have solve the main problem for us.
currently we have in the list
I hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi!
Are there any news regarding using domain objects in HTTPS inspection in R80.20?
BR,
Bernhard
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any update on this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any News?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am not aware of any specific plans to use Domain Objects in the HTTPS Inspection policy.
That said, we should see some improvement in upcoming releases.
That said, we should see some improvement in upcoming releases.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We plan supporting it in R80.40 planned for the end of this year, and we're looking for EA customers for EA program to start in 2 months.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 25 | |
| 16 | |
| 6 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 2 |
Upcoming Events
Wed 22 Oct 2025 @ 11:00 AM (EDT)
Firewall Uptime, Reimagined: How AIOps Simplifies Operations and Prevents OutagesTue 28 Oct 2025 @ 11:00 AM (EDT)
Under the Hood: CloudGuard Network Security for Google Cloud Network Security Integration - OverviewWed 22 Oct 2025 @ 11:00 AM (EDT)
Firewall Uptime, Reimagined: How AIOps Simplifies Operations and Prevents OutagesTue 28 Oct 2025 @ 11:00 AM (EDT)
Under the Hood: CloudGuard Network Security for Google Cloud Network Security Integration - OverviewWed 05 Nov 2025 @ 11:00 AM (EST)
TechTalk: Access Control and Threat Prevention Best PracticesAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


