- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Quantum SD-WAN Monitoring
Watch NowCheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
MVP 2026: Submissions
Are Now Open!
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: R80.10 Syslog Exporter
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.10 Syslog Exporter
Via Check Point Support you get a Syslog exporter for SIEM applications for R80.10 Managment.
Which allows an easy and secure method for exporting CP logs over syslog. Exporting can be done in few standard protocols and formats.
Log Exporter supports:
- Splunk
- Arcsight
- RSA
- LogRhythm
- QRadar
- McAfee
Log Exporter is a multi-threaded daemon service, running on a log server. Each log that is written on the log server is read by the log exporter daemon, transformed into the desired format and mapping, and then sent to the end target.
Installation on R80.10 Jumbo Hotfix Take 56 or higher.
Syntax:
# cp_log_export add name <name> [domain-server <domain-server>] target-server <target-server> target-port <target-port> protocol <(udp|tcp)> [optional arguments]
|
Command Name |
Command Description |
|
add |
Deploy a new Check Point logs exporter. |
|
set |
Updates an exporter's configuration. |
|
delete |
Removes an exporter. |
|
show |
Prints an exporter's current configuration. |
|
status |
Shows an exporter's overview status. |
|
start |
Starts an exporter process |
|
stop |
Stops an exporter process. |
|
restart |
Restarts an exporter process. |
|
reexport |
Resets the current position, and re-exports all logs per the configuration. |
Regards,
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Tags:
- performance
53 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Where can I get the installation package?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Heiko,
If you've had a chance to use this tool, please advise if it is possible to:
1. Create separate processes for individual gateways writing to the log server?
2. Resolve gateway names before shipping logs to the destination SIEM for the "Origin" fields?
Thank you,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Vladimir,
You can install multiple instances of the log exporter but you cannot separate them by gateways.
The tool reads from the log files (such as fw.log) in your $FWDIR/log directory.
There are some filtering capabilities, but for the first release, they are mostly focused on key (field) based filters and not value based filters.
You can filter by 'action' but not by 'accept'/'drop'.
We plan to add more advanced filtering capabilities in future releases.
regards,
Yonatan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the info.
Any plans to re-introduce syslog output directly from gateways, the r77.30 style?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you referring to the OPSEC LEA tool?
If so, I personally am not aware of any such plans to refresh it, but as far as I know, that tool still exists in R80.10.
The new log exporting tool is a direct replacement for the CPLogToSyslog tool. We will be retiring the CPLogToSyslog tool, but I don't know of any plan to retire other tools (such as the OPSEC LEA tool).
Regards,
Yonatan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
the tool is very helpful.
We have two customers who use it.
Can you say something about how it's gonna be included in the next HFA?
Little note:
The Syslog entry contains firewall rules and thread rules in one line. So some fields have the same name, we have the problem that we cannot index the fields in LogRythm.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Heiko,
The plan at this point in time is to have the tool directly integrated into R80.20 (no hotfix needed).
Regarding a future R80.10 HFA integration - at this point in time we have not yet reached a decision on this subject.
As to your point on LogRhythm - it's true that there are many instances where fields will be sent more than once.
Sometimes it will be the same field (that is, both instances will have identical information) and sometimes it will be different fields, such as in the case of multiple layers (each layer will have an action field).
We plan to address the former to some degree in the next log exporter release, but the later is inherent to the way our logs are built. I don't think there is any feasible way to resolve this while still keeping all the relevant data in the log.
Those fields appear twice because they represent data which appears twice (like the above example, of one action per layer).
We have been in contact with LogRhythm, and they are aware of the new tool, and I also know that they have been working on it from their end.
However, I cannot speak for them and am not privy to the details of how/if they plan to address this.
Regards,
Yonatan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Yonatan,
thx for this info.
Regards,
Heiko
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you also discussed this with AlienVault? You still have a partnership with them, yes?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
AlienVault recently updated their Plugins List adding in the R80 plugins options. For R80 with the logexpoter function AlienVault will utilize the CEF format.
I have tested this with a customer and their AlienVault USM Anywhere is correctly receiving data.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
John ... is there any chance of making the plungin .cfg file available? ... your post is the only reference I can find regarding the export of logs from R80 to AlienVault....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, I am talking about R77.30 add-on: How to configure R77.30 Security Gateway on Gaia OS to send FireWall logs to an external Syslog serv...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am also interested in this since I have one firewall cluster for PCI that I need to syslog only its data into a Splunk.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are planning to release this tool more generally very VERY soon ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In witch hotfix?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The official release: Logs Exporter - Check Point Logs Export
To answer your question about "which hotfix" christian konner, it's installed over a R77.30/R80.10 management/log server (not gateway) with a recent jumbo hotfix.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, I've used the CPLogToSyslog package to export the check point logs (based on the cplogtostosyslog rules) to an external syslog server (Extreme Networks Management server) for automate the process for block ip address to the edge of the networks via ExtremeControl NAC.
Now seems that the new method described above is compatible only with some SIEM, but is not general as the previous one, and most important is not possible to define rules for filter was is important to export to the SIEM.
Is this true?
How is possible to know more and test the new tool for see if is still possible to integrate with the Extreme Management syslog server.
Thanks,
Antonio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sk122323 Logs Exporter - Check Point Logs Export says that Log Exporter supports:
SIEM applications: Splunk\Arcsight\RSA\LogRhythm\QRadar\McAfee\rsyslog\ng-syslog and any other SIEM application that can run a syslog agent.
Protocols: syslog over TCP or UDP.
Formats: Syslog, CEF, LEEF, Generic.
Security: Mutual authentication TLS.The ability to export logs/audit or both.
Filter out (don't export) firewall connections logs.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Has anyone heard more about being able to filter out firewall connection logs (as Günther mentioned from the sk122323?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
when will be supported the filter out of all the blades (Threat Emulation, IPS, ThreatAV, etc...)?
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Antonio,
We plan to address this gap in a future release.
I don't have any information about what exactly the next release will contain nor when it will be released.
I've created a log exporter guide in another post that covers this and many other questions.
You can find it at Log Exporter guide.
I hope you'll find it helpful.
Regards,
Yonatan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Would it be possible to get sample sanitized logs for each blade type for development use please?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You should be able to stand up a test gateway with an evaluation license and generate whatever logs you need.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It sounded too good.
On my lab R80.10 with T91 it fails towork as it seems to get in a pickle about permissions.
This showed up in /opt/CPrt-R80/log_exporter/targets/SYSLOG/log/log_indexer.elg:
[log_indexer 27834 4139846544]@fwmgmt[3 Apr 14:03:10] SyslogUDPSender::sendPacket - failed to send packet: <30>Tue Apr 3 14:03:10 CheckPoint Syslog started
[log_indexer 27834 4129356688]@fwmgmt[3 Apr 14:03:10] SyslogUDPSender::connec - failed to send initial message with handler to [loghost(-1):514]
I initiated this with:
[log_indexer 27834 4139846544]@fwmgmt[3 Apr 14:03:10] SyslogUDPSender::sendPacket - failed to send packet: <30>Tue Apr 3 14:03:10 CheckPoint Syslog started
[log_indexer 27834 4129356688]@fwmgmt[3 Apr 14:03:10] SyslogUDPSender::connec - failed to send initial message with handler to [loghost(-1):514]
The host loghost is known as object and it is present in /etc/hosts
Other syslog traffic from GAIA works without a problem. ..... (come to think of this. Might this be the issue?)
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Hugo,
This is a known issue that stems from an attempt to improve the interface (an attempt which sadly backfired...).
The original parameter name was 'target-ip'. It was changed based on customer feedback to 'target-server', but the backend stayed the same - expecting an IP-address.
Add to this the fact that we didn't implement a verification mechanism on the input (to make sure it's a valid IP address) and we have a bug.
We already have a task for this and it will be addressed in the next release.
For now, the simple fix is to use an IP-address for the 'target-server' parameter.
Hope this helps,
Yonatan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Check! That fixed my issue.
(No stroopwafels for who ever made that half way change.)
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hugo van der Kooij - Any comment that refers to stroopwafels gets a thumbs up in my book 😉
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I was able to successfully configure it in MDS environment. And also the cp_log_export status showed me correct information.
But on a SMS 1 - 210 appliance running on latest take(103) R 80.10 when i installed and configured the log_exporter. i got this warning(Failed to find the env variables.... ) but it continued to send the logs to syslog server.
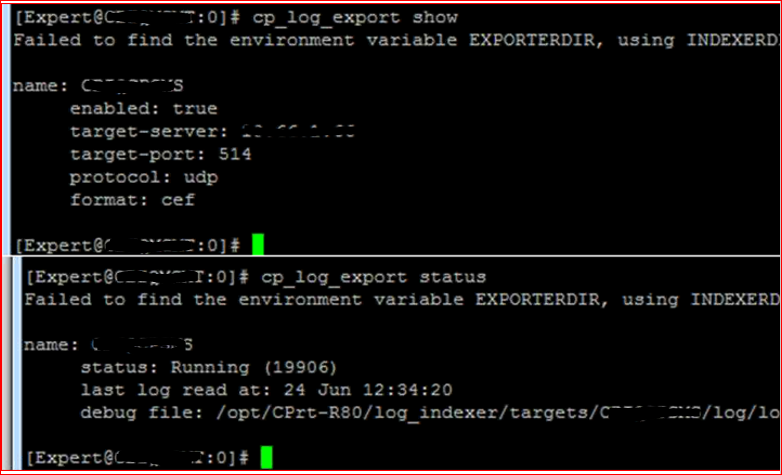
Just later when i tried to see the status of the same, i got this error:-
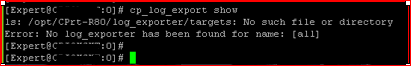
it seems somehow it used the log_indexer directory instead of EXPORTERDIR, not sure why
any advise. ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Biju,
When you install the log exporter hotfix it adds the $EXPORTERDIR environmental variable.
Since the hotfix doesn't require a reboot, you need to manually reset the ssh connection for the new variable to be added to your environment.
Since you didn't log out the variable didn't exist when you tried to deploy it, and so it generated an error and used the $INDEXDIR variable instead (in the status output you can see the location is under 'log_indexer' instead of 'log_exporter').
This is not an optimal solution. I would recommend deleting the existing the deployment (using the delete flag) and redeploying it so that it's deployed in the correct location. If the delete flag doesn't work you might have to manually delete the exporter (cpstop; delete the folder; cpstart).
If you want to verify if the $EXPORTERDIR variable exists, you can just try to write it down in expert mode and use the auto-complete (tab) to see if the OS environment recognizes the variable or not.
(I actually remembered this as being blocked because of those errors, but I guess I'm misremembering...)
P.S. just to clarify, this deployment should still work as expected, but as the 'show' flag error shows, it's not seamless, which is why I recommended to remove/redeploy.
Regards,
Yonatan
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 13 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 4 | |
| 4 | |
| 3 | |
| 3 |
Upcoming Events
Tue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


