- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Private to Private NAT on IPSEC VPN
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Private to Private NAT on IPSEC VPN
Hi Experts,
We're planning to build IPSEC Site to Site VPN with our clients. Our Internal subnets for VPN domain is 172.16.0.0/24. In order to hide our Internal LAN , we've been asked to NAT to another Private Subnet so this can be advertised as VPN domain. This looks like Private to Private NAT. I'm not sure about this.
Could some one please advise me with NAT configuration Thanks in Advance.
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your NAT configuration should reflect the intended use:
I.e. will you be accessing peer's resources via this VPN? If so, you can use many to one (hide NAT). I would suggest to hide behind single host, but define same host's IP as another Network Object with /32 mask and use it in your Encryption domain. Some vendors are partial to the idea of establishing tunnels to hosts, instead of between subnet pairs.
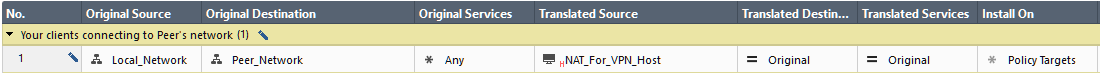
Where "NAT_For_VPN_Host" IP is the same as the /32 network you'll include in your Encryption Domain.
If your peer's clients will be connecting to you, you'll have to actually create manual NAT rules for each of your internal resources, something like this:

With NATed_Server IP being in the range of the subnet you have included in your encryption domain and the Local_Server being actual IP of your resource.
Place these NAT rules on top of your NAT policy to avoid interference with other rules that may-be using same sources.
Cheers,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Adding to Vladimir, If the VPN communication is between 2 subnets and flow will be bidirectional then use any fake subnet and NAT with entire subnet. Like below.
172.16.0.0/24 NATed to 192.168.2.0/24 (This subnet is fake subnet, means not a part of your LAN and it should be part of encryption domain)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Gaurav,
So if you create a network 192.168.2.0/24, add it to your encryption domain, you can then create a NAT rule using hide NAT? Can you just elaborate on this a bit as I cannot see how this would work? I need to configure a site to site VPN with a customer and we cannot use our existing private subnet as this is currently in use on the customer side. We would preferr not to NAT behind a public IP either so this solution might be perfect.
Thanks,
Dan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Daniel,
You can use IP Pool NAT in which entire subnet will be NATed to different subnet. Please see below NAT rule. You can use subnet as a object or IP Ranges.Please note that here peer end has also have to do NAT and that NATed subnet need to put at destination. Again it depends peer end is giving public IP or private IPs for interesting traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Guarav,
Excellent, thank you very much for your quick reply. I will try this approach on a site to site VPN I am working on.
Thanks,
Dan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Gaurav,
I do not think that you can use the subnet object for a source NAT (in column 4), only the IP Range or a single IP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vladimir,
I have used IP Ranges as source NAT but not used subnet object. when I tried to add object, subnet was also one option so I just mentioned. Good suggestion.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Srinivasan,
I’m addressing the relevant people in order to provide an answer for your question.
Regards,
Adiel Ashrov
Software Engineer
Management Application
@Check Point
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi guys!
Any answer on this?
We're planning an IP range change (ex: 10.10.10.0/24 to 172.16.0.0/24) we have different services in that IP range and to make sure we don't have any issues, I'd lke to do a 1-to-1 NAT. Keeping the old IPs reachable, if we forget to migrate a service to the new IP range.
So service A (ex: AD DC) would answer on 10.10.10.2 and 172.16.0.2)
Am I correct in my assumptions?
Merci!
CL
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
When you give IP Ranges in NAT policy then it will automatically do 1to1 NATing. like 10.10.10.2 to 172.16.0.2.
My assumption is, at a time only one IP will give answer for specific service.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 16 | |
| 7 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


