- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Need auto execute command script like EEM in C...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Need auto execute command script like EEM in Cisco
Hi, My Security Gateway CPU is spiking randomly. I want to configure a script to collect output of some pre-defined commands like EEM in Cisco. But I'm not getting the script for CheckPoint. Any help much appreciated
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Checkpoint is based on redhat Linux. you can create python or bash scripts to collect the information.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for replying. I want to set up a script which will execute a command "fw tab -t connections -u > /var/log/Connections_Table.txt" when my gateway CPU goes above 90%. Could you please help me with script and steps?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You'd have to write a script that:
1. Monitors CPU (remember: there is more than one core)
2. When CPU reaches your desired threshhold, run the appropriate commands
Meanwhile, you might try using cpview, which can tell you a lot about what's going on.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Its happening randomly, that's why I thought of configuring script. But, I don't know how to do. If you have any document or document related to scripting, please share. It will be helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
cpview has a history mode that will likely be helpful.
It won't require scripting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Cpview will record the information, I believe every 1 mint. I have seen it before the cpu spikes in sub seconds and cpview will not catch it. we had to use top with lower timer to catch it.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's not fullproof, true, but it's a good starting point that doesn't involve writing scripts. ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Houssameddine Zeghlache in regards to the granularity of cpview history mode being 1 minute, I looked into it more closely when researching my book and the per-minute historical numbers reported by cpview are the average of two samples taken 30 seconds apart. So a spike of some kind that occurs but is not still happening during one of the samples taken every 30 seconds will not show up at all in cpview's history mode, and this was noted in my book. Sar takes more of a running average over its sampling intervals and is some cases is preferred over cpview depending on what you want to inspect. Here is the table from the second edition of my book where these preferences are summarized, these are just my opinion of course:
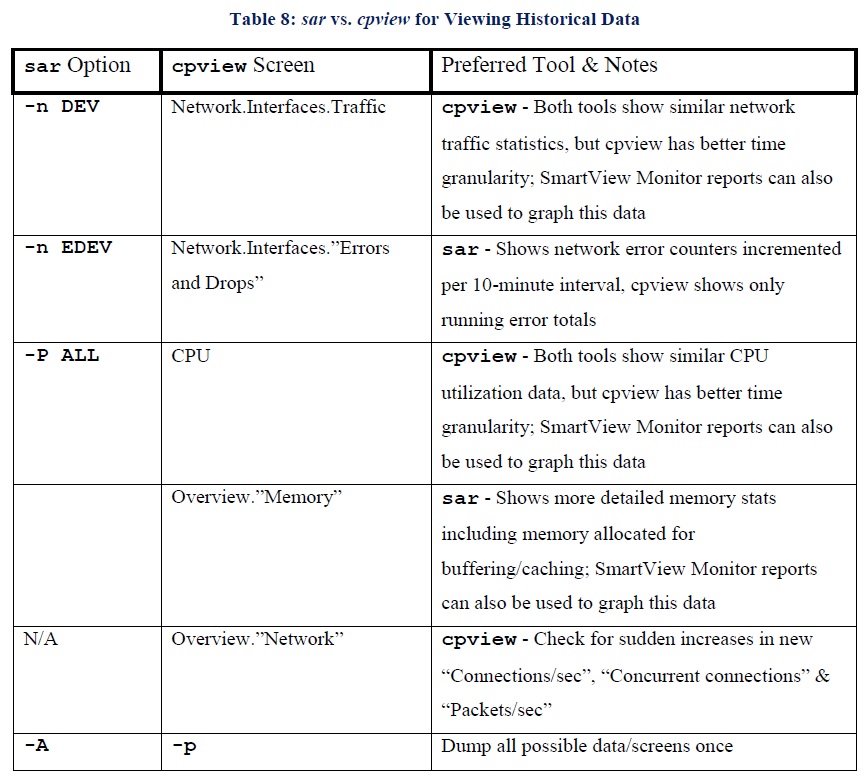
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tim, In my case CPU is spiking intermittently and by the time I login it will became normal. I know one thing, the CPU is spiking when the no. of connection is increasing suddenly from 40k to 80k.
I'm stuck here, I want to find out what are these connections which is causing CPU spike. Could you please help me out?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tim, forgot to say one more thing, firewall policy logs are disabled for all policy except clean up rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK since logging is only for cleanup it is probably not fwd and its associated logging functions spiking the CPU.
First order of business for a spiking CPU is determine what kind of execution is eating the most cycles during the problematic period. sar can get you going in the right direction here, run sar in historical mode like this (assume that the day number it happened was 7 in this example, for today just omit the "-f (filename)" argument):
sar -f /var/log/sa/sa07 -P ALL
This will show where specifically the CPU percentage-wise for each type of execution, namely:
%user - process execution, generally this should be fairly low on a gateway unless features that cause process space trips such as HTTPS Inspection are turned on
%nice - irrelevant on a gateway, important on a R80+ SMS though
%system - kernel execution, roll up of the sy/si/hi/st shown in top
%iowait - waiting for I/O, should be very low (<5%) on a gateway unless policy is currently being installed, if higher than that during your spikes the firewall is almost certainly low on memory, post output of free -m
%idle - hopefully self-explanatory
Please report where most of the CPU cycles are going during the spikes and we can go from there. If it is spiking in %system as shown by sar, you're going to either have to catch the problem live while running top, or run top in batch mode so we can see which one of sy/si/hi is the culprit.
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
you might start playing with it in lab by checking some scripts like this one an adjust for your needs
https://stackoverflow.com/questions/15655969/shell-script-for-cpu-load-monitoring
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have an old, outdated script from years ago ![]()
Usage: Before running the script please setup top so it always show all CPU's;
#top
Press 1
Press shift + w
Press Enter
Exit top
Verify that it shows all CPU's by entering top again Now we can run the script;
#dos2unix monitor.sh
#chmod +x monitor.sh
#nohup ./monitor.sh &
The script will now run in the background and will take specific outputs related to performance every 30 seconds.
They will be written into /var/log/output.txt
To kill the script;
#ps aux | grep monitor.sh
#lkill -9 [pid of monitor.sh]
You can change the time value to your needs.
#!/bin/bash
#
#
clear
echo "To stop the script press CTRL+C"
echo "Starting to probe the system . . "
echo ======================================================================== >> /var/log/output.txt
echo "=== The beginning of the probing process ===" >> /var/log/output.txt
date >> /var/log/output.txt
echo ======================================================================== >> /var/log/output.txt
sleep 5
while end_loop=0 # while this condition is TRUE -
do
echo "New run, collecting....."
echo "To stop the script press CTRL+C"
echo " "
echo ============================================================= >> /var/log/output.txt
date >> /var/log/output.txt
echo ============================================================= >> /var/log/output.txt
echo " " >> /var/log/output.txt
echo " " >> /var/log/output.txt
echo cat /proc/meminfo : >> /var/log/output.txt
echo "------------" >> /var/log/output.txt
cat /proc/meminfo >> /var/log/output.txt
echo " " >> /var/log/output.txt
echo cpstat os -f multi_cpu : >> /var/log/output.txt
echo "------------" >> /var/log/output.txt
cpstat os -f multi_cpu >> /var/log/output.txt
echo " " >> /var/log/output.txt
echo top -n1 -b : >> /var/log/output.txt
echo "------------" >> /var/log/output.txt
top -n1 -b >> /var/log/output.txt
echo " " >> /var/log/output.txt
echo ps -auxf : >> /var/log/output.txt
echo "------------" >> /var/log/output.txt
ps -auxf >> /var/log/output.txt
echo " " >> /var/log/output.txt
clear
echo " "
echo "GOING to SLEEP for 5 seconds, run complete"
echo " "
echo " "
echo "Please press CTL + C in order to break the script"
sleep 30
done
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
But best would be to ask CP TAC for the CPU spike monitor script "spike_monitor_cpk.sh" by Ariel L. Dor ![]() .
.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 15 | |
| 13 | |
| 9 | |
| 8 | |
| 6 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


