- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Moving from 71.30 to 80.10 - two problems left
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Moving from 71.30 to 80.10 - two problems left
I've made a clean install of GAiA R80.10 on new hardware (OpenServer), manually create all network objects, groups, services, rules and so on. After two unsuccessful attemps of switching servers I need to solve two problems.
First: I cannot send/receive emails trought firewall.
I have rules with smtp resource using match patterns to filter nonexisting addresses (up to 90% of incoming traffic)

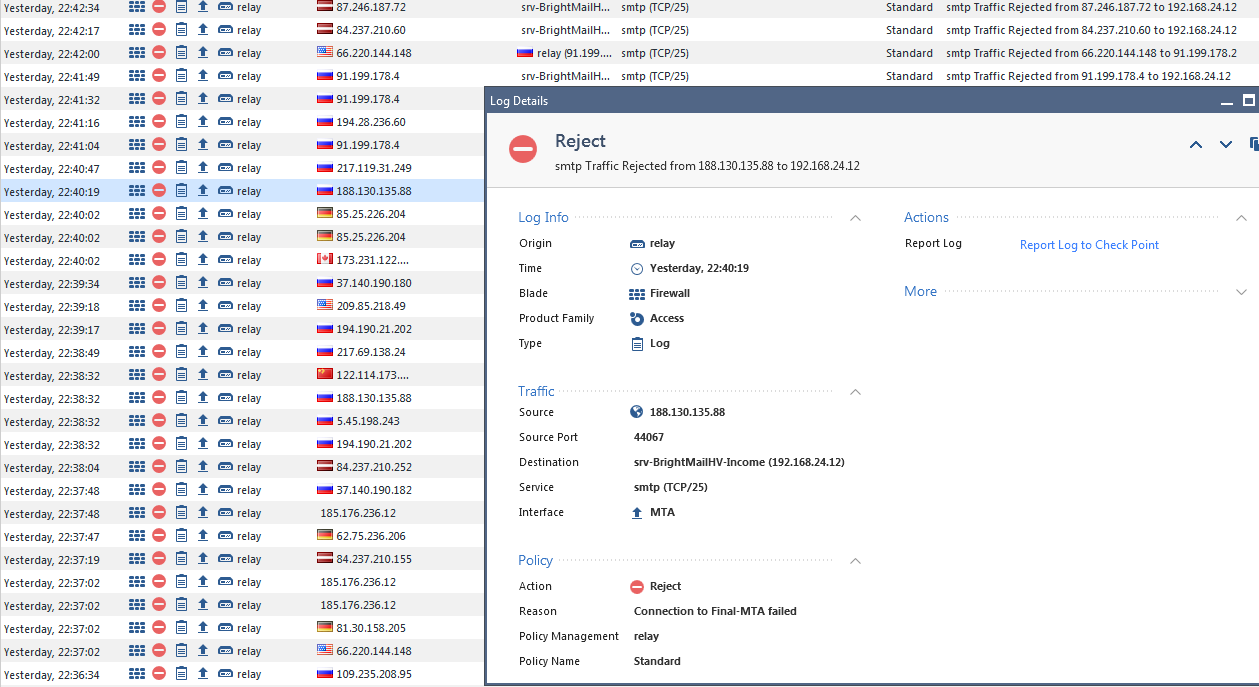
Firewall accept emails from external senders but don't forward them to internal mail server (stated inside smtp resource):
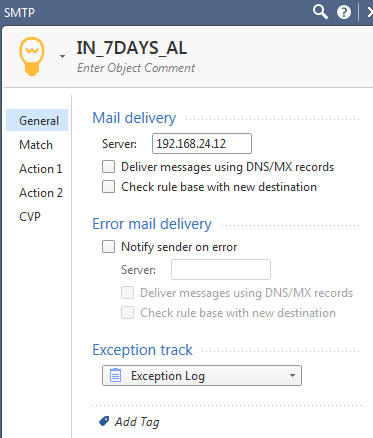
Log shows "Connect to final MTA failed" (what a strange interface - MTA?)
I defined a new rule (100) allowing Any source to internal mail server but this rule works only in short period of time (about 10s) while policies is installing on the gateway (using correct interface - eth2):
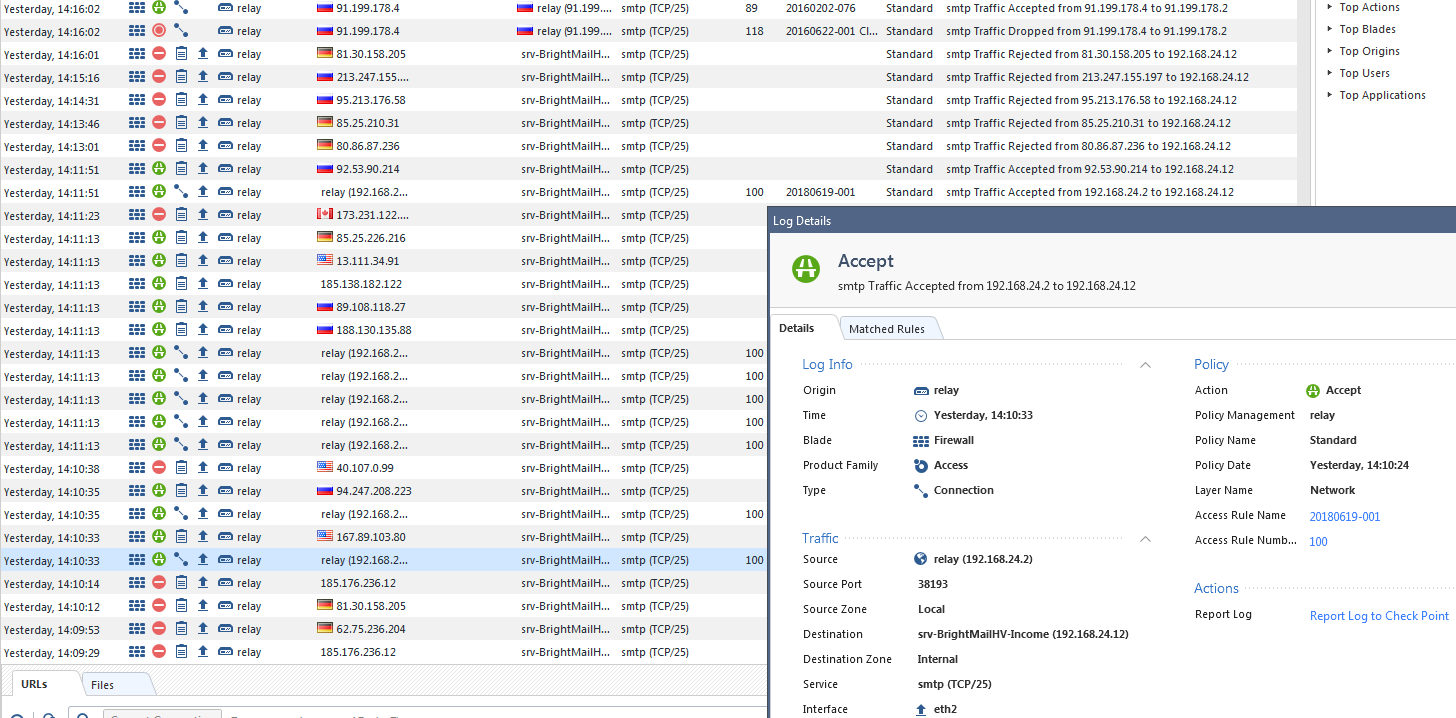
What I'm doing wrong?
Second problem: snmp-read
I have rule allowing Nagios server to send snmp read requests to the group of servers (external and in DMZ). Logs show everything is fine:
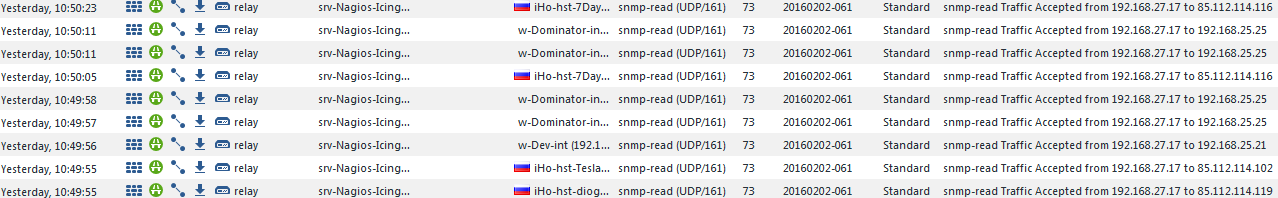
In real life requests to the external servers works fine but to DMZ (192.168.25.*) - timeout.
Labels
- Labels:
-
Policy Installation
-
SmartConsole
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For the SNMP issue, any chance that rule (rule 73?) is now also being subject to the NAT policy? I believe you can double-click on that line to get more details of the log entry and perhaps NAT is taking place. You can also use 'fw monitor' to see the fate of that packet:
fw monitor -e 'accept src=192.168.27.17 or src=192.168.25.25 or dst=192.168.27.17 or dst=192.168.25.25;'
You'll get a lot of output here (and the filter is intentionally loose and not pairing the src/dst of the packet, so it will show possible NAT on the output chain in each direction).
Do you have SecureXL enabled? Perhaps disable it and check the request, and re-enable it afterwards. 'fwaccel off' and 'fwaccel on'. SecureXL can do weird things to the connections (good and bad).
Hope that gets you on the right track!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Duane, thank you for giving me a right direction! 🙂 I found a misconfiguration in GW's network configuration: DMZ was stated in two network interfaces (direct and as a member of the networks group).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's great to hear. Was NAT being applied in this case? Or was that an anti-spoofing problem? I'm curious to know the final result.
Thank you and I hope you are able to fix the other SMTP issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
After migration from R77.30 to a clean install R80.20 we had same problem with snmp from our nagios server to external and dmz systems. Logs look fine but snmp get timeout.
fw monitor shows me only the first get-request paket passing only preIn ("i") and nothing more.
(checked NAT and antispoofing -> is ok)
My actual workaround:
I made a new service object with UDP/port 161 and without protocol. After changing the rules with service snmp to the new object and it works.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the purpose behind your SMTP resource object?
That uses a security server, which I believe have been largely deprecated in R80.10.
We have a proper MTA (using Postfix) which might be better depending on the specific use case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The purpose of SMTP resource - to filter incoming emails for non-existing addresses in our domains (up to 95% emails drops here significantly reducing the load of internal mail server).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Theoretically, as long as you're not using Threat Emulation, this should still work, even in R80.x.
That said, there seems to be an issue that might require a hotfix: Emails remain in the spool when SMTP Resource Rule is defined
Note that if you are using Threat Emulation, then you need to use the MTA that goes with it rather than SMTP Resources: ATRG: Mail Transfer Agent (MTA)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've opened a support ticket for this sutuation. Will wait for a hotfix on JF take 112.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 16 | |
| 15 | |
| 8 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


