- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Limit of concurrent connections
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Limit of concurrent connections
During heavy load on your firewall busiest periods you can get connection failures I read. As mentioned in other threads on this community you can run this command to see if your firewall reached the limit:
fw tab -t connections -s
But default on new installations og Gaia it's not configured a limit nmber of concurrent connections. On your firewall object in SmartConsole it's set to automatically:
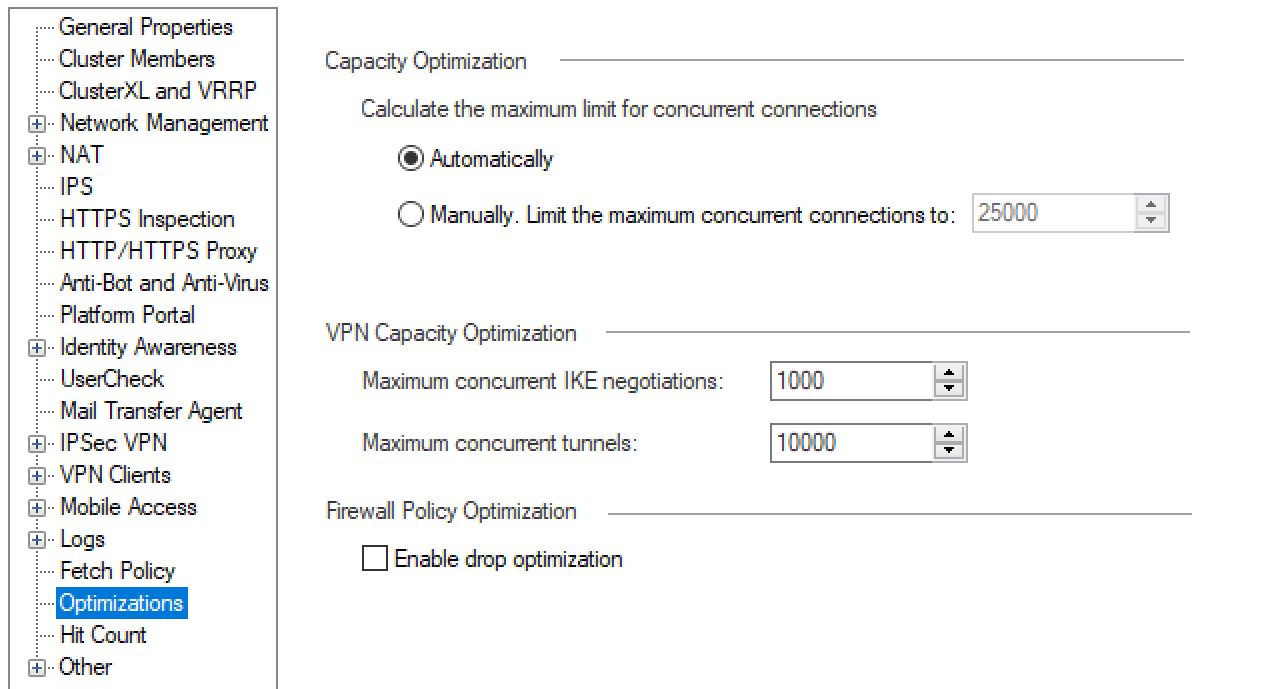
So my question is what is the limit actually set to then? My gateway has 16GB of RAM. Output of the above command:

I see that since boot up that the peak was at 21394 concurrent connections. But since I actually don't know the limit and if this is low or high what do I get out of this command? How do I know if new connections were dropped (not from firewall policy) because firewall could not keep track of the new connection?
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The setting "Automatically" is selected by default if the firewall object is set for Gaia as the OS. If you want to set it manually, the settings depends on your traffic and resources. The setting affect the VPN kernel. Lets assume you have 1000+ remote users, which are connect to office network thorugh the mobile access blade, it creates multiple connections ( from user to gateway, from gateway to internal rdp server). So on the example environment you should increase the maximum concurrent connections, by default maximum is 25000, increase the limit 27000 (2 times 1000). You can read for more information >
Capacity Optimization and Connections Table
If you set the maximum conn manually and for somehow it reached the limit , you can run the following command to check if there is dropped connection because of connection limit.
fw ctl zdebug + drop
You may see something like that >

By the way you can can run following command to gather statistics about the connections .
fw ctl pstat
Connections:
17907 total, 2214 TCP, 10855 UDP, 21 ICMP,
4817 other, 0 anticipated, 8 recovered, 8 concurrent,
68 peak concurrent
*
total - Since last machine boot time.
other - Other protocols (Not TCP/UDP/ICMP)
concurrent - At the time the output was taken.
peak concurrent - Since last machine boot time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Indeed, fw ctl pstat is your friend to see connections tables. I purposely took an example from 32bit gateway as you can see that box actually has a lot of RAM (64GB) but it can only use 4GB for connections (actually around 3GB realistically).
Just make sure usage in percentage is not high and Aggressive Aging is not active - then you are all good. And yes - automatically means that RAM will be allocated as needed for connections until exhausted.
[Expert@fw1]# fw ctl pstat
Virtual System Capacity Summary:
Physical memory used: 15% (8285 MB out of 53867 MB) - below watermark
Kernel memory used: 8% (4512 MB out of 53887 MB) - below watermark
Virtual memory used: 15% (631 MB out of 4014 MB) - below watermark
Used: 87 MB by FW, 544 MB by zeco
Concurrent Connections: 1% (280 out of 16900) - below watermark
Aggressive Aging is not active
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Kaspars, hope you are fine, sorry , may i ask why aggressive aging should not be active?. from what i understand this helps to finish or close idle connections and with this free some resources from the connection table.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Edson, aggressive aging gets activated only when connection table is getting full thus "cleaning" up idle connections much quicker than normally. This is to allow you to process new connections when you are near capacity. Technically it sounds a "good and helpful" feature (and it is mostly!) but I have to admit we have seen some strange behaviour when AA was active - some RDP connections over SSL did not work for example. I would say - if you see AA active, act on it, fix it, it's not a "normal" state ![]() more like a workaround till you free up memory/tables
more like a workaround till you free up memory/tables
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you guys but I still don't feel that I got answer to my questions.
Huseyin, I don't want to set a limit but instead keep it automatically. Kaspars, it's 64 bit gateway. I have 0 failed allocations on system memory and on kernel memory. I just want to know what is the limit actually when set to automatically if possible to know. Like my example with peak at 21394 concurrent connections, what does that tell me? Was that close to maximum what the firewall could handle before starting to drop new connections? I mean I don't know the treshold and when to start to worry without waiting for the next storm and run fw ctl zdebug drop command.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can't be that you were anywhere near the limit with this small number. Even with 3GB RAM you can handle nearly 300k connections (no advanced blades though)
Considering that you have 16GB and 64bit OS you shutsh be able to handle heaps more concurrent connections.
What did fw ctl pstat showed?
Worth noting that delayed connections won't appear in connections table
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Like my example with peak at 21394 concurrent connections, what does that tell me? Was that close to maximum what the firewall could handle before starting to drop new connections? I mean I don't know the treshold and when to start to worry without waiting for the next storm and run fw ctl zdebug drop command
Ok so you are asking actually how many connections can your firewall handle? For example if you set the limit automatically, when will the firewall reach the maximum connection limit ? Like Kaspars Zibarts said, with these resources, can't be that you were anywhere near the limit with this small number.
Maybe the appliance datasheet can help, there is statistics about conn under performance section. Perhaps you can make an inference from these datas.
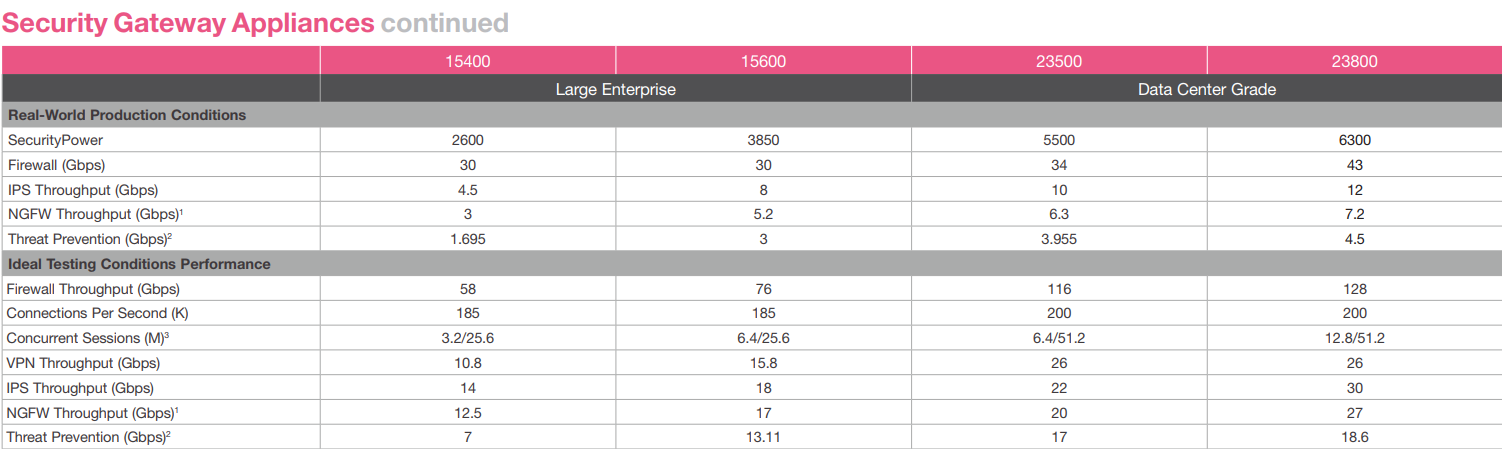
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Exactly, since it's set to automatic I would like to know the maximum concurrent connections limit the firewall can handle before starting to drop connections. It's an open server so I can not relate to some numbers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can always guestimate based on current state of fw ctl pstat
for example
System Capacity Summary:
Memory used: 9% (1175 MB out of 11845 MB) - below watermark
Concurrent Connections: 24946 (Unlimited)
Aggressive Aging is enabled, not active
You could easily rough estimate that we could run 10 times as many connections on this firewall (at current usage of 9%), so 10 x 25k = 250000
It's very hard to put exact number as it depends on blades that are enabled and NAT usage
A simple FW connection will only consume ~10kB whereas in example above you can see that each connection was ~40kB that's because IA, IPS and AB is enabled on that gateway
![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you. I find this interesting:

Around the same memory usage in percent but very different numbers in connections. So based on a rough calculation
10 x 7k = 70 000. Several blades are enabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The actual amount of memory a connection takes up depends on the blades in use.
We used to have a public SK that explained memory usage, but I think it's internal only now.
IPv6 uses more memory also ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Indeed! I was trying to find that SK but failed miserably
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 13 | |
| 9 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


