The best you can do here is limit the amount of bandwidth/connections the auditors consume in the firewall via the fw samp command which requires SecureXL to be enabled. Here is a excerpt from my book covering this exact situation:
Your new internal auditor, Jim Profit, has discovered the wonders of the nmap and
Nessus attack tools, and is thoroughly enjoying blasting your underpowered firewall with
ridiculous amounts of port scan traffic aimed at your organization’s various DMZ
networks. Jim’s internal workstation has a static IP address of 192.168.48.96 and is
targeting various destination DMZ networks that can be summarized as 172.17.8.0/22.
You want to let Jim do his job (as no one ever wants an auditor upset with them), but you
need to ensure acceptable firewall performance for everyone else. You decide to limit
Jim’s workstation to 100 new connection requests per second. The command to do this
would be:
fw samp add -a d -l r -n Limit_Jim_Profit_PortScanning quota \
source cidr:192.168.48.96/32 destination cidr:172.17.8.0/22 service any \
new-conn-rate 100 flush true
(Note: the ‘\’ character at the end of lines 1 & 2 of this command is a backslash
and allows us to continue the same command on a new line)
Key arguments for our sample fw samp add command:
-a d (action drop)
-l r (regular logging)
-n Limit_Jim_Profit_PortScanning (name of rule)
new-conn-rate 100 (limit new connection rate to 100/sec)
flush true (make this new Rate Limiting rule take effect immediately)
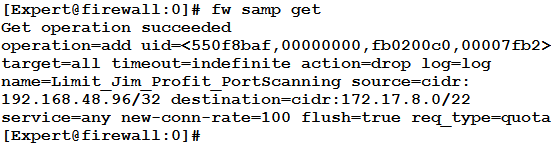
We can check the status of our rules with the command fw samp get:
We can check the status of enforcement with cat /proc/ppk/dos:
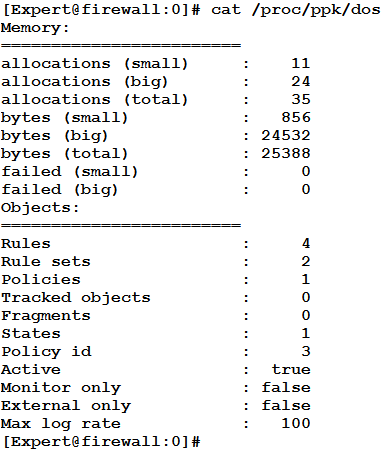
But we have done all this, and Jim is still laughing gleefully as he pummels our
firewall with well over 100 connection requests per second! Why isn’t our new quota
working? Remember these quotas were originally designed to blunt the effects of DoS
attacks, which tend to arrive most often on the external interface(s) of the firewall. By
default these quotas will only be enforced on the firewall’s external interfaces. To
enforce our quota on all firewall interfaces (and abruptly halt Jim’s grating laughter), run
the sim_dos ctl -x 0 command.




