- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- How to block some https sites?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to block some https sites?
I have a rule in Checkpoint, in Policy tab:
Source: host (one pc with IP)
Destination: Internet
Services & Applications: denied_sites
Action: drop
denied_sites: custom site, which contains some urls.
I wrote both http://www.example.com, https://www.example.com
After installation policy, rule drops only http, but not https.
How can I make that rule worked for https too? (Without turning on https inspection)
I looked previous questions, but I didn't manage to find solution.
Labels
- Labels:
-
Policy Installation
-
SmartConsole
- Tags:
- url-filter
29 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Copy&paste from help:
In the URL List, enter the URLs.
- Do not include http/https prefixes
- The URL list supports the use of wild cards, for example to define the sub domains and paths of a top level domain. (*.checkpoint.com/*)
- Select URLS are defined as Regular Expression to define more complex domain patterns, or for greater specificity.
For example, if a news site has these links:
To allow access only to the https link, use this regular expression:
^https:\/\/.*\.news\.com
Note: The application or site URL defined by a regular expression must use the correct syntax.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In url list, if I write *.example.com/* it gives error:
URL cannot contain the following substring: /*
Then I wrote *.example.com and it blocks only http, not https.
It cannot block https sites.
What else can be done?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Add this:
(^|.*\.)*example\.com
and make sure "URLs are defined as Regular Expression" is ticked.
But if the site is using SNI then you better follow SK mentioned bellow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have tried adding this and ticked as "Regular Expression".
I added some sites, not one.
https is not blocked still.
Simple Proxies may block https, why it is so difficult in Checkpoint?
Can Checkpoint block https?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In addition to what Hristo Grigorov said, you need to confirm what the DN of the certificate of the site you want to block is as that is what is matched.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you mean that I should include full domain name of the certificate in URL list?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Whatever it says in the DN of the certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to see DN of the certificate? I could not find
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is certificate DN:
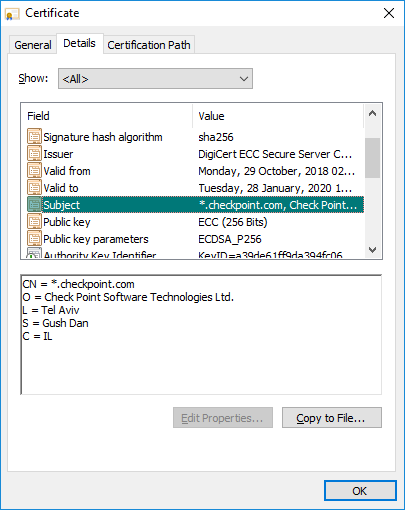
This is certificate w/o SNI:
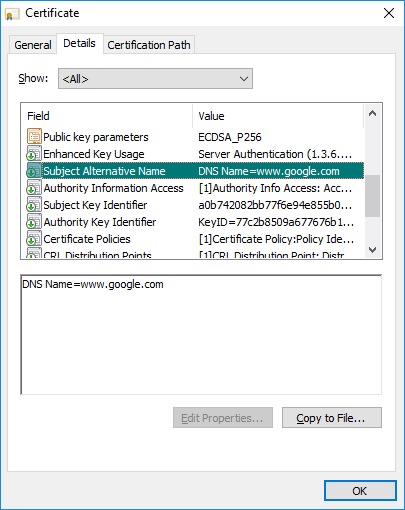
This is certificate with SNI:

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How can I block https://z1.fm site for example?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
^https:\/\/z1\.fm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have checked, it does not block. Any other solution?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am sorry mate, no idea what is wrong. It works for me here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you anyway mate! Then I have to write to tech.support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The CN of the certificate for z1.fm is sni.cloudflaressl.com, as shown below:

This means you cannot currently use the URL z1.fm to block, as we will see sni.cloudflatessl.com, at least in the manner described.
Right now, you can do one of two things:
- Enable HTTPS Inspection
- Create a signature for this site using the Application Control Signature Tool: Signature Tool for custom Application Control and URL Filtering applications
In general, we do plan to improve our support for SNI in the near future.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, can we block that site by its IP addresses then?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can, but it's possible you will also block some legitimate sites in the process (not to mention the IP could change, being behind CloudFlare).
Is there some reason you can't use the Application Control Signature Tool to create a signature for the site?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The reason is that I don't know how to use Application Control Signature Tool.
Is it possible to create custom signature for any site?
I would appreciate if you share one example how to create custom signature step by step.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's a pretty straightforward Windows app with documentation that can help you.
This is what I created specifically for the site you mentioned:
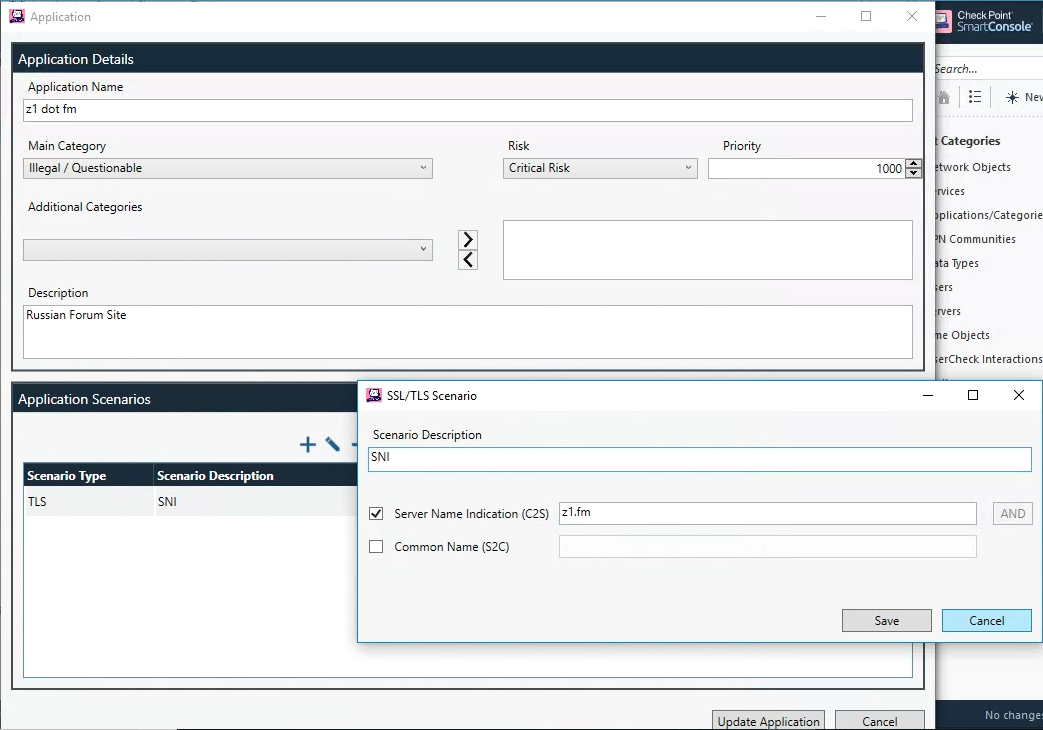
Import the app into R80.x Management:

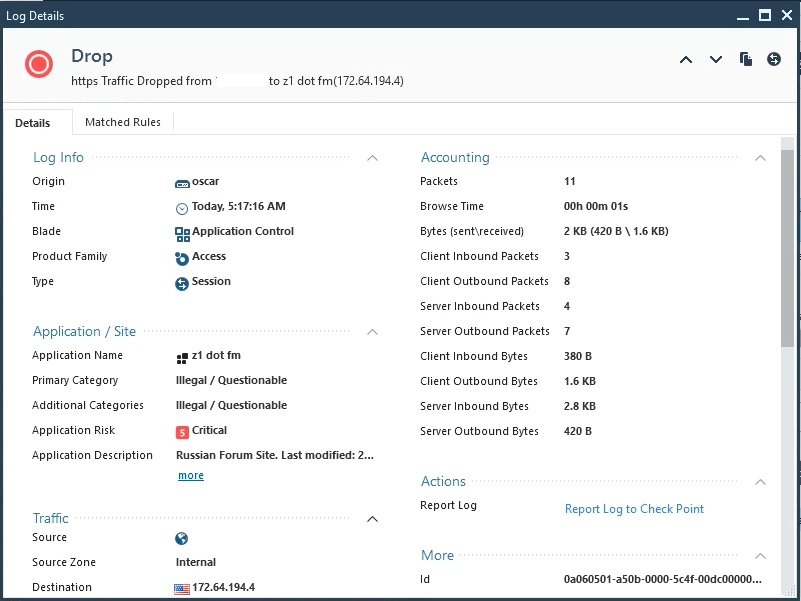
Create a rule based on the signature and push policy:

And, sure enough, it works.
No HTTPS Inspection required.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Very cool. Where can I download that Windows app?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is linked in my previous comments.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can this exported Application also be used with R77.30?
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The tool produces R77.x and R80.x versions of the application definition.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I could not find link to that app. Would you provide please?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey PhoneBoy,
Maybe you could help me out, not sure if I am missing a step, We have https inspection enabled, though in bypass mode, have sites that are not being blocked on https, but are blocked for http. I created an app with the signature tool, imported it, (R77.30), I see it in the applications/sites, but in the policy it does not show up. I have installed database and pushed policy, but it still doesn't populate in the policy for an app to added to a rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Custom URL filtering by SNI
sk103051
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What we experienced is that putting more than 1 line in the urls field will break the https recognition abilities.
Try to change the custom application to only one url like example\.com as a regular expression and check to see if https categorization is turned on when you do not have https inspection enabled.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is HTTPS inspection enabled? If not, is the first checkbox for categorization of HTTPS websites checked within the engine settings?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 15 | |
| 9 | |
| 8 | |
| 6 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


