- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: How do Threat Prevention Layers work?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How do Threat Prevention Layers work?
Tomer,
Can you expand on the use of Threat Prevention layers?
I am having difficulty envisioning how those relate to the overall policy and its layers.
I.e. Adding layer to Threat Prevention seem to create additional policy:
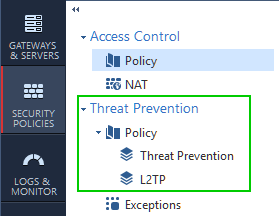
That is not tied to the layers in the main policy.
Would those TP policies be then processed sequentially?
What is the point of those layers if the only differentiation in each is the Scope and Profile?
How is the TP layers differ from multiple rules in the same TP policy?
Thank you,
Vladimir
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Threat Prevention Layers enforcement is calculated by the following:
- Each layer has a first-match logic. Once a match is found, processing is done at the other layers.
- Unlike Access Control, there is no requirement for clean-up rule. So if there is no match on a layer, assumption is that no threat prevention inspection is needed.
- In case there are multiple threat prevention layers, and a match was found in several layers, the strictest option matters. So if you chose to prevent a protection for a subnet in the first layer but detect that protection in another layer, it will be in prevent.
The motivation was to add extra layers of protection, if needed. Separation can happen per blade (like the IPS Shared Layer which appears post-upgrade and is the way things worked in previous versions) or per network (for the sake of policy clarity and in later versions, role segregation).
At Check Point we believe that Access Control and Threat Prevention are separate things. Access Control is typically a more massive operation, with sometimes hundreds of rules and more, while generally for Threat Prevention you probably don't define that many rules, and entire scopes go with a profile. Adding a new Access Control Rule does not violate a threat prevention profile. Installing policy changes is done separately for Access Control and Threat Prevention because we believe those are different types of owners in the organization and they don't have to affect one another.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tomer,
I'm still a bit baffled by it, should you have an opportunity to showcase few sample policies with layers, it will go a long way clarifying the issue.
As far as I can tell, there is no ability to limit individual admin's rights over single or select Threat Prevention layers:

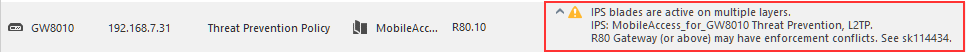
Further more, when multiple Threat Prevention layers are used, I am seeing a warning about possible conflict in IPS:
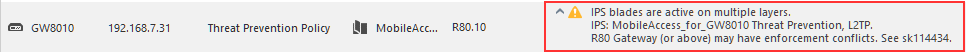
I'll read the SK later to see what is it all about.
As to the sequential processing with segregated controls, multiple rules in the same policy seem to be able to address it:
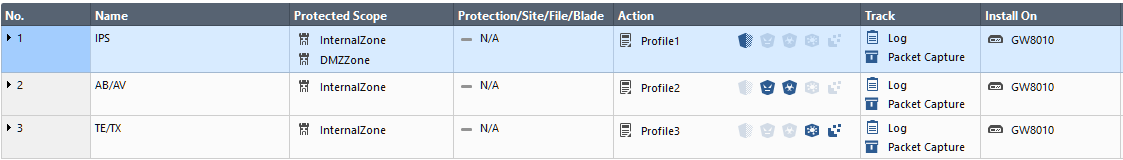
But I really do not see much merit in separating blades in rules if they cover same scope, as shown in rules 2 and 3.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
As far as I can tell, there is no ability to limit individual admin's rights over single or select Threat Prevention layers:
This is actually coming in the next release of Security Management Server, not this one.
Further more, when multiple Threat Prevention layers are used, I am seeing a warning about possible conflict in IPS:
I'll read the SK later to see what is it all about.
Personally I think we may have used the wrong UI indication to tell our users that the policy works as they designed it. It means that the stricter option matters. It's not really a warning, it's more like a reminder of how the policy will behave.
So we can talk about 2 examples:
1. Each layer controls a software blade. This pattern already happens for users who upgraded their Management but not their gateways - the IPS Shared Layer is separated from the rest of the Threat Prevention products, which are in a second layer. So the upgraded policy scenario is a private case of this pattern. Users can go further and separate the signature-based decisions and profiles with the dynamic-based decisions and profiles by placing them in multiple layers.
2. Each layer controls a different network, and has multiple profiles for different portions of a network (so multiple rules per layer).
Why split to layers and not just have one big rule-base? It's up to each administrator to decide, generally:
1. Smaller building blocks help understand the policy better
2. Features that are coming in the next release: Sharing the same layer across multiple policies, and assigning different permission profiles to edit different layers - similar to the way Access Control layers are defined.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you!
This does makes more sense when new features are implemented in the : "coming in the next release: Sharing the same layer across multiple policies, and assigning different permission profiles to edit different layers - similar to the way Access Control layers are defined."
Will the layers applied to the same policy be visible in one contiguous view, same as inline layers?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think that the need for "one contiguous view" is not due to threat prevention execution similar to inline access layers or not (it's not similar to inline layers...) but rather because it makes sense to see all the rules in one contiguous view (and then it also makes sense to do that for ordered layers at Access Control). At the moment we don't have concrete plans for this but we will take your feedback into consideration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yep, that's exactly it: "rather because it makes sense to see all the rules in one contiguous view".
It is just had to made very clear that this is the presentation only, not the actual sequence of execution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Tomer_Sole: Could you maybe clarify again the behavior, if I got multiple rules on one layer, with same scope and different threat profiles, like in the screenshot provided by @Vladimir :
Will Threat-Emulation in Rule 3 be enforced, or is rule 2 shadowing rule 3, so that only AV and AB is enforced for internal-zone?
So in one layer - is it a first-match and out or first-match per protection?
Thanks
Johannes
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The combination of all the enabled engines will apply.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay, so for clarification:
(Same Scope)
Rule 1: av-only
Rule 2: ab-only
Rule 3: TE-only
Rule 4: av, ab and TE
With this setup is garanteed, that up to and including Rule 3, Blades AB, AV and TE are enforced, but Rule 4 is shadowed by Rule 1-3 and will never match, right?
(Same Scope)
Rule 1: av-only
Rule 2: ab-only
Rule 3: TE-only
Rule 4: av, ab and TE
With this setup is garanteed, that up to and including Rule 3, Blades AB, AV and TE are enforced, but Rule 4 is shadowed by Rule 1-3 and will never match, right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No.
If these rules belong to the same layer, the first matched rule, #1, will apply, and that's it.
However if you split each rule to its own layer, AV, AB and TE will apply with the strictest prevention set.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tomer:
In case there are multiple threat prevention layers, and a match was found in several layers. Aside these layers both prevent one protection.
How about the matching in this situation?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Chen,
Not sure I understood the question accurately, but the answer to your question is that both layers will be matched, and the protection will be prevented. Is that what you asked?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 16 | |
| 13 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter