In R80.10 the rule base is represented as a database table in the kernel which automatically adapts to changes in dynamic objects and results in a more efficient policy installation process.
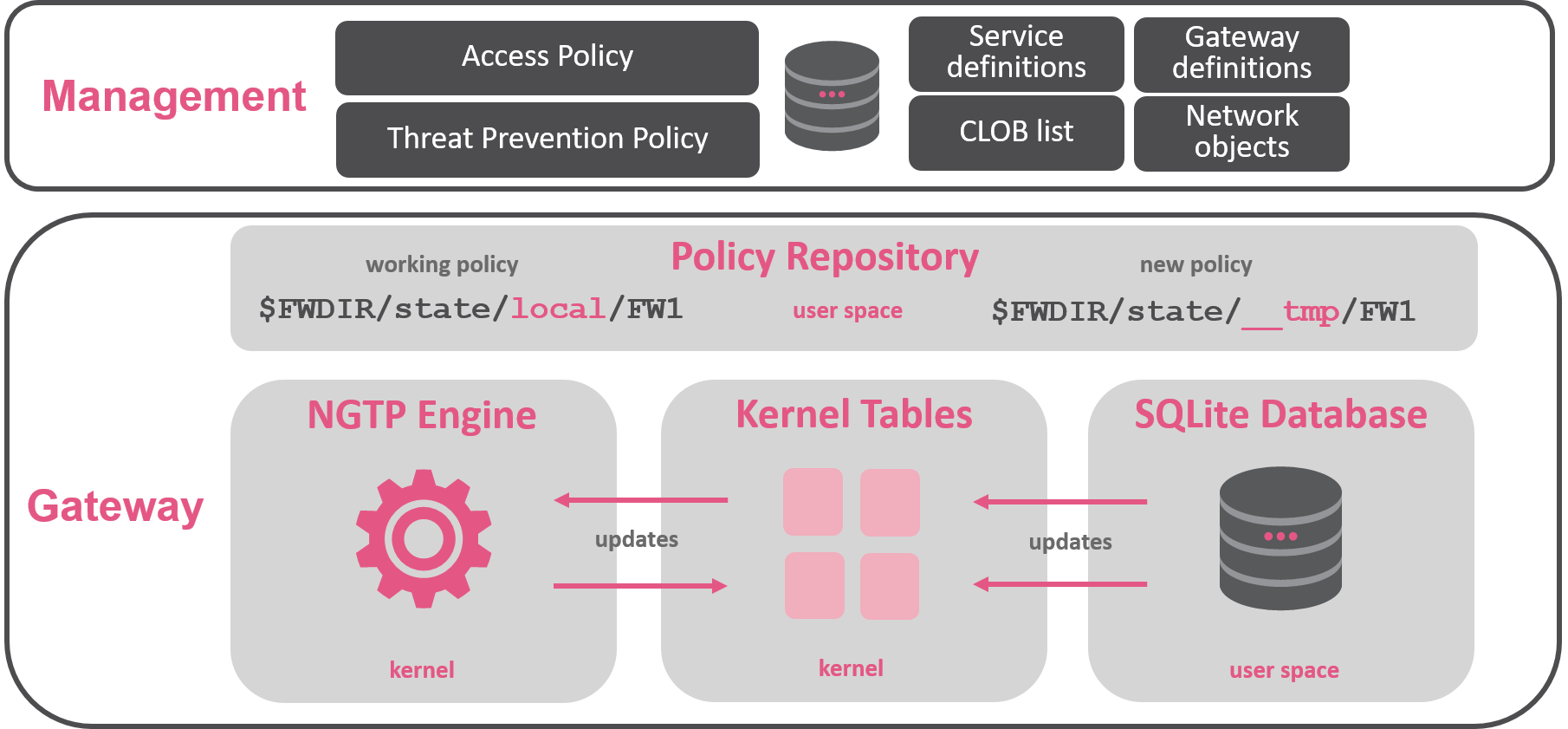
The policy installation process on R80.10 gateways consumes less time and resources than on R77 gateways. Instead of a compilation process the management server does a database scheme conversion. Each gateway receives only the objects required for the local rule base.
On the gateway a separate preparation and commit phase provides recovery and fallback if needed. The current policy is stored in the $FWDIR/state/local/FW1 directory. During the policy installation files containing the information about the new policy are transferred from the management server to the gateway and stored in the. $FWDIR/state/__tmp/FW1 directory. The next step is to create and/or update the table structure in the SQLite database. If a failure or reboot occurs at this point, then the gateway continues to run the current policy. During the final commit stage, the pointers in kernel memory are changed to point to the new policy and objects. The gateway continues to run the current policy until the new table pointers are loaded.
In addition to supporting fallback and recovery the new structure automatically adapts to changes in dynamic objects and adds SecureXL support for Dynamic, Domain and Time objects. In R77 these objects would disable SecureXL accept templates at that point in the policy.
# fwaccel stat
Accelerator Status : on
Accept Templates : disabled by Firewall
disabled from rule #<N>
In R80.10 security enforcement is done based upon the kernel table arrays and the policy stored in the kernel memory. As network and dynamic objects change in the SQLite database the kernel tables are updated. When the objects change the SecureXL template is revoked and then SecureXL goes through the process of recreating the connection providing acceleration template support for these dynamic objects in the R80.10 policy.
In addition to the above, the infrastructure still supports legacy commands such as “fw unloadlocal” and “fw fetch localhost” and enables future enhancements such as partial policy installs, i.e. installing a policy layer or sublayer.



