- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Disable "Local interface address spoofing"
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Disable "Local interface address spoofing"
Hello,
we have a setup, where all the traffic is mirrored to the Checkpoint 5800 (via SPAN port).
Management and mirrored traffic interfaces both have "Anti Spoofing: Disabled",
however, since CP receives mirror of all the traffic (including one from its management interface), logs are filled with
message_info:"Local interface address spoofing" messages
(the MAC address of the mirrored packet is that of the router, not CP device).
How can we disable check for "Local interface address spoofing"?
Running R80.20.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
fw ctl set int fw_local_interface_anti_spoofing 0
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
18 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In SmartLog, just enter. not spoofing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Wouldn't that only filter output in the view?
We are using cp_log_export, to export logs via syslog, and these are flooded with
---
2018-11-07T11:49:58+02:00 local0.info 11.11.11.11 1: 2018-11-07T09:49:54Z ids-n2 CheckPoint 29740 - [action:"Drop"; alert:"alert"; flags:"401408"; ifdir:"inbound"; ifname:"eth1-01"; loguid:"{0x0,0x0,0x0,0x0}"; origin:"11.11.11.11"; originsicname:"cn=cp_mgmt,o=ids-n2.xx.xx.fpp84p"; sequencenum:"530"; time:"1541584194"; version:"5"; __policy_id_tag:"product=VPN-1 & FireWall-1[db_tag={637D2E66-C60F-4646-BD66-FDB8148F5F42};mgmt=ids-n2;date=1541582377;policy_name=Standard\]"; dst:"23.60.24.21"; message_info:"Local interface address spoofing"; product:"VPN-1 & FireWall-1"; proto:"6"; s_port:"38149"; service:"80"; src:"11.11.11.11"; ]
...
---
messages
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
fw ctl set int fw_local_interface_anti_spoofing 0
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Operation succeded, but messages "Local interface address spoofing" still pour to the fw.log.
# fw ctl set int fw_local_interface_anti_spoofing 0
Set operation succeeded
# fw ctl get int fw_local_interface_anti_spoofing
fw_local_interface_anti_spoofing = 0
# sim feature anti_spoofing off; fwaccel off; fwaccel on
Command 'sim feature' has been replaced. Use 'fwaccel feature' instead.
SecureXL device disabled.
# fwaccel feature anti_spoofing off
Invalid feature 'anti_spoofing'
Usage: fwaccel feature <name> {on|off|get}
Available features: sctp
I've also set:
# fw ctl set int fw_antispoofing_enabled = 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
After checkpoint reboot the issue is solved: there is no longer spoofing messages in the logs.
Thank You
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Timothy !
Thanks for the answer! I 'm wondering if there will be a negative impact after entering this command on the gateway ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It won't affect production, it will just keep traffic that the gateway thinks is spoofing its own address from getting dropped. Generally though if you are getting these messages it indicates a network misconfiguration of some kind such as another system in conflict with the firewall's interface IP address, or traffic that was NATted to the firewall's interface address getting incorrectly bounced back to the same firewall interface due to an upstream routing problem.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks !
in our scheme, anti-spoofing is in the Net_10.0.0.0(Internal) mode on the Inside interface (anti-spoofing is detect mode) . However, there is a need to connect the office of a partner who uses 10.109.0.0 networks area. With successful initialization IPsec tunnel, we have drop log "Local interface address spoofing". I'm assuming to change the topology for the Inside interface Net_10.0.0.0(Internal) ----> Specific, and to make a set of networks more granular than Net_10.0.0.0(Internal). I hope this helps to win )
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
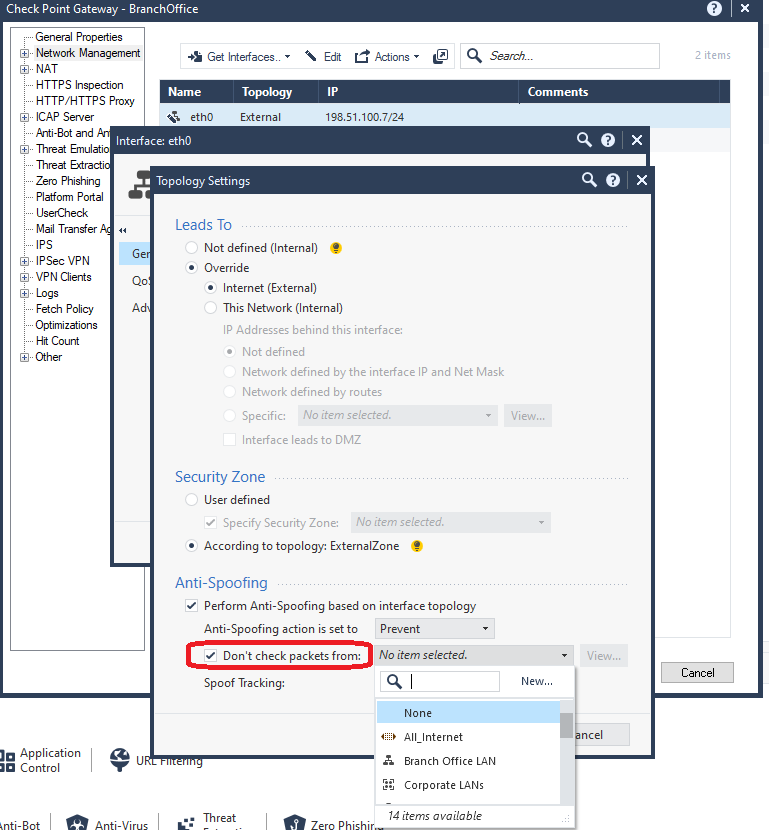
A cleaner way to handle this is adding 10.109.0.0 as a "don't check packets from" exception on the External interface here:
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes, of course, this was done first, the network 10.109.0.0 is excluded on the External interface. But it didn't help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes, of course, this was done first, the network 10.109.118.0/24 is excluded on the External interface. But it didn't help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
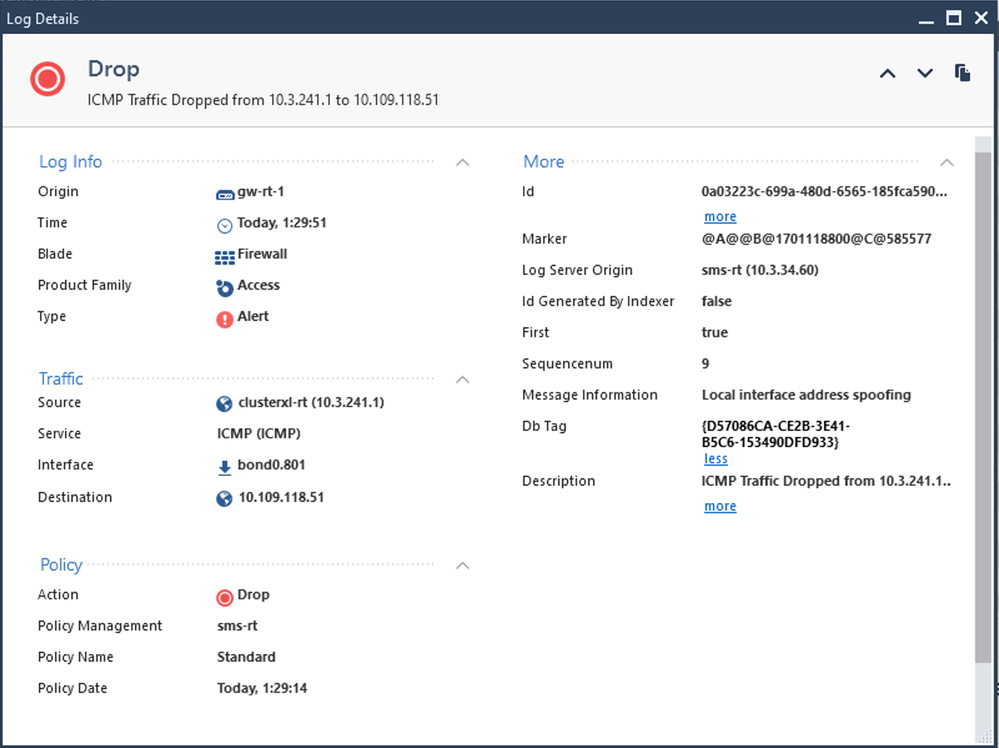
It is the source IP address 10.3.241.1 that is violating anti-spoofing in that log card, not the destination 10.109.118.51. You have one of two situations occurring:
1) Most likely a routing problem. Traffic was initiated from somewhere bound for 10.109.118.51, it arrived at the firewall who then source NATted it to 10.3.241.1 and sent it out egress interface bond0.801. Some router on the path towards 10.109.118.51 improperly bounced the packet back to the firewall inbound on interface bond0.801 where it was dropped by spoofing.
2) IP address 10.3.241.1 is being used by some other host (either on the other side of the VPN or locally) and it conflicts with the firewall's interface IP.
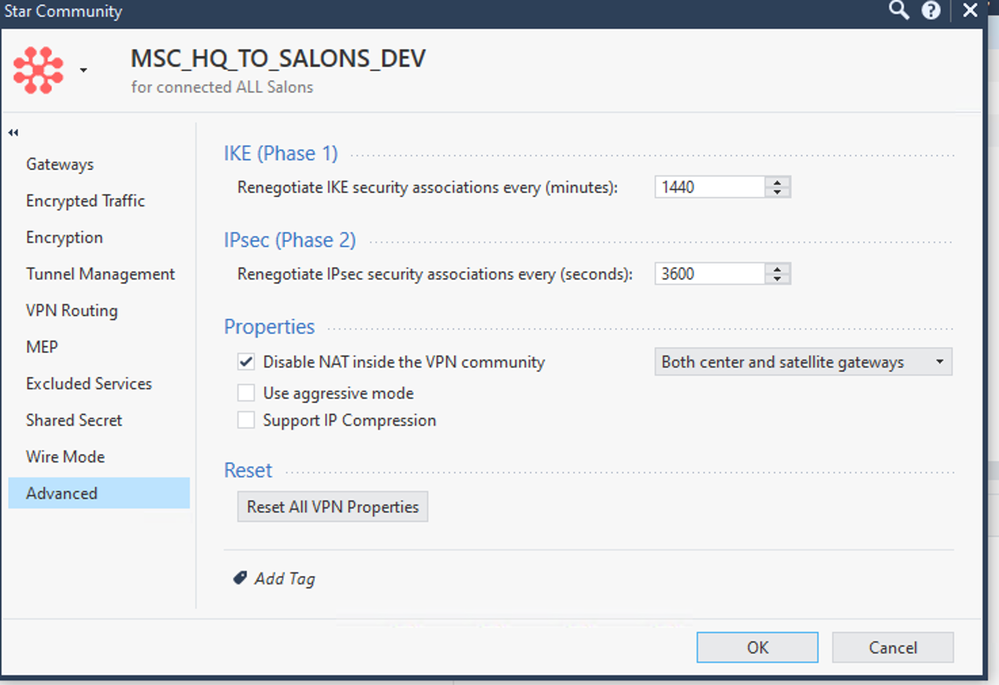
Either way, turning off local interface spoofing enforcement will not help as the routing for either of these situations is incorrect. If this is VPN traffic, checking "Disable NAT in VPN Community" for the relevant VPN Community might fix the problem, if it is caused by the firewall inappropriately NATting the traffic thus causing situation #1.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does the fact that 10.109.118.0/24 is behind the SmartLSM gateway matter? and I check VPNcomm settings, yes NAT is disabled for those VPN communities
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
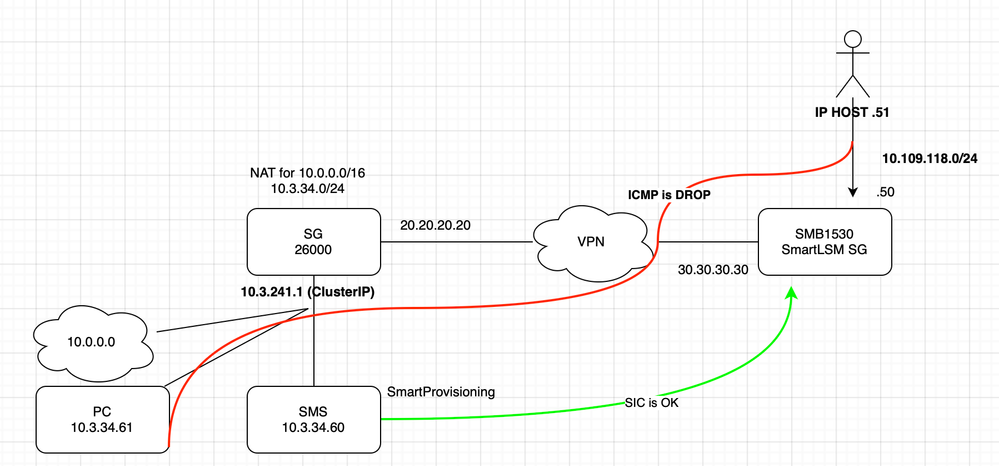
Need a network diagram please.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
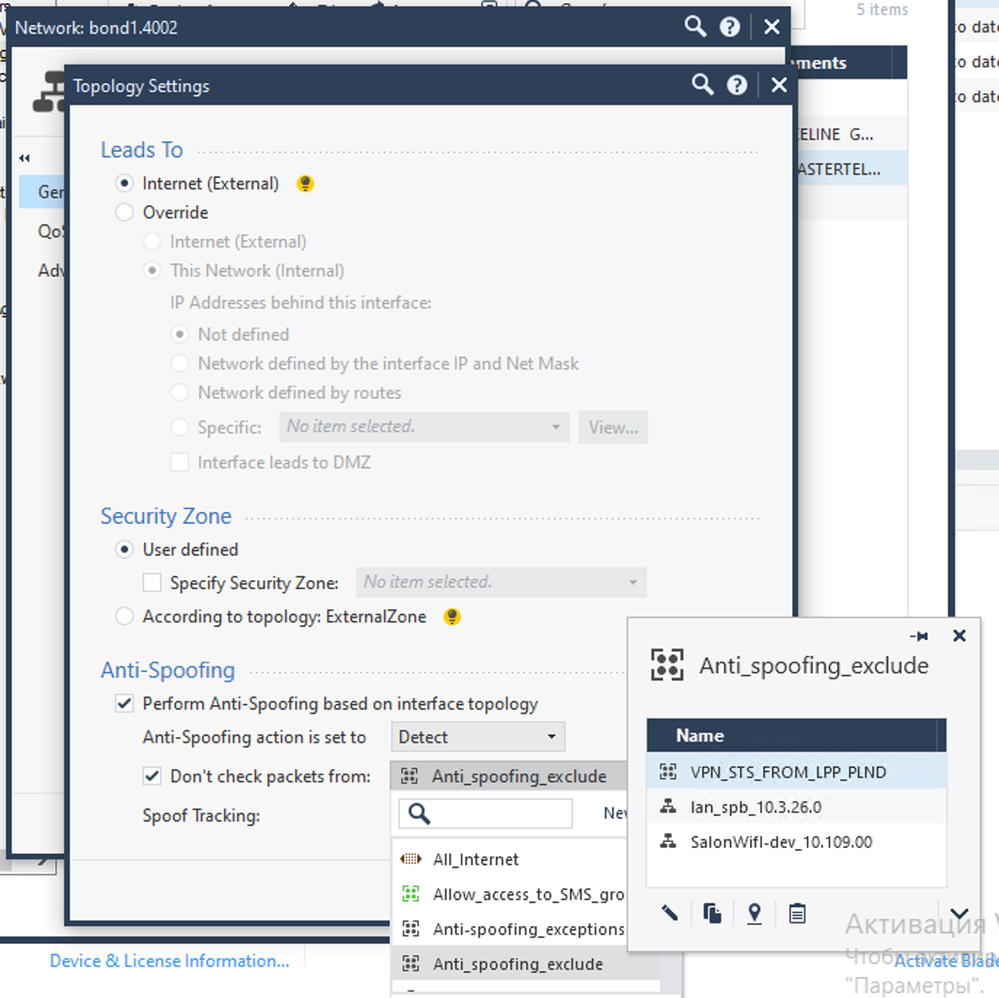
In general, the diagram illustrates the current VPN connection. We have a cluster 10.3.24.1 (in HQ) behind it the area 10.0.0.0. SmartLSM SG in the branch, is successfully connected to this cluster, there is a network 10.109.118.0 behind the SmartLSM internal interface. ICMP or another service does not pass from the network 10.3.34.0/24 to the network 10.109.118.0/24. "Local interface address spoofing error" Have one VPN community Star mode, members of this community с26000 and SmartLSM SG.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You almost certainly have a supernetted route for 10.0.0.0 (probably /16 but could be /8) on your HQ firewall pointing to your internal core router. You need a firewall static route for 10.109.118.0/24 with the next hop your Internet perimeter router. Because you don't have this, the traffic to 10.109.118.0 is being NATed by the firewall then hairpinned right back to your internal core router, who promptly bounces it right back to the firewall which then drops it for spoofing. Like I said, a routing issue.
You also need to ensure that the 10.109.118.0 network is not part of the VPN domain definition for the HQ firewall, a "group with exclusion" object is typically used for this purpose. Obviously 10.109.118.0 must appear in the VPN domain for the remote firewall.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are absolutely right! Our routing was implemented poorly. Our network engineers fixed the situation and the problem with Local Spoofing was solved. Thanks again for the help!
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 16 | |
| 6 | |
| 5 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter