- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Quantum SD-WAN Monitoring
Register HereCheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
MVP 2026: Submissions
Are Now Open!
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Difference between HTTPS Inspection and Catego...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Difference between HTTPS Inspection and Categorize HTTPS websites settings
Hi Checkmates,
I would like to ask what is the difference in the behavior, pros and cons of or when will you use the following:
1. HTTPS Inspection
2. In Application & Url Filtering Settings under Url Filtering -> Categorize HTTPS websites.
because in the " Categorize HTTPS websites" settings it says that you can allow HTTPS (SSL traffic) URL's without activating HTTPS Inspection.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
At the time I wrote the previous answer and for older (R77.x) releases, these options were mutually exclusive.
In current (R80.20 and above with appropriate JHF) versions, this is not the case and Categorize HTTPS Sites is enabled by default.
I am hard-pressed to come up with a situation where you'd want this disabled, regardless of whether or not HTTPS Inspection is used.
29 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HTTPS Inspection allows you to see all the traffic as if it was unencrypted, allowing you to do full threat prevention and content inspection.
Unfortunately, there are some situations where HTTPS Inspection does not work, namely:
- Certificate pinning
- Client certificate authentication
- Different ciphers used for TLS than are supported in HTTPS Inspection
- Where TLS 1.3 is required
Categorize HTTPS Sites will allow you to categorize HTTPS connections based on the certificate DN, which is sent in the clear.
It, however, does not currently support SNI, which many sites use, particularly anything with a wildcard certificate.
You also cannot see the full URI or any of the content (as we are not decrypting it), allowing for limited threat prevention capabilities.
There are several threads that discuss both of these topics in more detail.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank You sir Dameon for the reply.
Do you mean that if i will do HTTPS inspection i need both HTTPS inspection rules and check the "Categorize HTTPS websites" in url settings?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you can do HTTPS Inspection, you don't need Categorize HTTPS sites.
The options are mutually exclusive.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you have https inspections turned on HOWEVER you aren't doing outbound inspection, only inbound; can/should you still leave Categorize HTTPS websites checked?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
At the time I wrote the previous answer and for older (R77.x) releases, these options were mutually exclusive.
In current (R80.20 and above with appropriate JHF) versions, this is not the case and Categorize HTTPS Sites is enabled by default.
I am hard-pressed to come up with a situation where you'd want this disabled, regardless of whether or not HTTPS Inspection is used.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dameon,
Would any of these limitations be addressed in R80.20?
Doe the use of acceleration card help to address any of these limitations?
If the answers to above questions are "No", is there an ARTG on the use of the external SSL/TLS decryption solutions with Check Point that are known to work well and to remove these limitations (i.e. Gigamon, SSL Visibility Appliance | Symantec , Ixia or F5)?
Thank you,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is a coming hotfix on top of R80.10 (and presumably included in R80.20) that is expected addresses the issues with SNI.
For HTTPS Inspection in R80.20, there a couple things:
- Improved cipher support
- Support of outbound HTTPS Inspection with a Gemalto SafeNet HSM Appliance
- Support for use of both HTTPS Inspection and Categorize HTTPS Websites concurrently (at the moment, they do not work together).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
TLS 1.3?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are definitely looking at how to address TLS 1.3, though not listed in the EA notes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dameon,
Can you validate if the issues are effectively solved on R80.20?
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SNI support is not included in R80.20, but we are planning to bring the hotfix to this release also.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello phoneboy, quick question, 80.20SP, is categorization working with SNI in current hotfix? or it does not work for whole 80.20 code? thx! for reply
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SNI support is specifically called out in the R80.20 JHF SK.
A similar call out does not appear in the R80.20SP JHF SK.
A similar call out does not appear in the R80.20SP JHF SK.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Here I want to share my recent experience.
We have enabled & configured URL Filtering blade on the firewall. After checking logs, came to know that only http traffic is categorized. For https traffic, categorization is not happening and result is not as per the configuration.
We don't want to enable https inspection. So finally we have enabled "Categorized https Websites" and it started working as expected.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Interesting. So if you block the category gambling, for example, and then go to a https gambling website ( i.e. https://ladbrokes.com ) does the usercheck screen display correctly ? I find that unless https inspection is on, this will not show the block/user check pages ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Paul,
Yes it is working correctly without https inspection ON.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Paul,
For me, visiting the website (HTTPS CATEGORIZATION IS ENABLED) did not show the user check / block message but after enabling SSL Inspection the block message appeared.
This behavior is tested on a SMB Appliance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Pretty sure this is expected behavior on all versions.
It's certainly my experience on R77.20/R77.30.
Gaurav Pandya what version did this work for you?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is R77.30
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, not with SMB 1450. I had to open a TAC Case for this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Paul
Indeed , User Check Block web page will not function well when Https Inspection is off.
When we try to key-in the URL in "ladbrokes.com" is different from "https://ladbrokes.com" to User Check Block Page function.
"ladbrokes.com" will display User Check Block Page correctly.
Because it is http redirect.
"https://ladbrokes.com" will not display User Check Block Page correctly.
Because it is https redirect. So need to enable Https Inspection function.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Rick & others
Thanks for the advice. It does seem that the 'categorise https sites' option is pretty useless then without https inspection.
I do wonder how Forcepoint (ex Websense) and other dedicated filtering companies manage to filter and show block pages without having ssl decrypt enabled.
Does it make any difference if we configure the Checkpoint gateway as a web proxy ? Does it work then ?
If this is fixed in a hotfix or R80.20 then that will be very welcome news
Cheers
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Paul
I ever talk with my colleague.
He is familiar with both CheckPoint and WebSense(ForcePoint).
WebSense also need to enable https inspection function to be able to show https block page correctly. (Even work in proxy mode)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Rick
I have Websense showing the block page for https websites without SSL decrypt enabled. Be interested in your colleague's findings
Thanks
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Another disadvantage of categorization vs. inspection is the fact that categorization wouldn't be able to differentiate between two services that run under the same hostname, e.g. dropbox and wetransfer uploads could not be differentiated from downloads as the only part that's visible to the CP is the hostname, not the full URL.
As the hostname is identical for both the upload and the download, the CP could not tell it apart.
To confirm, using any of the following would either block or allow WeTransfer as a whole, not just e.g. up- or download when using categorization only instead of inspection.
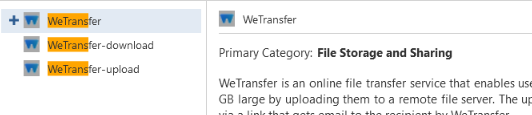
In this respect you'd need to at least enable inspection for the sites you're interested in differentiating (e.g. into up- and download) for logging or controlling purposes while bypassing all others.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Sorry for the micro NecroBump, but I think it's a good spot to ask this question :
Is Full HTTPS Inspection ca be enabled on some firewall, and HTTPS categorization enabled on other firewall ?
If I activate "Categorize HTTPS websites" in the "Advanced Setting" of "Application Control & URL Filtering" blade, what will happen to Firewalls with Full HTTPS Inspection activated ?
We have a mixed collection of CPs, and I want to some categorization on SMB Appliances without disabling HTTPS inspection on our main Gateway.
I hope it is possible.
Bests Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Per above are the main Gateways R80.20 or another version?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If the gateways are R80.20 and above, you can run both at the same time.
Gateways that are R80.10 and earlier cannot run both options at the same time and HTTPS Inspection will take precedence.
Gateways that are R80.10 and earlier cannot run both options at the same time and HTTPS Inspection will take precedence.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the reply,
Main Gateway is R80.10 version.
So, in my scenario, if I check the option "categorize https websites":
- If full inspection HTTPS is activated on my R80.10 CP, it will remain active, and categorization is not active.
- On my SMB 14xx, if I disable completely full Inspection HTTPS, "categorize https websites" will be activated ?
I Hope this is the correct behavior.
Thanks again.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 17 | |
| 9 | |
| 6 | |
| 5 | |
| 3 | |
| 3 | |
| 3 | |
| 2 | |
| 2 |
Upcoming Events
Thu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


