Oren,
Thank you for explaining why I am missing out some very important incident if I filter out "SSL Enforcement Violations" and "Web Server Enforcement Violations". I get the point, and I will adjust my view to get a better understanding.
I am also afraid of filtering too much out which could be important.
I will try out your suggestions.
I really liked your presentation on getting the numbers right. And I see first IPS logs, Anti-bot and Anti-virus logs that one needs to look into to get a better understanding.
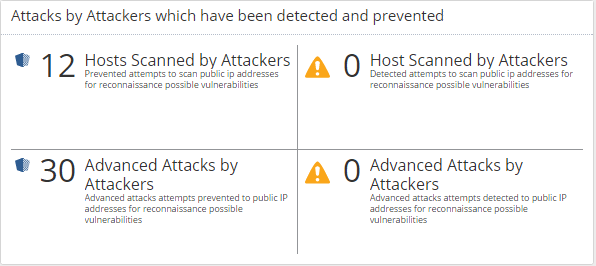
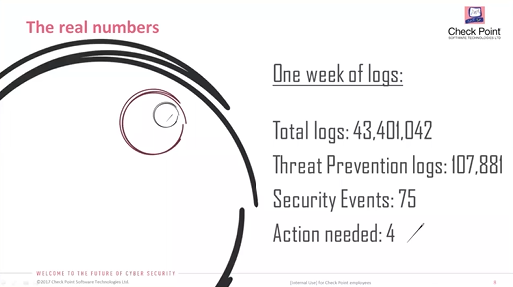
For the 107.881 Threat Prevention logs, I would like to narrow down to real advanced attacks which have been going on for the week.
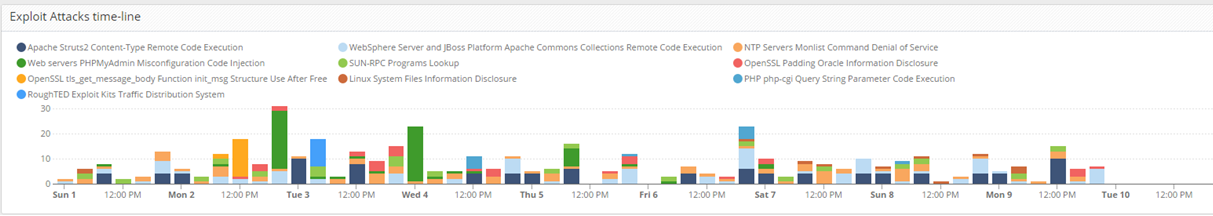
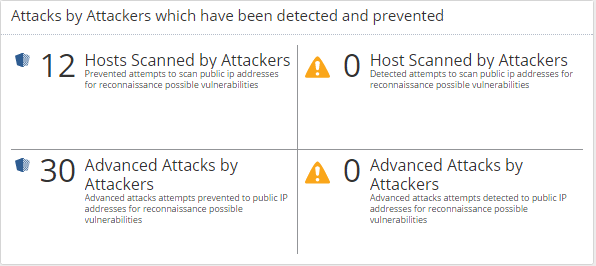
You have told in other settings that one needs to focus on the important logs. With the below SmartEvent Report with 30 advanced attack, I would like to focus on advanced exploits used for an attacks but prevented by the IPS blade, and I guess the 4 logs that needs action would be those that have been detected and possible provided access to the attacker. Like the attempt to use of using the apache struts vulnerability attack that have been used against many public Apache installation. That one is a nasty one, that gain remote access to execute commands on the apache servers
Have I misunderstood any thing here?
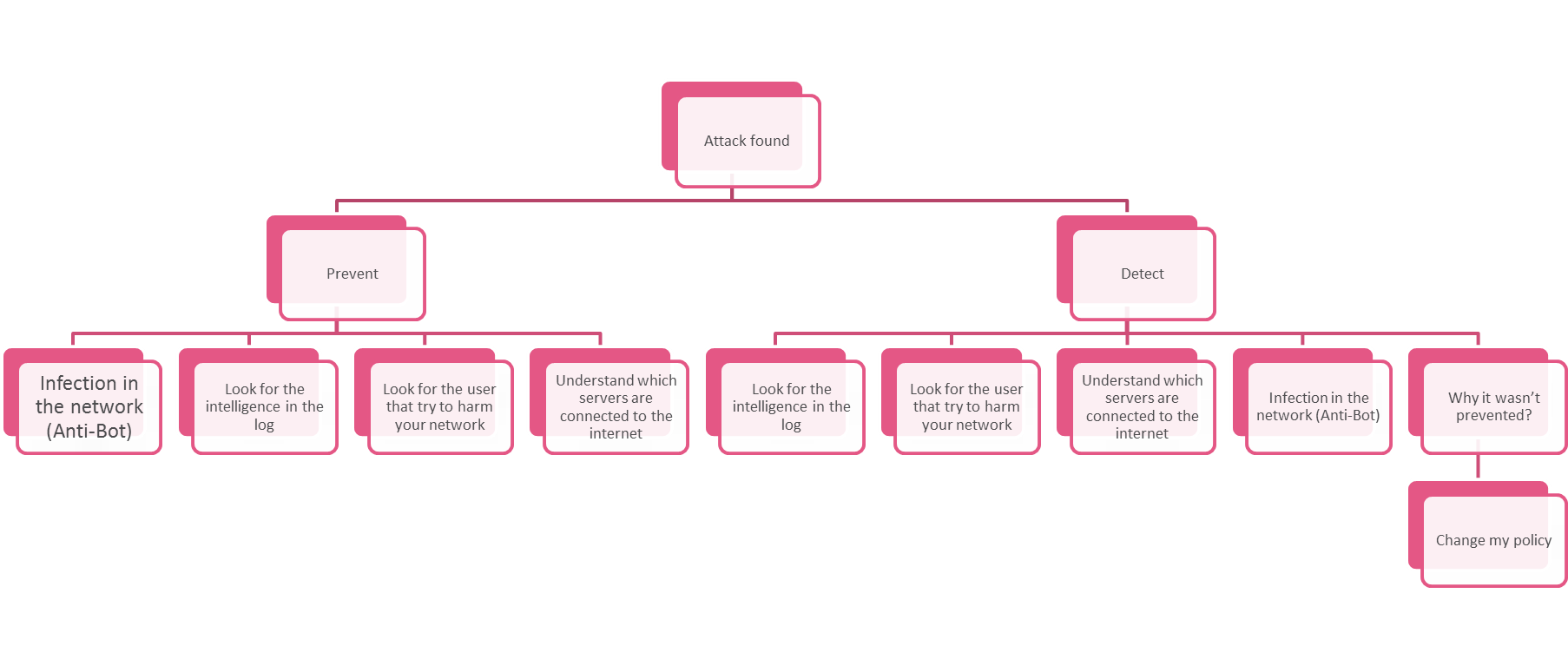
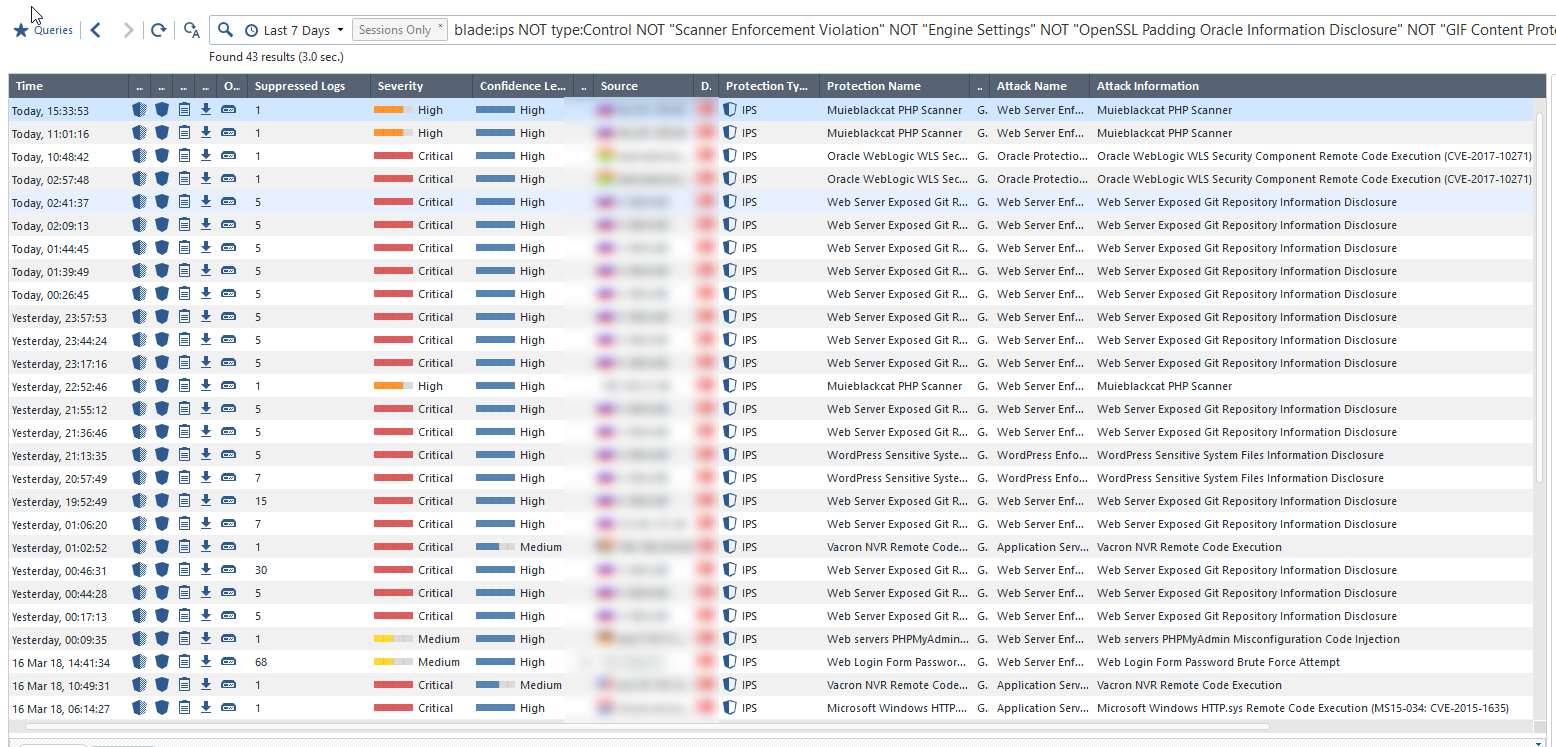
Those advanced attacks, while looking into the the following fields in SmartEvent logs.
Blade: IPS
Severity level: Medium OR High OR Critical
Confidence Level = Medium OR High OR Critical
Suppressed logs = more than 1 incident
I have tried to filter our attacks that is not generated internally to externally.
Here you see that last 7 days with different kinds of attacks from outside in.
For example I do not have any IoT presented public but still an advanced exploit other than a normal scanner like Shodan etc.
These I want to present in my SmartEvent Report. 42 advanced attack last 7 days but prevented, and none detected by IPS. But after a drill down on the report, I could see how advanced the attack have been? But will it then be the real view of reality?
I would like to generate a company threat report, without to much explanation, but still being able to see the real picture of reality.
Thanks
Kim
Best Regards
Kim