Hello Team,
Environment
2 Check Point 5900 VSX environment running R80.40 JHF 192
Management console is running on R81.10 JHF109
Issue
Need you suggestion on this issue we are facing in our environment.
We're currently running into issues while testing out AST as our new phishing simulation tool, part of the MS Defender platform.
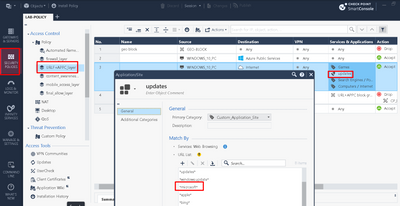
Check Point is blocking the landing page attemplate.com as potentially malicious/spyware website.
This is the global landing page for the service, as acknowledged by MS here https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/attack-simulation-train...
This URL is recently changed by Microsoft, as some tests done few weeks ago were not blocked by the firewall.
Phishing simulations are only successful if the different security elements are not blocking the simulation
The issue started some weeks ago – during initial testing of the phishing simulation, the issue did not occur. Now we see that the Application/URL filtering is blocking the access to one of the Microsoft phishing domain names and IPS flags also mark the DNS request as phishing.
See screenshots below: attempts have been made to access https://attemplate.com (see list of domains in Get started using Attack simulation training | Microsoft Learn). Microsoft is updating the list of domains used for Attack simulation training often as seen below
As Microsoft is dynamically updating the different landing page templates, is there a possibility to dynamically exclude these 'landing pages' on the Check Point environment?