- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Can't monitor secondary node over IPSec tunnel
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can't monitor secondary node over IPSec tunnel
Dear Community,
as an ISP we are monitoring our customer environments throug IPSec tunnels from our datacenter.
I don't know why, but two of our Check Point installations are strange - I cannot access the secondary node through IPSec - other sites work well with the same design. One troublemaker runs an old VRRP cluster (R77.30), the other on is a clusterXL (R80.20).
This is the general setup:
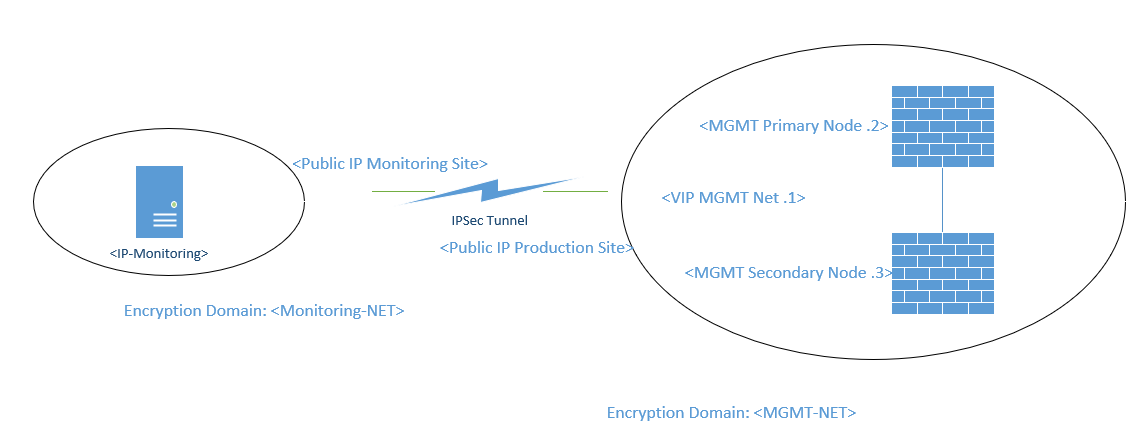
The montoring server is able to contact the MGMT VIP and node one, but obviously we need to monitor the second node as well.
The kernel param "fwha_forw_packet_to_not_active" is set to yes on both nodes, but packets are getting dropped as "received unencrypted packet...should be encrypted". I also tried to do a hide nat with a dummy ip to masquerade the access to the second node, as if it is sourced from that dummy ip - didn't work either.
I can't find the point I'm missing here - hopefully the community can help?
Best Regards
Johannes
30 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For VRRP there are 2 settings in the dash, on the cluster object, forward to cluster member and hide behind cluster IP:
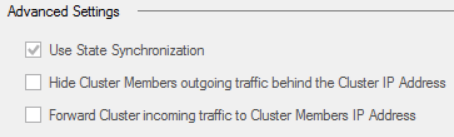
Turn them both off and these type of issues are no longer happening.
For the clusterXL double check that the correct member is dropping the traffic.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Maarten,
many thanks for your response, I wasn't aware of that VRRP setting.
But unfortunately that doesn't work, I still got this error (on the second node):
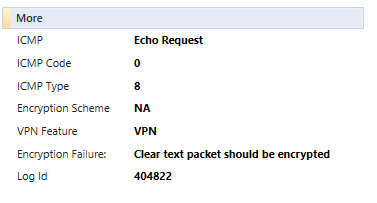
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Then you still have a problem with either that community (maybe a excluded service) or the VPN topology is not correct.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Doublechecked that.
VPN domain monitoring site: <monitoring-dmz-net>
VPN domain production site <management-net)
No natting between both of them
No excluded service in the domain.
The strange thing is, that we have working sites with the same configuration, so I'm wondering why that "unencrypted received...expected encrypted" occurs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This shows that the ping is not sent thru VPN tunnel...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can see on the interoperable ipsec device that the monitoring traffic for the primary and secondary node is sent to the tunnel.
Communication to primary node is working well, so I guess that is no routing issue.
I think the primary Checkpoint terminates the IPSec tunnel, removes the encryption (as expected) and sends the data to the secondary node with the nearest interface (in this case management interface). Somehow the secondary node expects the traffic to be encrypted anyway.
Or do you mean I need two vpn tunnels against the Checkpoints? (it's possible due to that "we-need-3-public-ips-even-if-we-use-only-one-thing")
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is no way to do this indeed, as you say the traffic is decrypted on the active node and forwarded to the backup, and dropped there because it is cleartext.
You cannot build separate tunnels to the different members.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maybe the workaround from sk106425 can help ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the suggestion, but the sk describes drops due to address spoofing, I think I have a different problem here
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The spoofing error is due to the fact that the traffic comes from the other member, as I said before, look at the incoming interface the traffic is being dropped upon.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To be honest, I don't understand what you mean/referring to.
The incoming interface for the monitoring traffic on the second node (which drops that traffic) is the management-interface with ip <mgmt-subnet>.3. Topology is defined as per ip and subnet and anti-spoofing is set to detect for that interface.
The firewall detects address spoofing, but the drop reason is due to the screenshot above.
If you really cannot monitor the hardware through vpn, we cannot recommend checkpoint products for any customer.
I don't know any other relevant firewall vendor where that issue is expected behavior (without setting options which will decrease the security) - please correct me if I'm wrong
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why not open a ticket with TAC ? Maybe here we have different # fw ctl get int fw_allow_simultaneous_ping settings, or just different routing ! Monitoring of hardware mostly uses SNMP, not ICMP...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah, I guess that is the next step.
It's the same when using snmp, but a continous ping from commandline is not that distracting for our colleagues, than having our monitoring system sending snmp requests, which result in an error state.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What I mean by the interface is that when the traffic comes through the VPN tunnel to FW1 to go to FW2, it will be sent from FW1 to FW2 over a specific interface, so when you look at the details of the log entry, what is the interface you see the traffic come in on FW2 where it is being dropped, therefore the spoofing could because it is coming in over an interface where this traffic should not be entering normally.
Lets say you use the eth6 interface for monitoring and the inteface that the VPN terminates on is eth1, you do not have the monitoring system as a network you would expect to enter on eth6, you expect that to enter on eth1, butr as fw1 decrypts the traffic and forwards it to fw2 eth6 this would not accept this traffic there and drop it on spoofing.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ah, alright - I understand what you mean.
Right, the src:<monitoring-server> was received on the <mgmt> interface on the secondary node- that could had been a problem.
I set a static route on the primary host saying dst:<secondary-mgmt>/32 interface <external>
Now the traffic is received on the secondary firewall on the <external> interface, but the error message stays the same.
I will keep you updated how the ticket ends
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So it's not possible to monitor two hardware node through an ipsec tunnel with Check Point?!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not if they are in a cluster and the tunnel terminates on the cluster. Been there.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Johannes,
I know there is was an issue with "fwha_forw_packet_to_not_active" in R80.20.
A hotfix was released today on top Jumbo Take 43.
I suggest to open a ticket to TAC and request this Hotfix:
In the description mention that you have R80.20 and fwha_forw_packet_to_not_active is not working as before, and request this Hotfix R80_20_t43_jhf_218_main.
I suspect it will solve your issue.
Thanks,
Koby
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Cool, we also encountered issues with this kernel parameter not working at some customer with R80.20.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sk147493
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is the answer to the second part of the issue, the clusterXL R88.20. Why this also occurs on the VRRP cluster R77.30 is still the question. Does this work on other VRRP R77.30 clusters ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can't tell, we only got one VRRP Cluster with R77.30 in our support
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Koby,
thanks for that suggestion, in two weeks I'm with the customer, we will try that out.
I'll keep you updated
Johannes
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Johannes,
you will need to use the kernel parameter " and in case of IPS drop (i would expect drops from IPS as the cluster is not updating it about this traffic due the info below) we need set an exception.fwha_forw_packet_to_not_active=1"
So after enable the parameter we should look in IPS logs for drops, and set an exception.
As per R&D:
Currently APPI and IPS are not supported in R80.20 with these types of connections:
- Connections from/to Standby via IPSec tunnel
- Connections to Standby that are routed via the Active member
This limitation will be lifted in a future update. Till then the workaround is to add IPS exception for connections to/from gateway’s private IPs.
I hope this info is helpful.
Thanks,
Koby
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
... or downgrade to R77.30 where "fwha_forw_packet_to_not_active" is working well (solution in place within our environment).
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Would like to share our experiences with this topic. Result is we were decided/forced to disable this "feature".
By default as per design it's not possible access standby node via IPSec, but CP implemented "fwha_forw_packet_to_not_active" which allows this and you can monitor/access standby node.
But since this time we experienced quite big issues (sporadically!) on vpn sites implemented this. Symptomts: connections get lost, regular traffic packet drops, no explanation for.
Long story short - vpn sequence numbers mishmash and gw drops packets as a out of sequence vpn attack. Regular traffic and standby node traffic index numbers are different and when arrived out of sequence frames were dropped. Quite funny as more we focused on troubleshooting or monitoring standby/primary more out of sequence and more drops...
Check your logs, bet you can find out of sequence drops as well
Outcome of CP discussions:
- First of all monitoring of standby node not supported
- if you want you can implement fwha_forw_packet_to_not_active but can cause this behavior
- works as design
- can be resolved by disable of "vpn out of sequence" attack prevention - verified
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Regarding fwha_forw_packet_to_not_active in R80.20
This is the reason why "vpn out of sequence" attack is preventing the traffic (bellow)
An update from R&D: ( they are planing to fix it )
Currently APPI and IPS are not supported in R80.20 with these types of connections:
- Connections from/to Standby via IPSec tunnel
- Connections to Standby that are routed via the Active member
This limitation will be lifted in a future update. Till then the workaround is to add IPS exception for connections to/from gateway’s private IPs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Or, if possible, change monitoring port to something very special (like tcp_43634) in order to exclude this port from VPN.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ladislav expained the topic very well, but I would like to add few words.
This not so elegant design isn't specific to R80.x at all, we had similar sporadic VPN disruptions under R77.x and the CP support explained that the standby cluster member is not supposed to send any traffic, including response packets to the VPN, at first we couldn't believe that this is being considered acceptable design, but you learn something new every day.
Such a limitation should be mentioned in VPN admin guide in capital letters and with many exclamation marks!
Any packets from the standby node addressed to any remote VPN encryption domain will trigger standby firewall to start speaking directly to the remote VPN peer and this activity is able to break existing tunnels between the remote Check Point VPN peer and the active node. Size of the impact is determined by tunnel granularity: the biggest impact is when there is single tunnel defined between the gateways and the least impact happens when there exist a SA pair for each host pair.
In the ideal world the standby node should route any traffic to remote enc domains via the active node, as it knows it is in standby state, but the existing design is different and the standby node just tries to negotiate IKE and IPSec SA-s in parallel.
As mentioned above, IPSec negotiation traffic from the standby node is detected as IPSec Replay Attack in remote CP peer and the VPN will be down for some time.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 16 | |
| 15 | |
| 7 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


