- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Blocking list of domain names (FQDN) with R80....
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Blocking list of domain names (FQDN) with R80.10
I want to block a list of domain names (example.com, google.com, customurl1.com, customurl2.com, customurl3.com, and so forth) using Checkpoint Firewall R80.10. This has proven challenging, though. I want to block the domain names from being resolved at the DNS level, even if it has no IP address assigned to it yet.
The two options appear to be to use:
- Application Control & URL Filtering
- Block domains using Domain Objects
Is there a clear-cut solution to perform what I am trying to achieve? Documentation has left me feeling unclear. I want to know what the proper approach for doing this is.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It’s a Chicken and Egg problem:
- The forward DNS (e.g. hostname.example.com > 192.0.2.1) rarely matches the reverse DNS (192.0.2.1 > not.a.valid.name)
- We don’t know every host in *.example.com
- Short of looking at the DNS request, there’s no real way to know before a the TCP connection is established whether we are connecting to somehost.example.com. Even then, this is only feasible if the gateway is between your clients and the DNS server.
A clever way to solve this problem might be to use Anti-Bot DNS Trap.
What this will do is replace lookups for the domain with a bogus IP that goes...nowhere.
This assumes Anti-Virus and/or Anti-Bot blades are enabled.
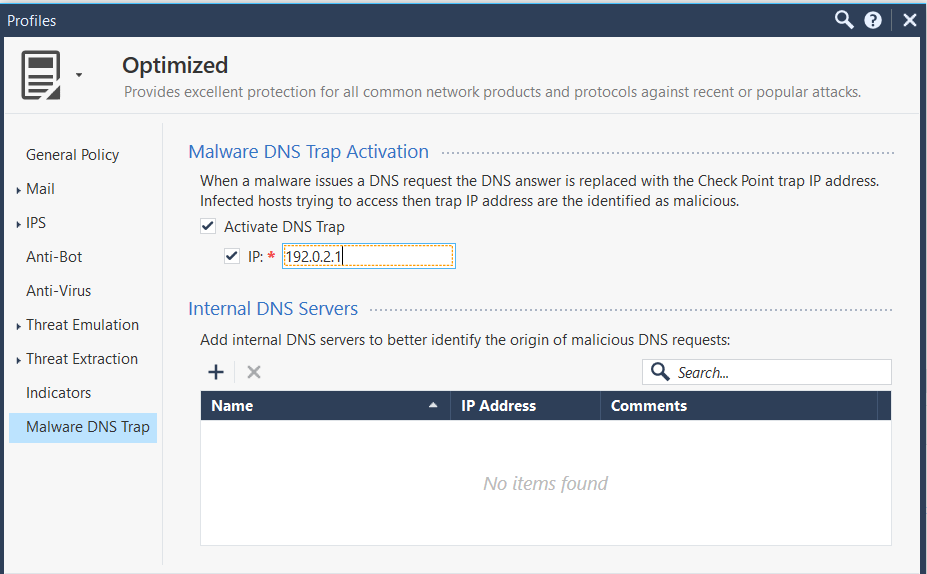
Configure this in the relevant profile:
You can create a CSV file with the relevant domains in it.
Something like:
observ1,somedomain1.com,Domain,,low,AV,Domain_to_block
observ2,somedomain2.com,Domain,,low,AV,Domain_to_block
observ3,somedomain3.com,Domain,,low,AV,Domain_to_block
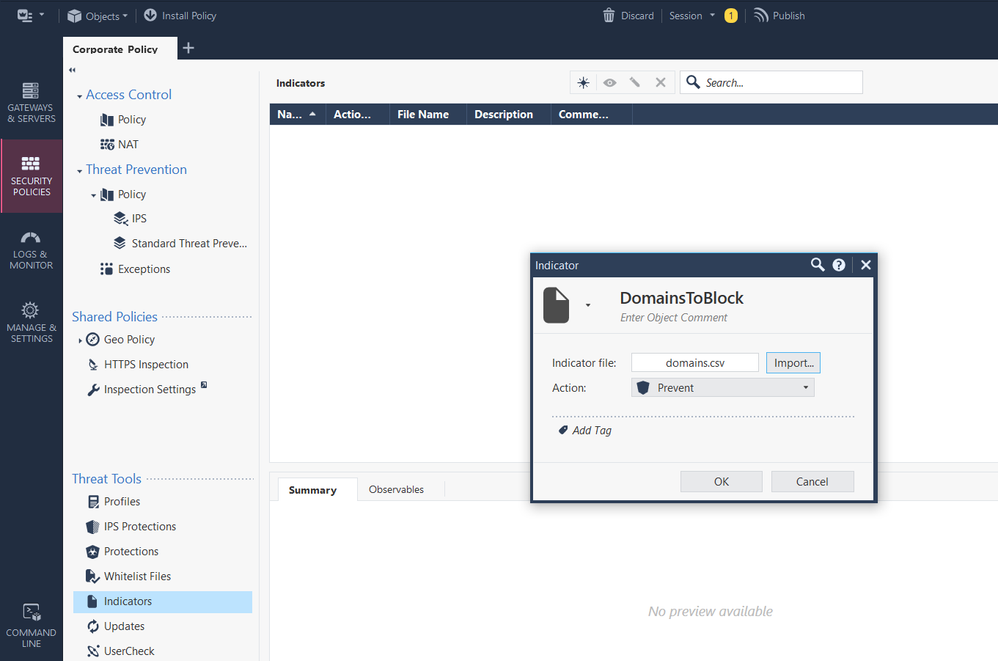
Upload it as indicators:
Install policy.
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
The basic way of doing it is like this I believe:
The only question I think is whether you want to block those very specific domains or their subdomains as well. For the first option you would need to create the domain objects in FQDN mode whereas for the second option you would need to create them in non-FQDN mode.
See sk120633 and sk90401 for more information and let us know if you are still having difficulties.
I hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Nick,
Thank you for taking the time to reply to me. I should clarify that I would block non-FQDN domains, blocking up to the first 10 layers of sub-domains. Is it only possible to achieve "blocking a list of domain names" by using Domain Objects, or are there other options available? I worry that it would not be optimal to place hundreds of domain names into a Domain Object.
Is there anyway for me to use Application Control & URL Filtering to achieving blocking a list of domain names instead?
I reviewed sk120633 and sk90401 prior to this, so I am familiar with the documentation; although, I am new to Checkpoint Firewall, so I'm taking things one step at a time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It’s a Chicken and Egg problem:
- The forward DNS (e.g. hostname.example.com > 192.0.2.1) rarely matches the reverse DNS (192.0.2.1 > not.a.valid.name)
- We don’t know every host in *.example.com
- Short of looking at the DNS request, there’s no real way to know before a the TCP connection is established whether we are connecting to somehost.example.com. Even then, this is only feasible if the gateway is between your clients and the DNS server.
A clever way to solve this problem might be to use Anti-Bot DNS Trap.
What this will do is replace lookups for the domain with a bogus IP that goes...nowhere.
This assumes Anti-Virus and/or Anti-Bot blades are enabled.
Configure this in the relevant profile:
You can create a CSV file with the relevant domains in it.
Something like:
observ1,somedomain1.com,Domain,,low,AV,Domain_to_block
observ2,somedomain2.com,Domain,,low,AV,Domain_to_block
observ3,somedomain3.com,Domain,,low,AV,Domain_to_block
Upload it as indicators:
Install policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi PhoneBoy,
Thank you for your feedback. Someone had mentioned the Anti-Bot DNS Trap solution before, but it didn't seem feasible at the time since all of the documentation and community discussion that I've read has pointed to Domain Objects. Your suggest solution sounds promising.
So, if we enable the Anti-Virus and/or Anti-Bot blades, we can enable Malware DNS Trap Activitation, point the traffic to a bogus IP, and import a list of domain names to block from a CSV? If this actually works, then this sounds perfect.
For the domains that we would like to block, would there be any performance issue if I pointed 10,000+ domain names to bogus IP addresses? What overhead could the DNS Trap solution cause, and why?
If you could answer these questions for me, I'll be very grateful! I'm sure other readers will be grateful as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you're already using IPS and/or App Control, then the performance impact will be negligible.
If you're doing Firewall only, then yes you will probably notice a performance impact.
One word of caution is that I would break up the domains into several CSVs, maybe around 1,000 entries per file, and publish after uploading each one.
This is more for the management server performance while applying the changes than anything else.
If you're doing Firewall only, then yes you will probably notice a performance impact.
One word of caution is that I would break up the domains into several CSVs, maybe around 1,000 entries per file, and publish after uploading each one.
This is more for the management server performance while applying the changes than anything else.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
PhoneBoy, again, thank you for your useful feedback.
If we are only using a Firewall, will the performance impact be comparable to what it would be if we were to use IPS and/or App Control? An explanation of the performance impact is likely the last thing that I would like to request from the community here; where does the performance impact come from?
Also, to vaguely answer Wolfgang's question, we have a custom list of domain name addresses that we want to block, even if they are not registered yet. I understand that CheckPoint maintains separate lists of threat intel feeds, but our custom list focuses on very specific targeted attacks. The list may not actually be 10,000 domain names, maybe a few thousand, but I thought that I'd be safe and use a larger number.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Anti-Bot uses the same underlying infrastructure to process the packets as IPS and App Control.
As such, I would expect the performance impact to be similar.
As such, I would expect the performance impact to be similar.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello PhoneBoy,
We have implemented the first part for the DNS Traps,
But for uploading the Domains is there a specific format for the objects,
We have our blocked domains in a CSV already and already created in the Domain.
Can we use a group? or do we have to re run the CSV and will that cause any issues with the existing domains? Are they dynamic objects or regular host? Because the example given does not look like the regular CSV object we used from the API example.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there a known upper limit to the number of blocks that can be added? Have a prospect asking for this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In this way? Not entirely sure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @PhoneBoy. Thanks for sharing this method. Do you still recommend this method for blocking domains (fqdn and non fqdn) for R80.40 (take 118) ? I basically have it how Nick mentioned above, however I am learning it may not be exactly efficient and may have unintended consequences if the domain resolves to a cloud provider (aws, etc.) Can you please show an example of the csv? Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can still use this, yes.
My answer marked as correct above has an example, and you can also find an example in the R80.40 Threat Prevention guide.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
we have an issue sending emails to specific domain and per diagnosis it was found that the issue is DNS malware trap and bogus IP. I found an article -> https://support.checkpoint.com/results/sk/sk74060
My question is should this be resolved per article documentation or should I solve this as you proposed but instead "deny" set to "accept".
Looking forward to your reply,
Klemen
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is an old enough thread that I recommend starting a new one with the relevant details to your query.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 13 | |
| 13 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter