- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Ask Check Point Threat Intelligence Anything!
October 28th, 9am ET / 3pm CET
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Behavior of the subscription blade policies after ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Behavior of the subscription blade policies after expiration
2 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The policies and rules will remain.
However, there will be no enforcement of that blade's security policy.
There is a grace period for some blades:
- IPS (for historical reasons) has a fairly complex set of rules: IPS Software Blade contracts in R71 and higher
- For App Control: How to check if a Security Gateway is covered by an Application Control Software Blade contract in U...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Looks like R81.10 Jumbo HFA 93+ has added a 90-day licensing grace period for Compliance/SmartEvent & APCL/URLF/TEX features.
|
PRJ-43895, |
Security Gateway |
NEW: We have extended the grace period of Compliance blade to support you for 90 days following contract expiration to continue providing the best security value during the renewal process. |
|
PRJ-43807, |
Application Control, URL Filtering |
NEW: We have extended the grace period of Application Control and URL Filtering blade to support you for 90 days contract expiration to continue providing the best security value during the renewal process. |
|
PRJ-44255, |
Threat Extraction |
NEW: We have extended the grace period of Threat Extraction blade to support you for 90 days following contract expiration to continue providing the best security value during the renewal process. |
|
PRJ-43910, |
SmartView |
NEW: We have extended the grace period of SmartEvent blade to support you for 90 days following contract expiration to continue providing the best security value during the renewal process. |
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
27 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Vladimir,
The enviroment will continue to work, but theses blades need of update from Check Point Cloud for download new signatures, sites categories and solutions for malwares and virus and it's only possible with a valid contract.
I hope help you.
Alisson Lima
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The policies and rules will remain.
However, there will be no enforcement of that blade's security policy.
There is a grace period for some blades:
- IPS (for historical reasons) has a fairly complex set of rules: IPS Software Blade contracts in R71 and higher
- For App Control: How to check if a Security Gateway is covered by an Application Control Software Blade contract in U...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dameon,
Will the last policy not work either?
I'm interested in Anti-Virus, Anti-Bot, URL Filtering and Anti-Spam.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, enforcement on those blades will cease once the contract expires.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello PhoneBoy,
I have a question, If my unit expired license (Application Controll and URL Filltering), Can I used object Custom Applications/Sites?. Behavior my unit expired the license (Application Controll and URL Filltering) when I use Object Custom Applications/Site? Is it possible to block the web?
Example: My unit haven't the license (Application Controll and URL Filltering), and I want block website: Facebook and youtube, can I use Custom Applications/Site ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A valid license is required per sk56300 and there is no longer a grace period without eval licenses.
FQDN/Domain objects in the access (Firewall) policy are a different option depending on the use case.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah.
Policies & Rules will work as expected but new signatures/ Updates/ Category will not be fetched for particular blades
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Since now the policy could be unified, some objects, such as "Internet" from AppC may be present.
There are also default cleanup rules in AppC and URLF policies.
If, as Dameon states, there will be no enforcement of that blade's security policy, how will the rules containing objects from those policies be processed?
Specifically, in unified not-layered cases.
Another example of concern is situation when, for example,There is a separate layer of AppC and URLF with explicit rule permitting https and ssh access, for example, to gateways, with default implicit rule set to drop.
Which rule will end-up being enforced once this subscription expired?
Will it default to all open?
Gaurav,
Please see Dameon's reply above yours: Existing protections will not continue to work after expiration of the grace period.
I.e. in case of Application control: "If a valid Application Control contract is not associated with a gateway, the blade will be disabled."
So, it is not only affecting new signatures, categories, etc...
Thank you,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Blade's relevant object defined on a layer while the blade's contract is expired will just not be matched (all blade's relevant rules will be filtered out).
E.G:
Rule 1: Src: Any Dst: Any App: Skype Action: Drop
Rule 2: Src: Any Dst: Any App: Any Action: Accept
In case Application contract is expired rule 2 will always be matched.
Hope that clears things out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, just to be clear, if you have these rules in unified policy:
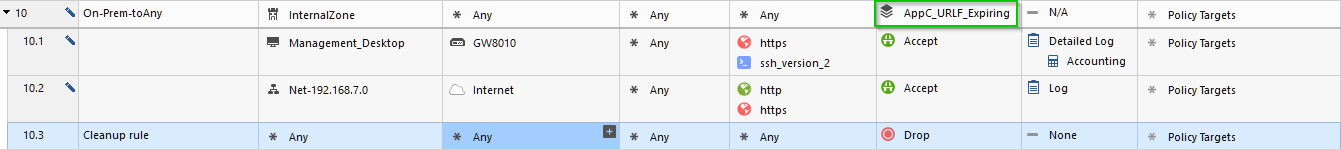
1. I will lose WebUI and SSH access to the gateway
2. I will lose Internet access from Net_192.168.7.0
And if I have it in sequentially processed App Control and URLF policy, same thing will happen, unless I have duplicate rules in Firewall policy allowing this traffic, but with "Internet" object replaced with either "All-Internet", "ExternalZone" or "Any"?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HTTP and SSH do not rely on Application Control signatures, so will not be impacted by an expired App Control license.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The inline layer in your example does not contain any application. So you will not lose internet access.
The only thing you will lose in this example is the application logs for connections matching rule 10.1.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oh ok.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please note that the inline layer shown contains single App Control and URL filtering blade.
If the blade's functionality is disabled after contract expiration, will these rules be treated as Firewall blade rules or the entire shebang will stop working?
In particular, the "Internet" object depicted is only available when the App Control is activated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
They'll be treated as firewall rules.
It's entirely possible you'll also get an error on pushing policy in this situation as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dameon.
After going through the discussion, I can understand that after the license & contract expire App Control and URL filtering blade will be disabled and as you say there will be no enforcement of that blade's security policy.
I have small query like do we able to push the policy package or we get the error and policy installation fails ?
We can only able to push the policy after disabling the rules related to specific blade ?
Regards,
Jaspal Singh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You will definitely get an error message when you push policy in this case.
However, it should allow the policy push, but the relevant rules won't work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Fellow Gentaleman's,
My MDS License & Contract will expired in this month but the VSX attached to this MDS is having license upto Dec-2019. So I have some queries regarding this issue::
1. If my MDS Contract will pass the grace period so can I able to open Smart Domain Manager or Smart Dashboard of any of my CMA after expiring the contract or not?
2. if it will open thereafter too so can I able to push the policy to the security gateways or not?
3. I think the Relevant Blades like IPS, Anti Bot, Antuvirus will not work so I will disable those blades earlier too, am i right?
4. Is there any way to take backup of the topology like details of Groups, Network Objects, Host Objects & in all whole topology before passing the grace period too., Please suggest me.
Thanks & Regards,
Saurabh/Gaurav
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Our contracts expired a few days ago, we are awaiting for the renewal PO to get pushed through now.
Thought it important to note that we are unable to install policy at all. It says the URL filtering blade has been deactivated and the policy push fails immediately. We're on the latest take of R80.30.
Unfortunately, we had a similar situation with R77.30 a few years back and were able to install policy without issue then.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's possible we've changed the grace period in more recent versions.
In any case, an evaluation license can be used to bridge the gap.
In any case, an evaluation license can be used to bridge the gap.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Seems like it. Our VAR recommended that as well, but also said they should have our renewal through today, so we decided to wait. Thanks for the quick response!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can an evaluation licensed be applied over top of an expired license though or does the OS have to be reloaded first?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes you can apply an Eval license over an expired license without reinstalling.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Only consideration is if you are running the software on open server. When you unlock the number of cores available by applying an eval licence, a reboot is required.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Looks like R81.10 Jumbo HFA 93+ has added a 90-day licensing grace period for Compliance/SmartEvent & APCL/URLF/TEX features.
|
PRJ-43895, |
Security Gateway |
NEW: We have extended the grace period of Compliance blade to support you for 90 days following contract expiration to continue providing the best security value during the renewal process. |
|
PRJ-43807, |
Application Control, URL Filtering |
NEW: We have extended the grace period of Application Control and URL Filtering blade to support you for 90 days contract expiration to continue providing the best security value during the renewal process. |
|
PRJ-44255, |
Threat Extraction |
NEW: We have extended the grace period of Threat Extraction blade to support you for 90 days following contract expiration to continue providing the best security value during the renewal process. |
|
PRJ-43910, |
SmartView |
NEW: We have extended the grace period of SmartEvent blade to support you for 90 days following contract expiration to continue providing the best security value during the renewal process. |
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good catch!
Hopefully this will also be in R80.40/R81 for those customers that need it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Look like the change is in Take 82 for R81 as well.
PRJ-43894, | Security Gateway | NEW: We have extended the grace period of Compliance blade to support you for 90 days following contract expiration to continue providing the best security value during the renewal process. |
PRJ-44254, | Threat Extraction | NEW: We have extended the grace period of Threat Extraction blade to support you for 90 days following contract expiration to continue providing the best security value during the renewal process. |
PRJ-43806, | Application Control, URL Filtering | NEW: We have extended the grace period of Application Control and URL Filtering blade to support you for 90 days following contract expiration to continue providing the best security value during the renewal process. |
PRJ-43909, | SmartView | NEW: We have extended the grace period of SmartEvent blade to support you for 90 days following contract expiration to continue providing the best security value during the renewal process. |
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 16 | |
| 6 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Wed 22 Oct 2025 @ 11:00 AM (EDT)
Firewall Uptime, Reimagined: How AIOps Simplifies Operations and Prevents OutagesTue 28 Oct 2025 @ 11:00 AM (EDT)
Under the Hood: CloudGuard Network Security for Google Cloud Network Security Integration - OverviewWed 22 Oct 2025 @ 11:00 AM (EDT)
Firewall Uptime, Reimagined: How AIOps Simplifies Operations and Prevents OutagesTue 28 Oct 2025 @ 11:00 AM (EDT)
Under the Hood: CloudGuard Network Security for Google Cloud Network Security Integration - OverviewTue 28 Oct 2025 @ 12:30 PM (EDT)
Check Point & AWS Virtual Immersion Day: Web App ProtectionAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


