- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Any tool to build a rulebase from an "Any-Any ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Any tool to build a rulebase from an "Any-Any Accept" rule?
Hello everyone,
A customer recently placed a firewall to control all inter-VLAN traffic and they unfortunately are not aware (as it usually is) what kind of traffic is generated between the VLANs as it was running through a switch until now.
We started building the rulebase depending on their necessities but I still believe that is far from ideal. To avoid any major issues we had to leave the last rule as ACCEPT. At this point, the only way seems to analyze the logs of this rule and keep adding new rules which brings me to the real question and I sincerely apologize if this is stupid but is there any quick way or a tool (I know Tufin can analyze the existing rulebase) to do this?
(I searched the forum but couldn't find any Q or A that might be directly related)
Thanks in advance,
2 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Policy Management would be the best place to put this.
The central question is: what is valid, acceptable traffic and what is not?
No tool is going to be able to tell you that.
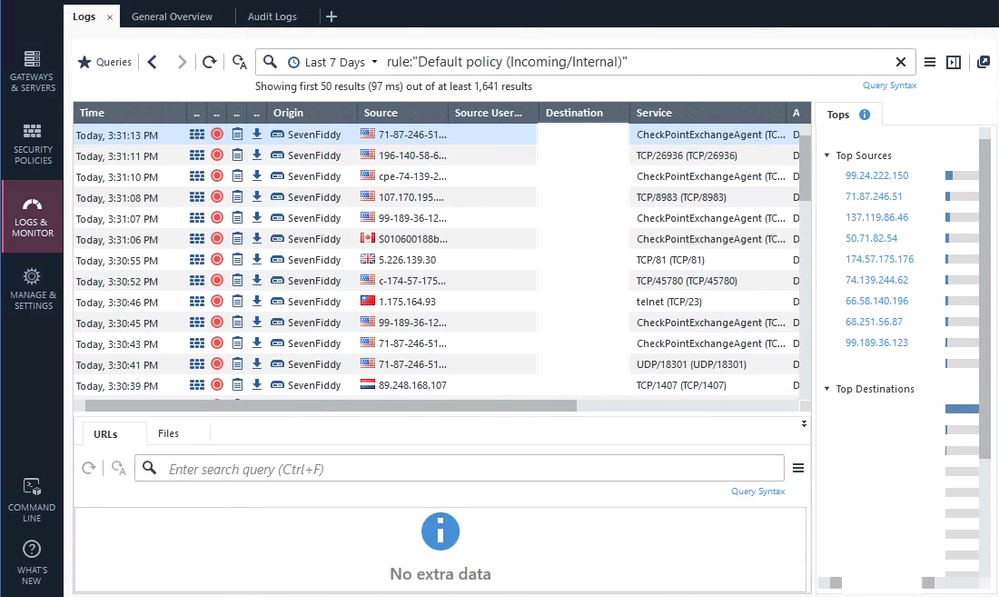
What you can do in SmartView/SmartLog is look at the top sources/destinations on this rule.
From there, you can drill down and see what is generating the most traffic and start making appropriate rules around that, perhaps after asking a few questions about what the particular host is doing and why.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is a couple of comercial tools that can help you with that: Algosec, for instance, has an optimization tool that analyzes firewalls logs and gives you proposals of rules. I guess Tufin does something similar.
The other option is a manual study of the exported logs with some other tools as Splunk or building a module with Access... Little by little you can resume the traffic.
Anyway, a Any/Any/accept rule has several problems if the TCP-out-of-state is not enable becouse logs will show even the SYN-ACK packets as being the first ones if there is some kind of assimetrical traffic. Be aware of that.
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Bekir,
My starting point would be to configure of the gateway's interfaces in monitor mode along with a SPAN port on the switch so that inter-VLAN traffic can be mirrored to the Gateway and analysed without affecting the production environment (see sk101670 for more info).
Once the traffic has been analysed over a period of time, you would then be in a better position to construct a more suited rule base.
I hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the prompt response Nick. I already have all the logs I need but it's millions of lines for even weekly traffic.
I was wondering if there's any tool (including 3rd party ones of course) to make this daunting task easier (i.e. finding patterns and making recommendations) 😃
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Bekir,
Now that your request is a bit clearer, the answer is no, I would be really surprised if such a tool exists!
In addition to what Phoneboy said, I believe you could also do the following:
- Provided that the logs can be exported in CSV format, you could start importing samples into Excel, apply a filter or a pivot table and then analyse the traffic on the basis of specific criteria such as source subnets/networks etc.
- Assuming you have captured some of the traffic involved, you could analyse it in Wireshark with the use of multiple display filters (based on say protocols).
This is what I would do anyway. I also strongly believe that this is work you would have to do with the customer as well unless you know their environment and critical services inside out. Once again though, the answer is no I'm afraid, there is no easy way to go about this.
I hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Policy Management would be the best place to put this.
The central question is: what is valid, acceptable traffic and what is not?
No tool is going to be able to tell you that.
What you can do in SmartView/SmartLog is look at the top sources/destinations on this rule.
From there, you can drill down and see what is generating the most traffic and start making appropriate rules around that, perhaps after asking a few questions about what the particular host is doing and why.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is a couple of comercial tools that can help you with that: Algosec, for instance, has an optimization tool that analyzes firewalls logs and gives you proposals of rules. I guess Tufin does something similar.
The other option is a manual study of the exported logs with some other tools as Splunk or building a module with Access... Little by little you can resume the traffic.
Anyway, a Any/Any/accept rule has several problems if the TCP-out-of-state is not enable becouse logs will show even the SYN-ACK packets as being the first ones if there is some kind of assimetrical traffic. Be aware of that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great advices all around, thank you everyone. Especially Phoneboy and Jose 😃
I'm aware that I shouldn't be "allowing" all traffic but the customer will be deciding everything at the end of the day.
I already started analyzing the traffic with the help of Tufin and building a rulebase on its proposals, mostly based on subnets but I will come back to them and change into more restricted rules. And final step will be changing the last rule to drop and add additional rules if we experience any major issues / outages.
Thank you again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Community,
I need to do similar task - generate rules from overly permissive "any any accept" policy. Many years ago I used Tufin APG for similar task. Since there is no Tufin in this enviroment decided to look around.
There is a perl tool "360-FAAR Firewall Analysis Audit Repair" i'm considering to try before trying Excel and pivot tables.
as per read-me in https://sourceforge.net/projects/faar/files/
* Build new rulebases from scratch with a single 'any' rule and log files.
# Currently supported input firewall log types are:
# - Checkpoint Firewall-1: logexport utility format,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Sergej,
I will definitely be looking into this one as it seems to cover a lot of ground for security engineering task. Thanks for sharing it 😃
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Bekir,
I too have had this need several times, and without the funding for commercial tools, it can seem like an enormous task. What I have found is that you can segment the rule base instantly based on traffic flow direction with an accept and log rule. You can this massively cuts down the hits on 1 single rule and makes the task somewhat "easier".
For example, lets assume you have 2 networks.
- DMZ (10.10.10.0/24)
- Internal Server Network (10.10.30.0/24)
Instead of having your any any any rule solely in place, you could create the following rules above your global any.
Rule 1
Source: DMZ (10.10.10.0/24)
Destination: Server Network (10.10.30.0/24)
Service(s): Any
Action: Accept
Rule 2:
Source: Server Network (10.10.30.0/24)
Destination: DMZ (10.10.10.0/24)
Service(s): Any
Action: Accept
Log: Yes
You would then perform analysis on each of the rules independently and start to create your actual required rules above these more specific rules.
You should then see that your original ANY rule should start to get less and less hits until the point where you can change your action to drop as a global cleanup rule.
For the actual analysis we use CSV export from SmartView (web version of SmartLog) and then perform unique flow filtering within Excel. This shows us all unique connections seen over a time period, we can then validate the connection then create as required.
I would also look at connections that give a lot of noise that the firewall may see, Broadcast, multicast etc, validate those connections and if not required, drop them without logging. This will remove a lot of garbage from your outputs.
I hope that I have explained this OK, if not let me know and I will elaborate further.
Regards
Mark
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Mark,
This was also the method I used and then the customer decided to get Tufin which made things much more easier.
But again not every customer has the budget to do so and this seems to be the most practical way for an otherwise daunting task.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 15 | |
| 8 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter