Hello together
On many Labs as well for the CSSA Lab i have seen the configuration Example that allways onyl one Nework is connected to a seperate Interface on the Firewall like the following Example.
Vlan 2 Network 10.2.1.0/24 default Gateway ist 10.2.1.254 Interface G0/1 on Firewall (DMZ1)
Vlan 3 Network 10.3.1.0/24 default Gateway ist 10.3.1.254 Interface G0/2 on Firewall (DMZ2)
Vlan 10 Network 10.10.1.0/24 default Gateway ist 10.10.1.254 Interface G0/0 on Firewall (Management)
The Physical Eviorment is a PC who have 8x Networks Port on it, (using Vmware Worksation, with Hostbased Connection to the Layer 3 Switch, ever Port is on a seperate Vlan, like VLAN2, 3 and 10.
The default Route on the Firewall is 0.0.0.0 0.0.0.0 to 192.168.1.1 Interface Outside Address from the ISP.
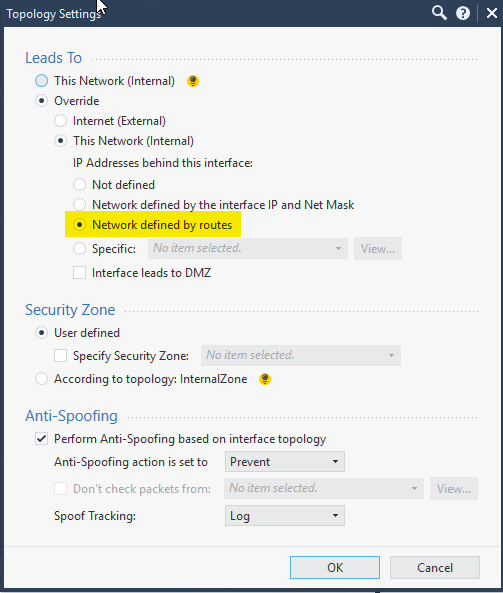
If I rember well until Anti Spoofing is enabled on the Managment Interface of the FIrewall he will only acept Traffic from this Network in this Exapmle 10.10.1.0/24 and not from the other Networks like 10.2.1.0/24 and 10.3.1.0/24.
No Traffic will go to the Internet or between the DMZ Networks, as well Antispoofing is disabel on the other Interaces.
On my Laver 3 Switch I have configure all SVI (Switch Virtuel Interfaces ) with x.x.x.253/24 who have a default Route to Managment Interface of the Firewall.
Maybe the Picture 1 on the Attachment explane the Situation easyer.
What is now the Question.
Can the Traffic only pass when Anispoffing is disable beween the DMZ and Managment Interfaces ?
Or is the Traffic blocked until the Objects (Networks) and Policys are in place?
Best regards
Alexander