- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Anonymizer matches all traffic
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Anonymizer matches all traffic
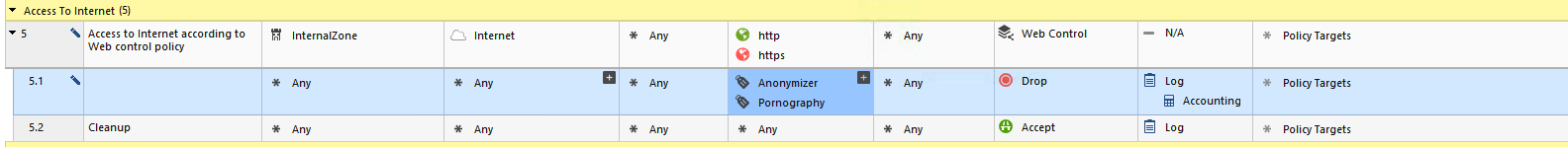
I am a bit struggling with an Anonymizer drop Rule. A rule basically like this
internal to external Anonymizer drop
This rule matches any traffic from inside to outside. This rule starts to create 'accept' logs. The accept logs are logs were Application Control was not able to finish Application classification because of insufficient data transmitted. This is also happening for traffic that should be dropped by the cleanup rule.
Does Check Point really accept / forward packets until the Classification did finish or not finish, even the traffic should be dropped by another Rule below this "internal to external Anonymizer drop" Rule (like the clean up rule).
The Anonymizer App Group matches TCP Port 1-65535 and UDP 1-65535. I think this is the reason it matches "almost" all my traffic from inside to external. But i don't like it when the Firewall Accepts Traffic until the classification is done for Traffic that should be dropped by the cleanup Rule.
Can I do something against that?
Regards
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your answer.
I think i can solve this problem with a rule selecting http and https and then add an inline layer with the Anonymizer category. I think that way i can avoid that Anonymizer is matching all traffic from inside to outside (only 80 and 443 is affected by the Anonymizer Rule).
6 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To match against an application layer (or content) GW needs application information.
There are cases where all application rules may be filtered out due to other columns or objects (source\destination\service) - on such cases the match can be done without the application information.
To gather application information GW needs to inspect connection data (i.e: TCP\UDP payload). If data does not exist (for optimization reasons browsers often opens empty TCP connection or empty SSL tunnels) GW will end in an "insufficient data" state.
Note that on cases where all potential rules (determined according to all none data dependent columns\objects) are drop rules connection will be dropped without inspecting the connection to determine application matched on the connection.
Regarding your specific problem. I do not have the full picture of your rulebase.
You can try changing anonymizer and cleanup rule to be with a drop rule without usercheck action (on such cases above drop logic should be applied).
Another option is to customize services of Anonymizer category to be more specific (e.g: web services).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your answer.
I think i can solve this problem with a rule selecting http and https and then add an inline layer with the Anonymizer category. I think that way i can avoid that Anonymizer is matching all traffic from inside to outside (only 80 and 443 is affected by the Anonymizer Rule).

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, this is definitely an approach you can take and an excellent use case for inline layers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Benjamin, just to be clear, the Accept logs didn't happen on the drop rule, but on one of the accept rules below it, correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
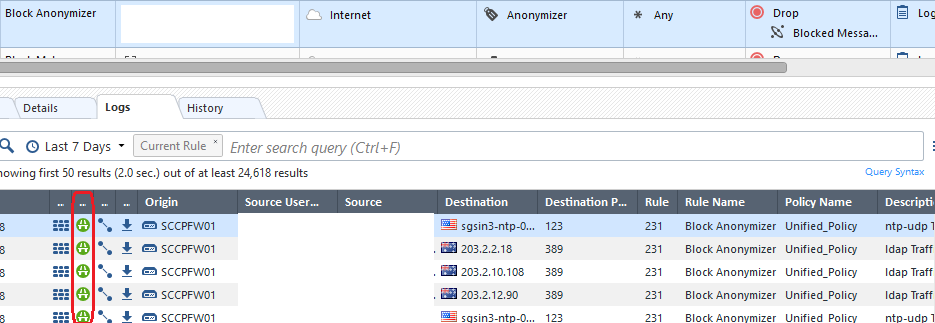
In the initial example without the inline layer. The rule "internal to external Anonymizer drop" starts creating 'accept' logs event it's a drop Rule. This is because the Anonymizer category matches all TCP/UDP and the Firewall tries to match an Application against the Traffic. All the accept logs are because of unfinished Application mappings (e.g. insufficient data to match an Application). This happens no matter if the traffic should be dropped by another Rule below the "internal to external Anonymizer drop" Rule.
In the second example with an inline layer. I select the traffic and then i apply the Anonymizer drop Rule within the Layer. Like this i can avoid that ALL traffic is inspected for Anonymizer Applications.
I hope it's a bit more clear now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I found this issue too.
need to filter logging without accept action.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 16 | |
| 8 | |
| 6 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


