Hello Community,
I'm writing to ask for a question regarding Mobile Access login and logout events.
The main objective is to retrieve login and logout events for all VPN client users and the VPN client version. I understand the "logout" event could have multiple reasons: session timeout, manual disconnection (by end-user).
Environment Description
- Check Point R80.20 Take 80 (1 VM Security Managements and 2 physical cluster nodes - Open Server)
- LDAP authentication
- VPN client: Check Point Remote Access VPN client (Windows) - product: Check Point Mobile

- Log Generation: per Connection
I started to looking at login events in SmartConsole logs but I found a "strange" behavior for some users, sometimes.
Example 1
- Filter: blade:("Mobile access") AND action:"Log In" and User01
- Time range: yesterday (2020-05-14)
As you can notice by results, there is only one login event related to User01 matching the filter (I removed some parts for privacy - see the attached screenshot 01-User01 login events - SmartConsole Log.png):
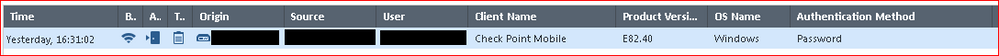
Now the User01 connected to VPN in the afternoon (16:31) but also in the morning (!!!) at 08:35 (+/-), but there is no trace in the log. I tried to modify the filter including the Identity Awareness blade too:
- Filter: blade:("Mobile access" or "Identity Awareness") AND action:"Log In" and User01
- Time range: yesterday (2020-05-13)
This time I get more results (see the attached screenshot 02-User01 login events - SmartConsole Log.png):

The user authenticated at 08:36 in Active Directory (because connected to VPN).
If I change the time range for the same user (today - 2020-05-14) I found expected login entries for Mobile Access blade (see the attached screenshot 03-User01 login events - SmartConsole Log.png):

Question: WHY, sometimes, for some users, I have no trace for Mobile Access blade ?
Example 2
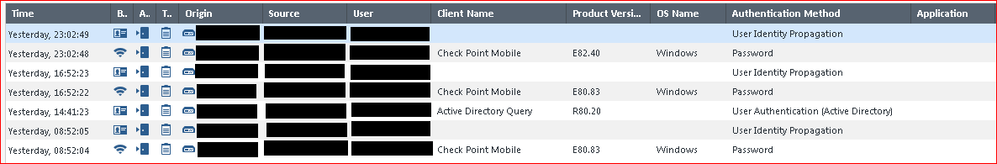
If I search for another user User02 (mine) it is working as expected: I notice three entries related to logins: one for blade Mobile Access and the other two for Identity Awareness (see the attached screenshot 04-User02 login events - SmartConsole Log.png):
- Filter: blade:("Mobile access" or "Identity Awareness") AND action:"Log In" and User02
- Time range: yesterday (2020-05-14)
Please, can you give me your opinion ?
Thank you,
Luca







