- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: should i be worried about a key install to an ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
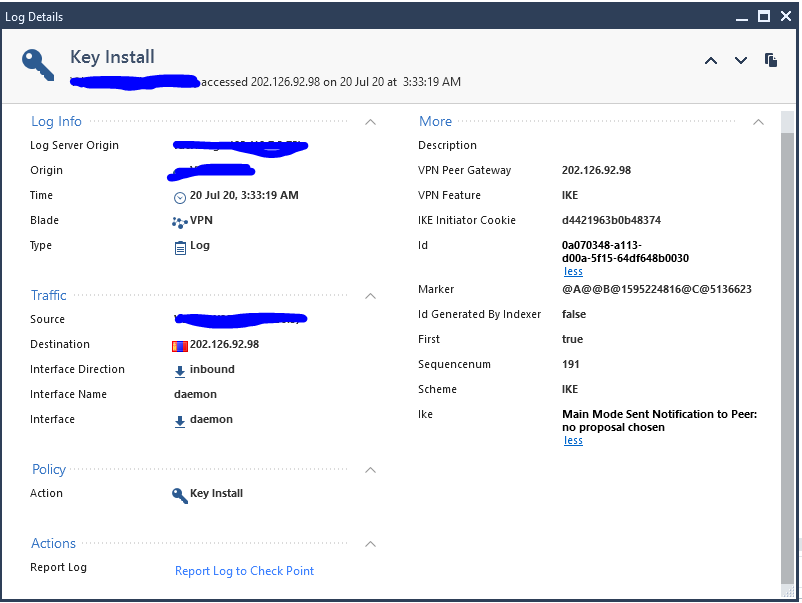
should i be worried about a key install to an unknown ip from the firewall?
So we had 2 vpn key installs that were successful from the same firewall to different ips (one from mongolia and one from china), should i be worried about that? because all i see in the logs are just the key installs so just 2 logs and no other logs, no exchange of information to those ips,etc. Do i have to investigate something else?
That is how the log looks like, the other key install is also the same but with a different destination ip.
Thanks and Regards.
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You’ll notice it also says “No Proposal Chosen.”
Which means no key was actually installed.
This could be a configuration error on the remote end but I suppose it could also be a reconnaissance attempt by a remote party (portscan or similar).
Something to keep an eye on for sure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
what does it mean " key install " ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's when symmetric encryption keys are (attempted to be) negotiated between VPN peers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This has been brought up before at CheckMates, basically all UDP 500 traffic is allowed by the firewall and sent to the process vpnd on the gateway which is where all IKE negotiations occur. You'll see random Internet IPs trying to start IKE negotiations with a "Key Install" log but they won't get anywhere since they are not a defined peer.
IKEv1 Phase 1 does things in kind of a messed up order of operations by design which is not Check Point's fault. IKEv1 Phase 1 performs the following three tasks in this order:
- Agree on algorithms to form an SA
- Compute a secret key with Diffie-Hellman
- Authenticate the negotiating peers
The fact that lots of negotiation and a computationally expensive Diffie-Hellman calculation is performed before the peers even authenticate each other should raise alarm bells. Because the peer has not been authenticated yet, it always possible they are hostile and trying to crash us with malformed or otherwise corrupt negotiations. For that reason all IKE is handled in the vpnd process instead of the INSPECT/Firewall Worker which traditionally runs in the kernel. If the vpnd process happens to crash, its parent process fwd simply respawns it immediately, no harm no foul. However if IKE negotiations took place inside the kernel, a crash caused by the peer in there would cause the whole system to crash. With the advent of USFW, it will be interesting to see if functions like this that are done for stability reasons in separate processes will end up getting integrated into the INSPECT/fwk/Firewall Worker when USFW is enabled.
IKEv2 resolves this design issue by authenticating the peers first before allowing any other operations.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I am documenting Key Install referenced in Harmony Connect logs. Basically, this is one of the reasons for unsuccessful connection between the SD-WAN device and Harmony Connect Secure Web Gateway. Could anyone please explain in simple terms what Key Install is?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe it relates to when the IKE SAs are successfully negotiated between VPN peers (ie they have negotiated their symmetric key used for bulk encryption).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello! could I ask you. how I can block all this unwanted "key installs" from particular ip addresses or networks or countries?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
if you are not using implied rules you just can make a firewall rule. In this firewall rule block ESP (50) and Ike (500). And and make rule that allows the traffic from trused public IP's (remote VPN endpoints)
-------
Please press "Accept as Solution" if my post solved it 🙂
Please press "Accept as Solution" if my post solved it 🙂
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 12 | |
| 10 | |
| 9 | |
| 8 | |
| 6 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter