Hi all,
I'm playing with R80.20 GA in my LAB (which is in fact running on my laptop using VirtualBox) and I'm setting up a IPSec VPN between 2 Security Gateways.
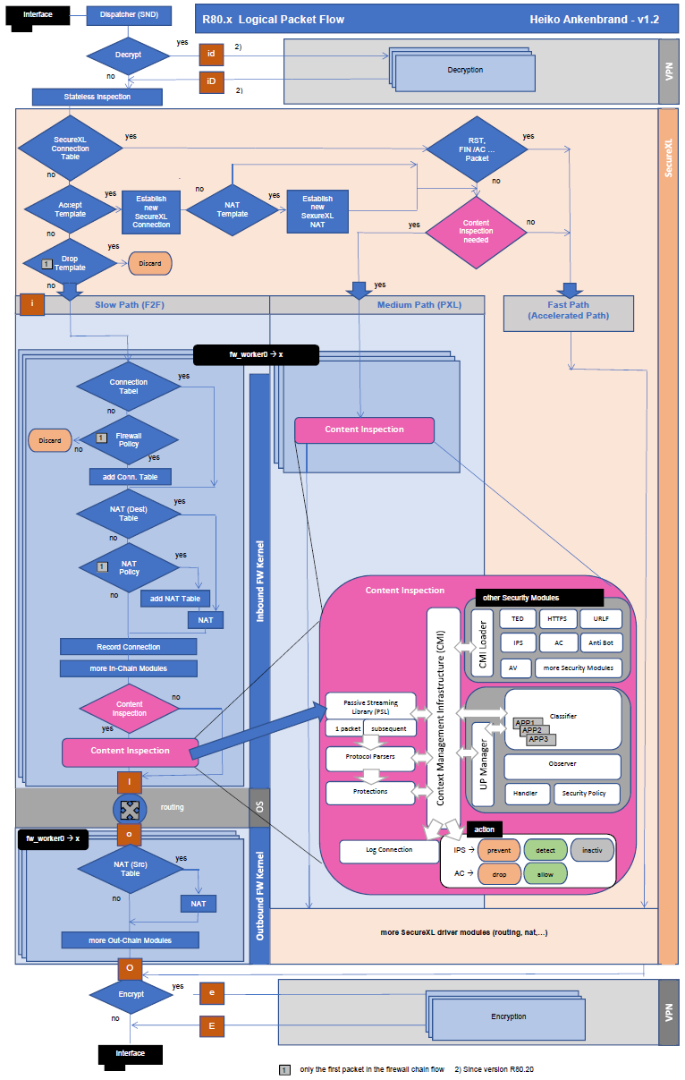
When I'm watching the traffic with fw monitor I do not see the inspection points we were used to since R80.10 (see fw monitor inspection point e or E for more information).
My LAB looks like this:
Local gateway: 192.168.202.80
Peer: 192.168.202.90
Local VPN Domain: 192.168.3.0/24
Remote VPN Domain: 192.168.2.0/24
I'm initiating SSH traffic from 192.168.3.100 to 192.168.2.2 which does enter the IPSec VPN. The SSH connection does work fine.
However, I see these "inspection points" with fw monitor: id, ID, o , O and OE on the local gateway where the SSH client resides in a directly connected network (eth2).
FYI, SecureXL was still enabled when fw monitor was started.
[Expert@GW2:0]# fw monitor -e 'accept (host(192.168.3.100) and host(192.168.2.2)) or esp;'
monitor: getting filter (from command line)
monitor: compiling
monitorfilter:
Compiled OK.
monitor: loading
monitor: monitoring (control-C to stop)
[vs_0][fw_0] eth2:id[52]: 192.168.3.100 -> 192.168.2.2 (TCP) len=52 id=24338
TCP: 50393 -> 22 .S.... seq=71548dfe ack=00000000
[vs_0][fw_0] eth2:ID[52]: 192.168.3.100 -> 192.168.2.2 (TCP) len=52 id=24338
TCP: 50393 -> 22 .S.... seq=71548dfe ack=00000000
[vs_0][fw_0] eth1:o[52]: 192.168.3.100 -> 192.168.2.2 (TCP) len=52 id=24338
TCP: 50393 -> 22 .S.... seq=71548dfe ack=00000000
[vs_0][fw_0] eth1:O[52]: 192.168.3.100 -> 192.168.2.2 (TCP) len=52 id=24338
TCP: 50393 -> 22 .S.... seq=71548dfe ack=00000000
[vs_0][fw_1] eth1:O[52]: 192.168.3.100 -> 192.168.2.2 (TCP) len=52 id=24338
TCP: 50393 -> 22 .S.... seq=71548dfe ack=00000000
[vs_0][fw_1] eth1:OE[124]: 192.168.202.80 -> 192.168.202.90 (50) len=124 id=7404
[vs_0][fw_1] eth1:id[124]: 192.168.202.90 -> 192.168.202.80 (50) len=124 id=33122
[vs_0][fw_0] eth1:id[52]: 192.168.2.2 -> 192.168.3.100 (TCP) len=52 id=0
TCP: 22 -> 50393 .S..A. seq=2a72dd30 ack=71548dff
[vs_0][fw_0] eth1:ID[52]: 192.168.2.2 -> 192.168.3.100 (TCP) len=52 id=0
TCP: 22 -> 50393 .S..A. seq=2a72dd30 ack=71548dff
[vs_0][fw_0] eth2:o[52]: 192.168.2.2 -> 192.168.3.100 (TCP) len=52 id=0
TCP: 22 -> 50393 .S..A. seq=2a72dd30 ack=71548dff
[vs_0][fw_0] eth2:O[52]: 192.168.2.2 -> 192.168.3.100 (TCP) len=52 id=0
TCP: 22 -> 50393 .S..A. seq=2a72dd30 ack=71548dff
[vs_0][fw_0] eth2:id[40]: 192.168.3.100 -> 192.168.2.2 (TCP) len=40 id=24339
TCP: 50393 -> 22 ....A. seq=71548dff ack=2a72dd31
[vs_0][fw_0] eth2:ID[40]: 192.168.3.100 -> 192.168.2.2 (TCP) len=40 id=24339
TCP: 50393 -> 22 ....A. seq=71548dff ack=2a72dd31
[vs_0][fw_0] eth1:o[40]: 192.168.3.100 -> 192.168.2.2 (TCP) len=40 id=24339
TCP: 50393 -> 22 ....A. seq=71548dff ack=2a72dd31
[vs_0][fw_0] eth1:O[40]: 192.168.3.100 -> 192.168.2.2 (TCP) len=40 id=24339
TCP: 50393 -> 22 ....A. seq=71548dff ack=2a72dd31
[vs_0][fw_1] eth1:O[40]: 192.168.3.100 -> 192.168.2.2 (TCP) len=40 id=24339
TCP: 50393 -> 22 ....A. seq=71548dff ack=2a72dd31
[vs_0][fw_1] eth1:OE[108]: 192.168.202.80 -> 192.168.202.90 (50) len=108 id=60012
[vs_0][fw_1] eth1:id[140]: 192.168.202.90 -> 192.168.202.80 (50) len=140 id=5328
A similar test when traffic is not sent into a VPN I see: id, ID, o and O.
Two questions:
- Do you see this too on your R80.20 GA environment?
- Can someone explain id, ID and OE?
My blog: https://checkpoint.engineer