- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- The difference of bridge-ha soft failover
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The difference of bridge-ha soft failover
Dear
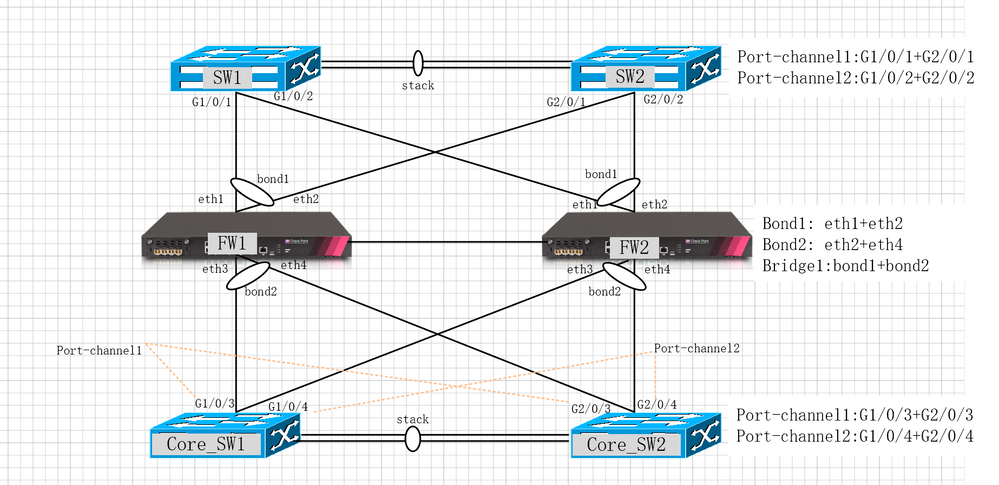
Pls see the screenshot:
I have a failover question,as below:
Before:
The bridge ha system version are R80.10,I did failover test with command "clusterXL_admin down; clusterXL_admin up",everything is ok,business traffic is working when failover active to FW2.
After:
I upgrade R80.10 to R80.40,then did failover test with command "clusterXL_admin down; clusterXL_admin up",after active faiover to FW2,business traffic interruption, i see the arp and mac table in switch ,i found arp and mac table out interface no flush,so the traffic interruption.
For example: I use source ip 1.1.1.1 under core_sw to ping dest 1.1.1.2 above (sw1&sw2).When fw1 is active,core_sw1&sw2 disply the 1.1.1.2 arp and mac out interface is port-channel1,but i failover active to fw2 with command "clusterXL_admin down; clusterXL_admin up",i see the 1.1.1.2 arp and mac out interface still is port-channel1,so traffic interruption.
The same environment of R80.10 and R80.40 ,just upgrade R80.10 to R80.40,R80.10 failover ok,but R80.40 failover not working,I want to know the difference between R80.10 and R80.40.
I also have the same problem in R80.30. I comfirm that R77.30 and R80.10 is working.
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What JHF level for R80.40?
There are many, many differences between R80.10 and R80.40, most of which are probably not relevant to this issue.
First, I recommend checking this with the latest GA JHF installed, if only because I see a couple fixes related to bonds and/or Layer 2 configurations.
If it still doesn't work, I recommend a TAC case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.10 JHF 155
R80.40 Latest JHF
the same problem in R80.30, JHF 196
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Use Virtual MAC. No need to clear arp tables on switches to make the traffic flow continue to work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If using the Virtual MAC option, be sure that portfast is set on all switchports where the firewall is connected, as I've seen STP get upset about seeing that VMAC on more than one switchport (even if just briefly) which can cause what I call a 10-12 second "slow" failover in my book. Note that enabling portfast is NOT the same thing as disabling STP entirely which you should never do...
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
vmac is not working(according to my test) and nothing to do with vmac(bridge mode ha).switch arp&mac table have out interface,when failover,arp&mac table out interface no change,for example:
Before failover,the arp table as follow:
mac IP Interface
12:34:ed:56:78:23 1.1.1.2 port-channel1
After failover,the arp table should as follow:
mac IP Interface
12:34:ed:56:78:23 1.1.1.2 port-channel2
but after failover,the arp table still as follow:
mac IP Interface
12:34:ed:56:78:23 1.1.1.2 port-channel1
so the traffic interruption.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
This is Known Limitations since R80.30 Kernel 3.10
This is listed in sk166717
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Yair_Shahar Are you talking about this:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks,But i think it is nothing to do with this.
It said that connections do not survive failover,i think it refers to connections synchronize between ha device.
in my environment,after failover,arp&mac out interface no change,so traffic interruption,did not reach the firewall.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tac tell me that i should change firewall bond from 802.3ad mode to A/B mode.
I need to verify it in my lab.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Jeff,
The root cause of this issue reside on the missing of shadow_table (mac table) in the FW.
This means upon a failover cluster does not send updates to its broadcast domain, this affect the switches which does not update its mac address table with new ports.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Yair_Shahar Yes,you are right. but i want to know why r80.10 is working well and r80.30&r80.40 not working,what are the difference.I am very confused,I met more than once
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The origin of this issue reside on kernel 3.10.
so all releases which have kernel 2.6 have this functionality working.
Yair
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I encountered this problem for the first time on,system version R80.30,kernel 2.6
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK - This will require investigation not related to what I mentioned for kernel 3.10.
In general, you should see updates coming out from the new Active Member toward the network.
Look on 'fw tab –t fdb_shadow –f' it should include mac address it learns.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 11 | |
| 9 | |
| 9 | |
| 8 | |
| 6 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter